Big data access control management system and method
A management system and management method technology, applied in the big data access control management system and its management field, can solve the problems that security cannot be effectively and timely protected, the reliability is not high, and it is useless, so as to avoid congestion, improve effectiveness, The effect of ensuring life safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
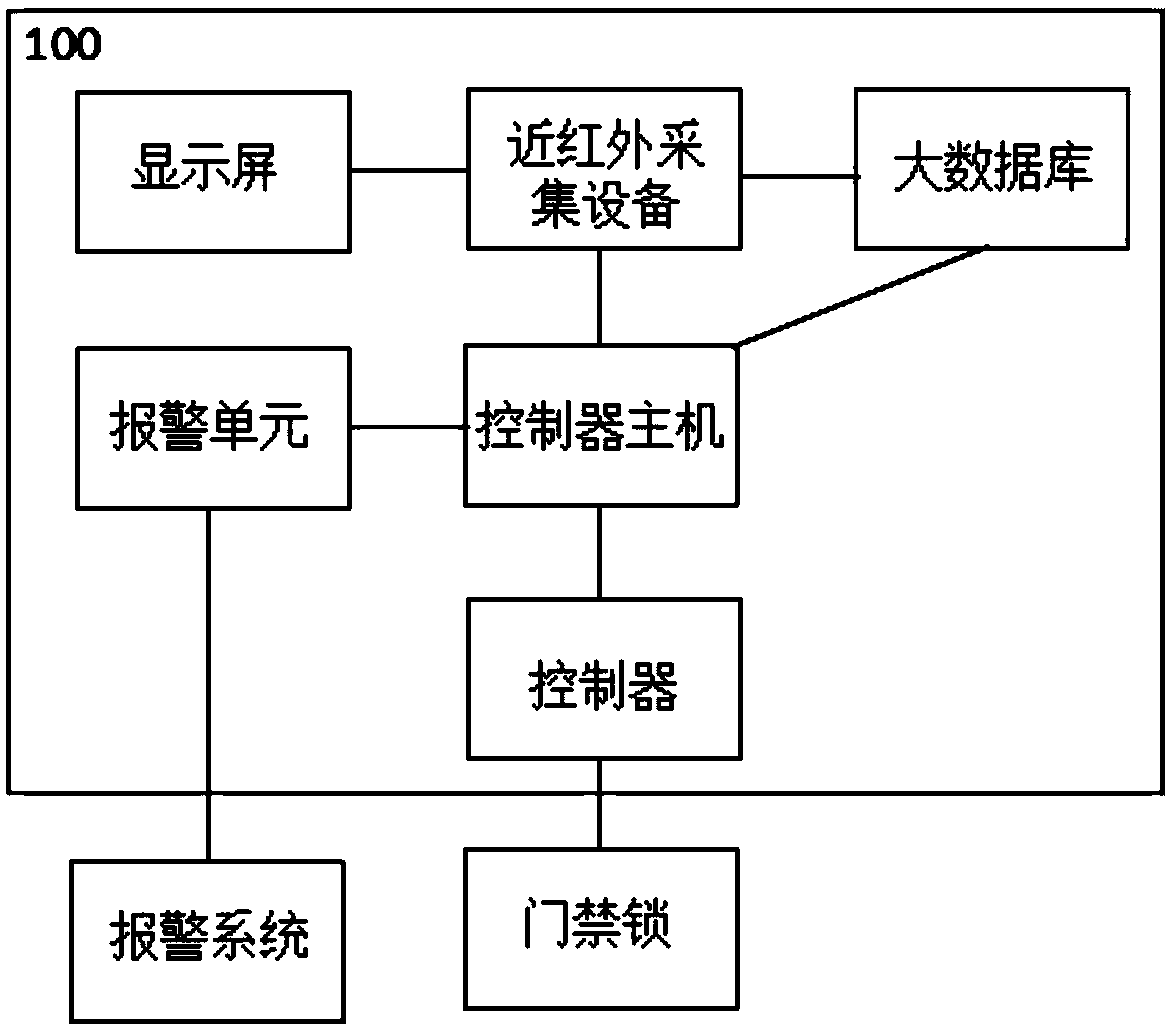
[0046] A kind of big data access control management system 100, such as figure 1 As shown, it includes: display screen, near-infrared acquisition equipment, controller host, alarm unit, and controller.
