Hardware Trojan detection method based on local area circuit mutual reference
A hardware Trojan detection and hardware Trojan technology, applied in the protection of internal/peripheral computer components, etc., can solve the problems of difficult to effectively predict the differences of integrated circuits, effective data matching, and multiplexing, so as to reduce test costs and test efficiency, and realize positioning , The effect of accelerating the practical process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
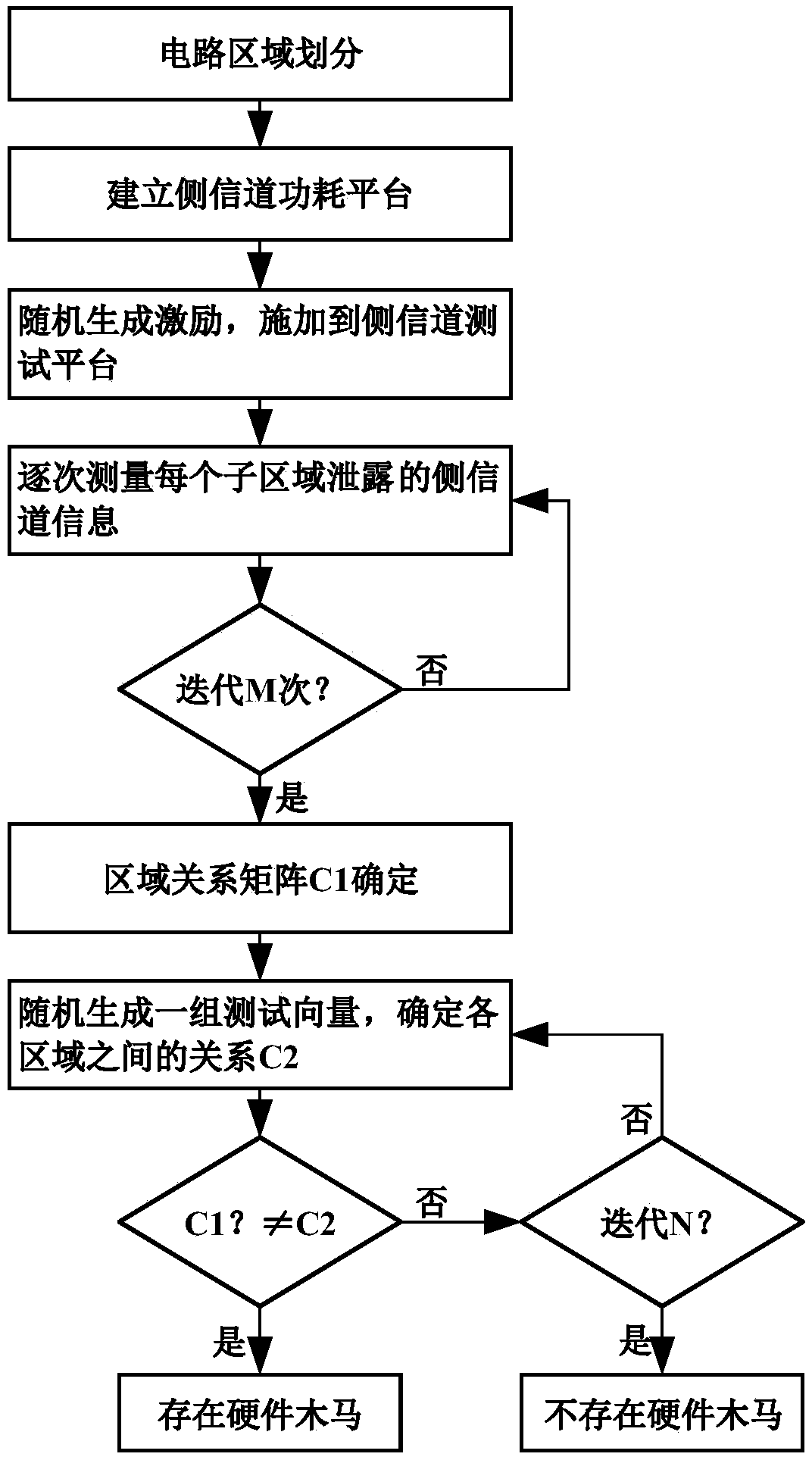
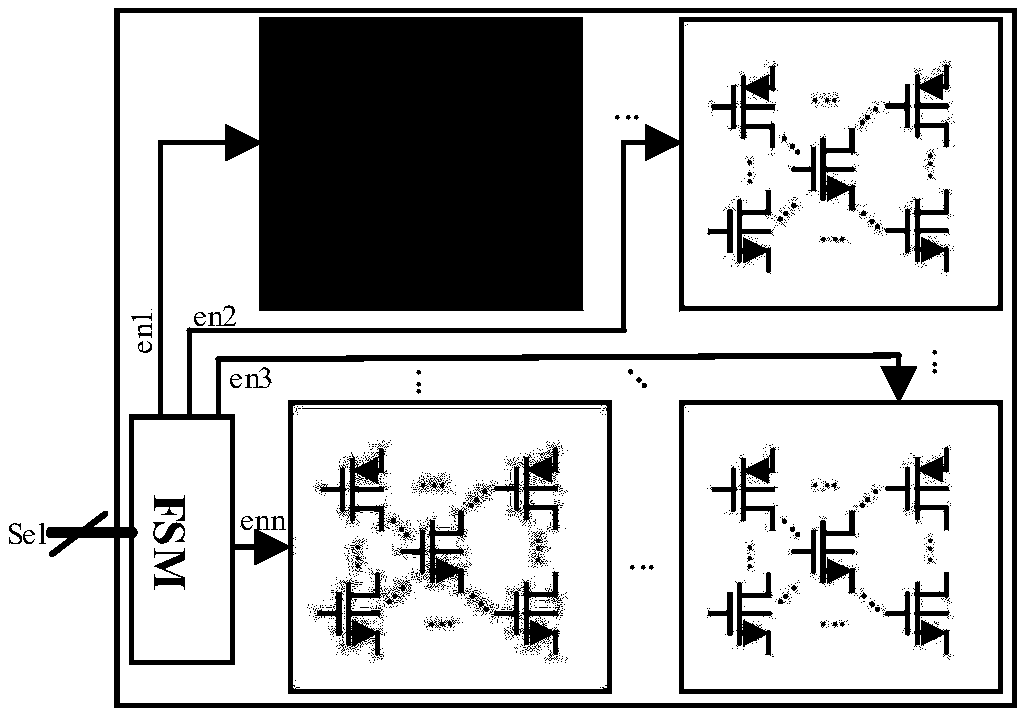
[0032] In view of the difficulty in obtaining reference models in side-channel analysis and the fact that process deviations seriously affect the recognition efficiency of side-channel analysis, the nonlinear regression method is used to determine the relationship between circuits in local areas, and this relationship is used as a cross-reference model. If there is a hardware Trojan , when the hardware Trojan is activated, it will change the relationship matrix of the local circuit. The relationship matrix between local circuits will change with each other, adaptively solve the process deviation problem between integrated circuits, greatly improve the accuracy of side channel analysis, and use the relationship between local circuits as a reference model , without reverse analysis to obtain the original design data of the circuit to construct a golden reference model that is in good agreement with the actual situation, which solves the mainstream problem of hardware Trojan detec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com