Access control and virus defense method and system based on dns protocol
An access control and virus technology, applied in the field of network security, can solve problems such as high superimposed costs, professional influence, abnormal access to secondary domain names, etc., to increase flexibility and comprehensiveness, expand matching strength, and enrich the system feature library Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be described in detail below, and the technical schemes in the embodiments of the present invention will be clear and complete, and it is apparent that the described embodiments are merely the embodiments of the present invention, not all of the embodiments. Based on the embodiments of the present invention, there are all other embodiments obtained without making creative labor without making creative labor premises.
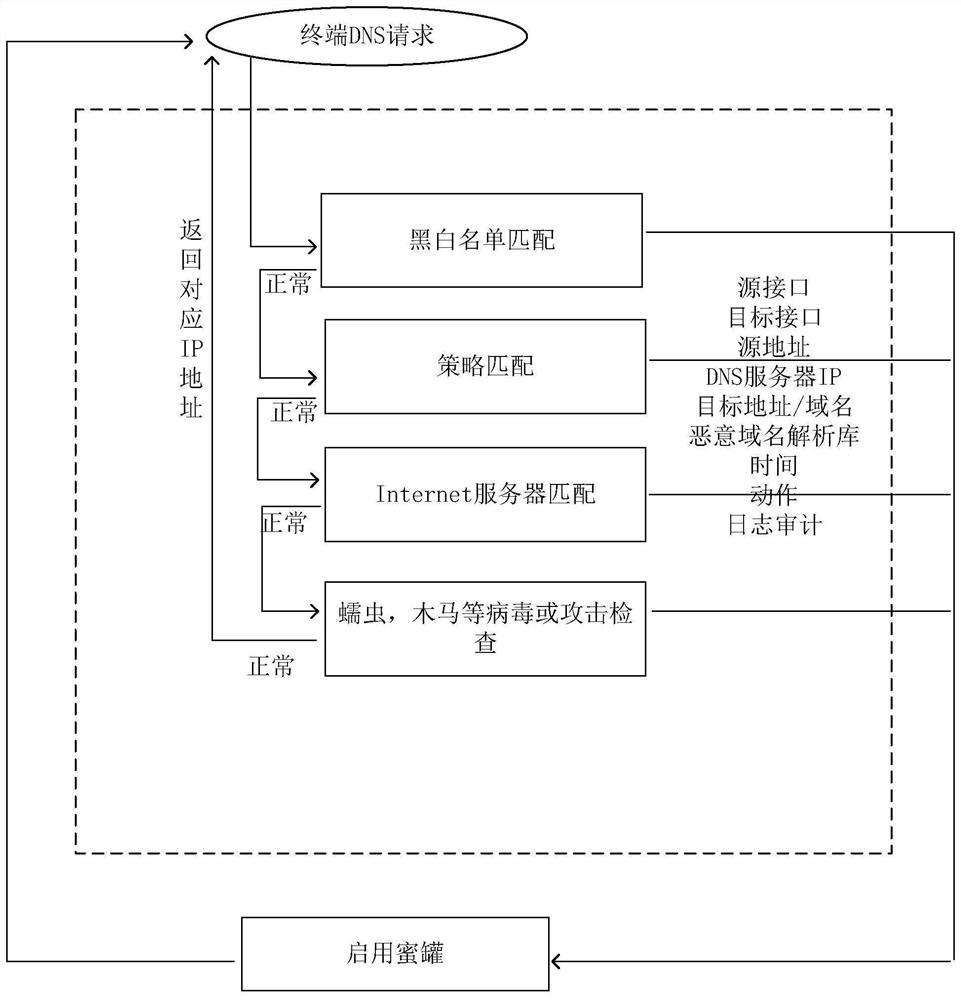
[0034] For the shortcomings of the prior art, it is an object of the present invention to provide an access control and a viral defense method based on a DNS protocol, which includes the following steps:
[0035] (1) Terminal sends DNS request;
[0036] (2) The DNS request matches the strategy of the settings, if you match the whitelist match; if you don't match the whitelist, enable honeypot;
[0037] (3) For the matching DNS request to continue analysis, record the time, source IP address, query domain name, and correlation analys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com