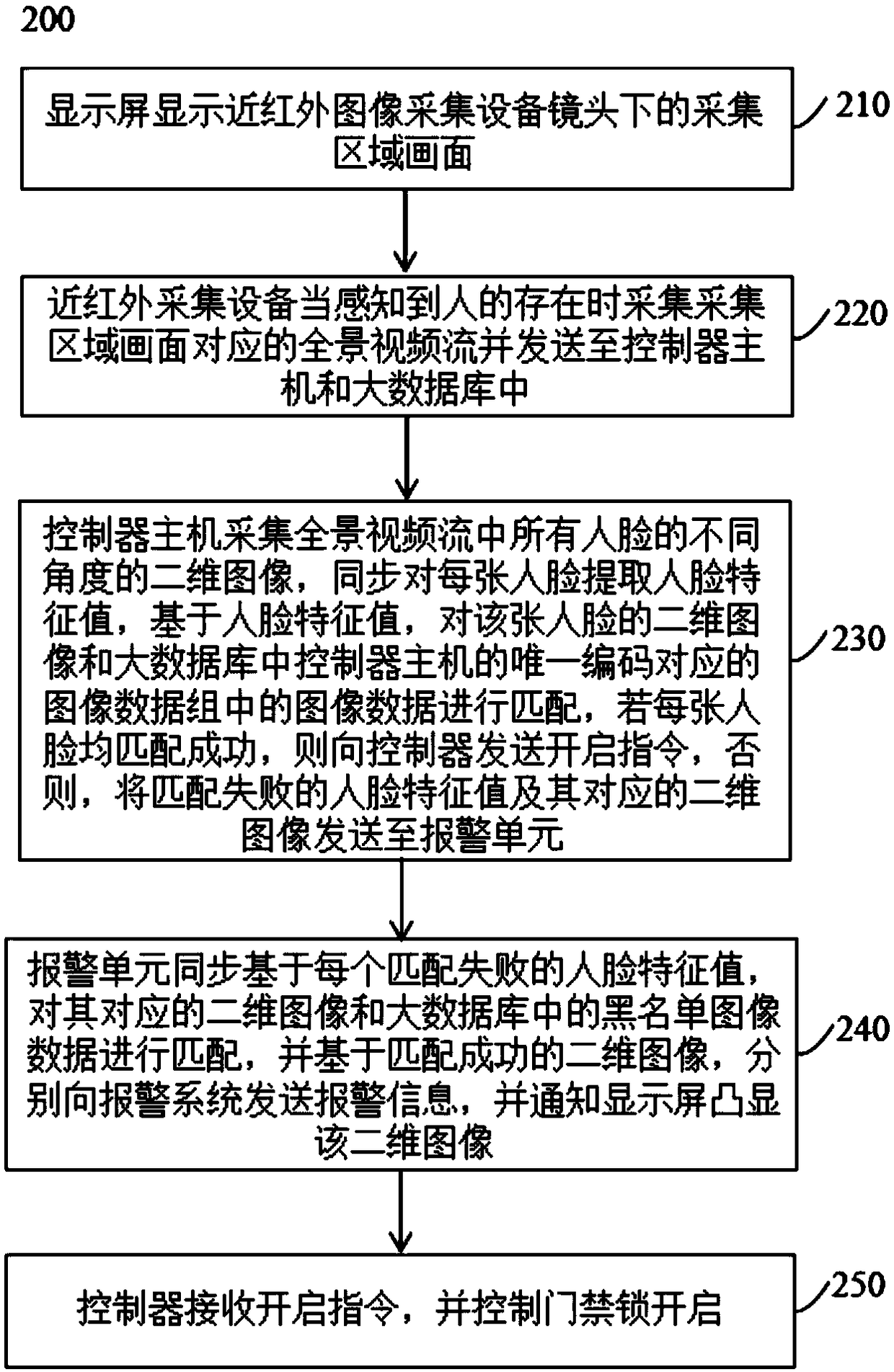
[0047] The display screen is used to display the image of the acquisition area under the lens of the near-infrared image acquisition device; the near-infrared acquisition device is used to collect the panoramic video stream corresponding to the image of the acquisition area when the presence of a person is sensed and send it to the controller host and the large database; The controller host is used to collect two-dimensional images of different angles of all faces in the panoramic video stream, and simultaneously extracts facial feature values for each face, and based on the facial feature values, the two-dimensional image of the face Match the image data in the image data group corresponding to the unique code of the controller mainframe in the large database. If each face ...
