A secure USB disk for solid state disk authentication
A solid-state hard disk, secure technology, applied in the protection of internal/peripheral computer components, instruments, digital data authentication, etc., can solve the problem of low security, operability and efficiency, single mode encryption storage method, reducing data security and other problems, to achieve the effect of complete data destruction, improvement of security performance, and prevention of illegal intrusion or cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be further described below in conjunction with the accompanying drawings.
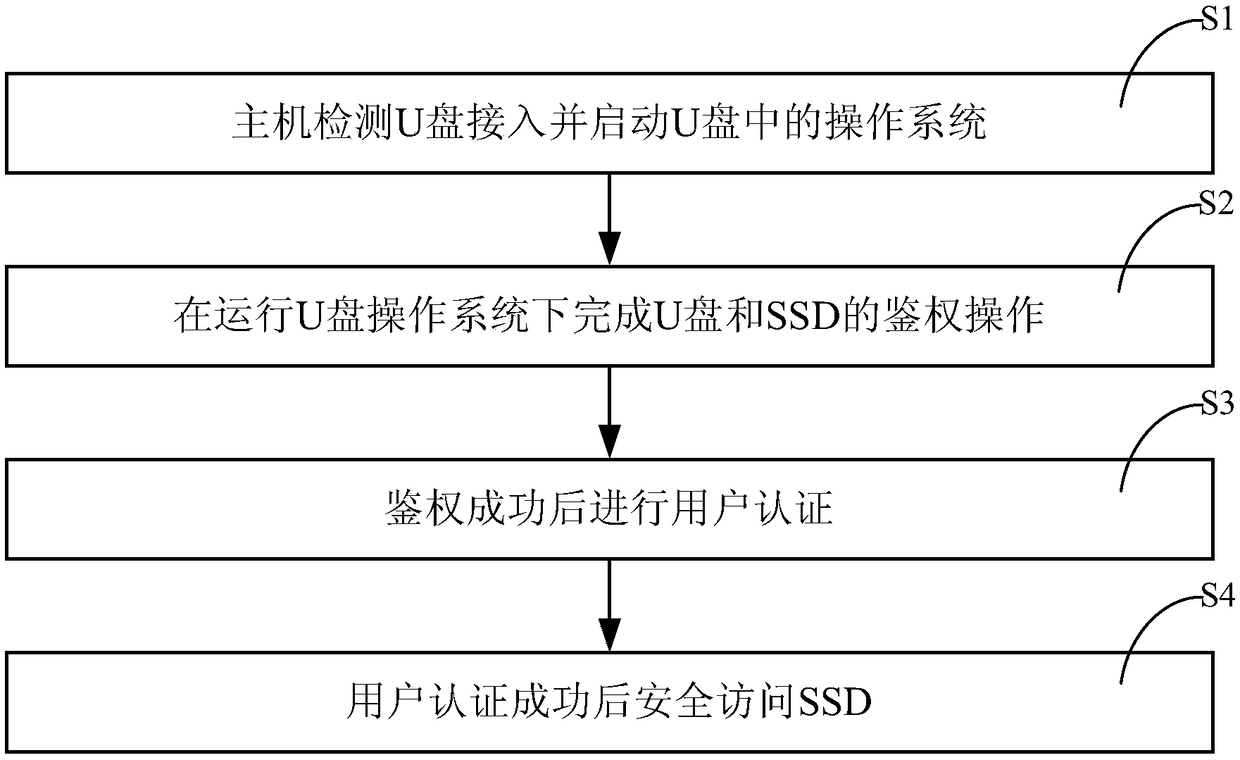
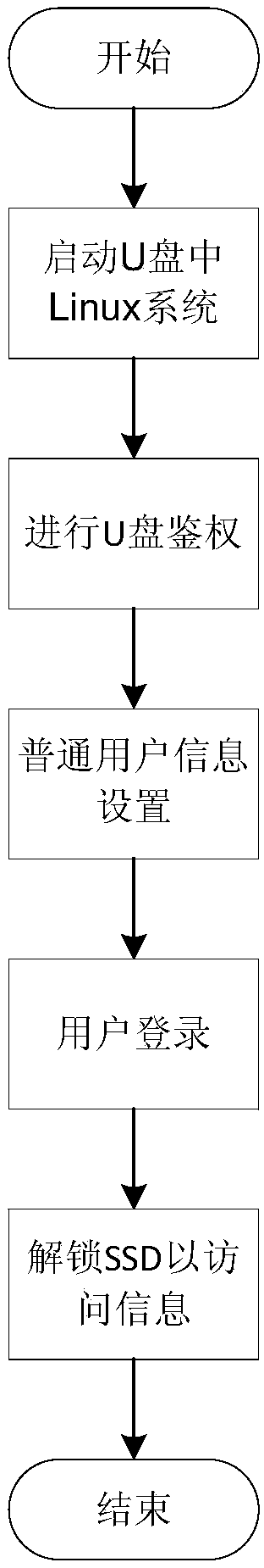
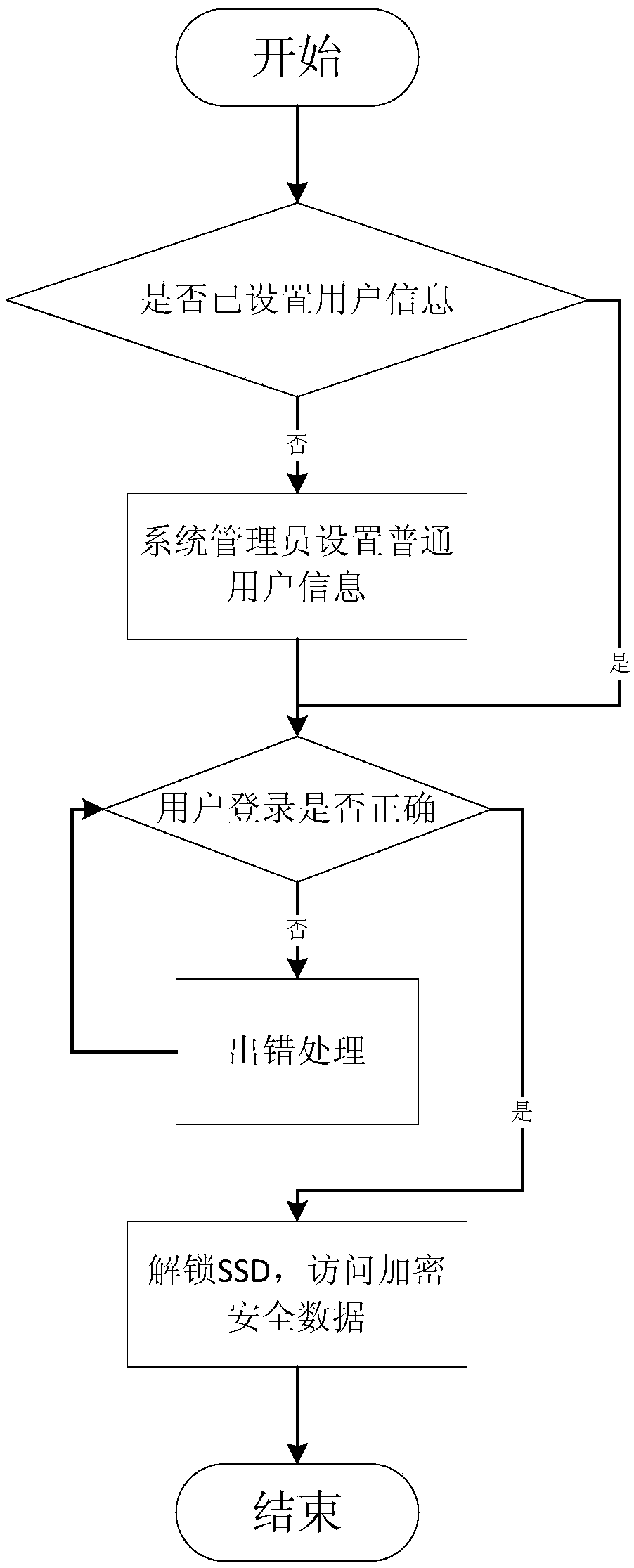
[0032] In order to address the shortcomings of the prior art, see Figure 4 and 5 , the invention discloses a secure USB flash drive for solid-state hard disk authentication, including a secure USB flash drive and a solid-state hard drive (SSD) connected to a host, and the secure USB flash drive at least includes a first interface module and a USB flash drive controller , a first authentication module and a user login management module, the SSD at least includes a second interface module, an SSD controller, a second authentication module and a data storage module, wherein the first interface module is connected to the host for realizing The secure U disk communicates with the outside; the second interface module is connected with the host for data communication between the SSD and the outside; the U disk controller is connected with the first interface module, the fir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com