Embodiment 2
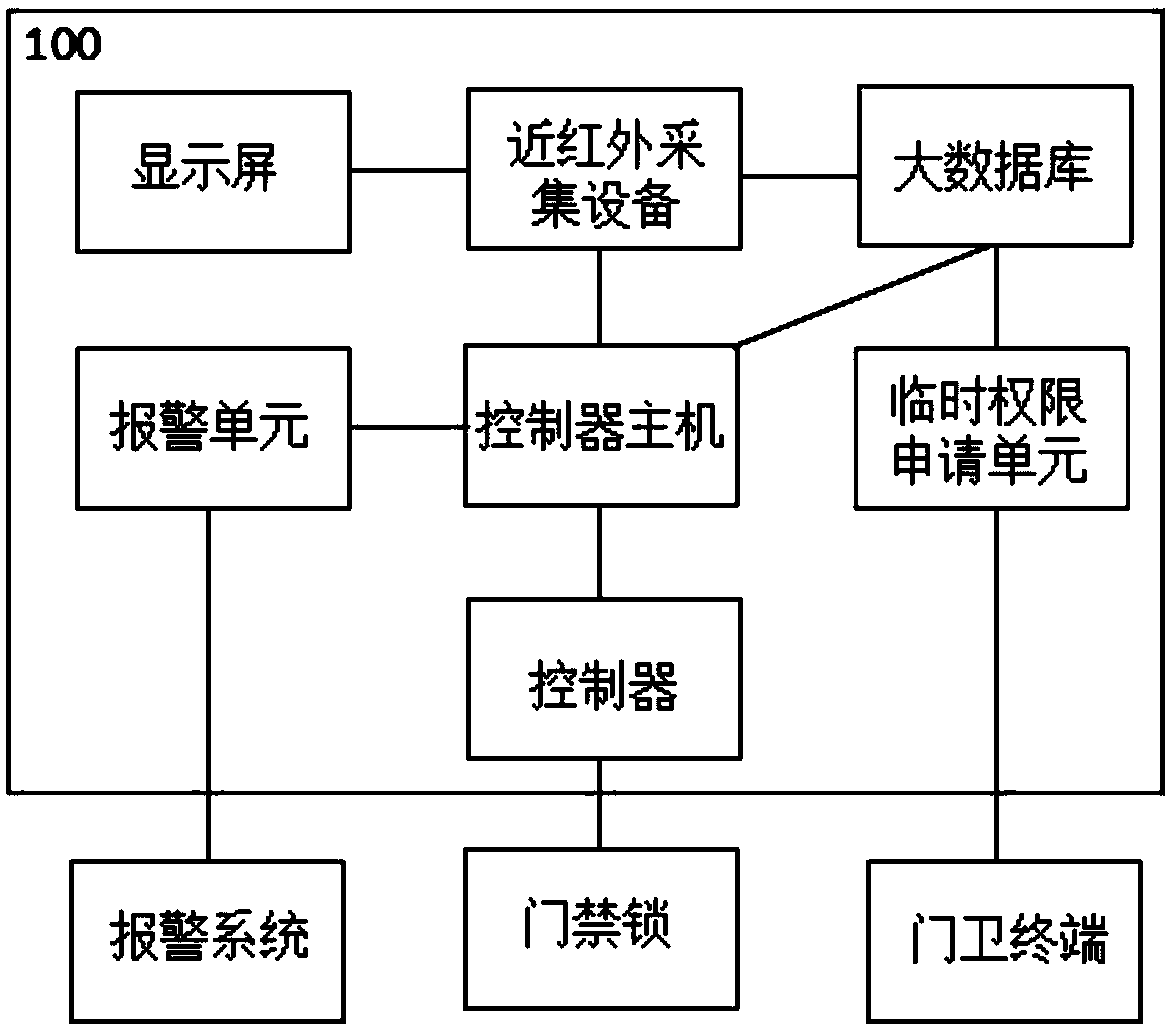
[0053] On the basis of Embodiment 1, the image data group includes: a long-term permission data group and a temporary permission data group, such as figure 2 As shown, the system 100 further includes: a temporary authority application unit.
[0054] The temporary authority application unit is used to receive the ID number and temporary visit time period entered by the temporary visitor through the guard terminal, retrieve the identity information corresponding to the ID number from the public security system, the identity information includes the record image data, and collect the face of the temporary visitor image, and match the record image data with the face image. If the match is successful, the ID number, temporary access time period and face image will be sent to the temporary permission data group; Delete the ID number and face image in the temporary permission data group.
[0055] It should be noted that the temporary authority application unit will automatically de...
Embodiment 3
[0058] On the basis of Embodiment 1 or Embodiment 2, the acquisition area corresponding to the acquisition area picture is set by adjusting the near-infrared image acquisition device according to actual needs; the size of the display screen is set according to the actual required acquisition image size; the alarm system Including: security system and / or public security system.
[0059] Using a large screen or increasing the collection screen can increase the number of faces in the collection screen, and simultaneously recognize and match multiple faces, improve the recognition efficiency, and prevent the occurrence of congestion at the access control.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com