Network risk blocking method based on attack graph and co-evolution
A co-evolution and attack graph technology, applied in electrical components, transmission systems, etc., can solve problems such as low accuracy, long calculation time, and inability to achieve the effect of improving efficiency, reducing cost, and enhancing accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
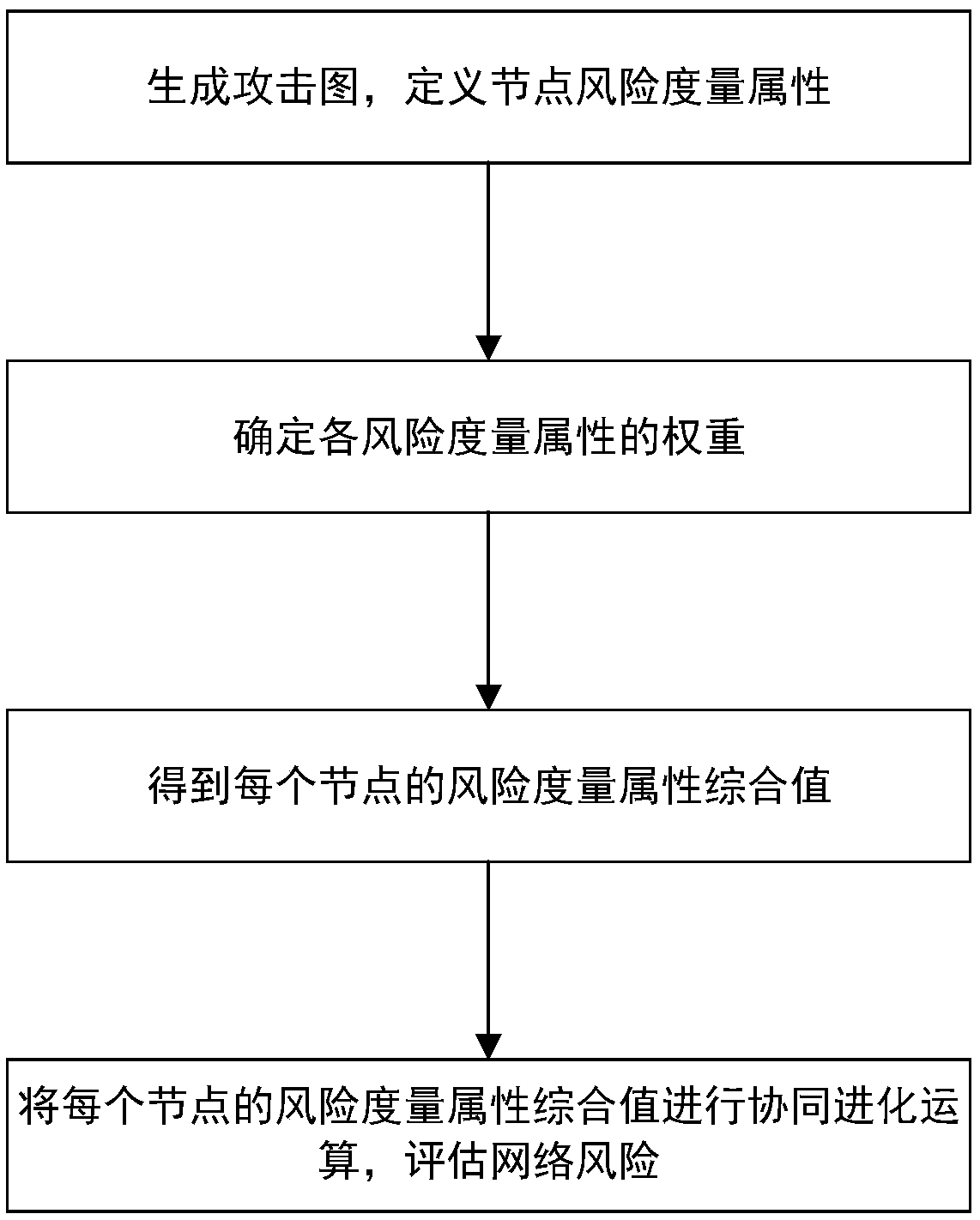
[0032] The present invention will be described in detail below with reference to the accompanying drawings and examples.
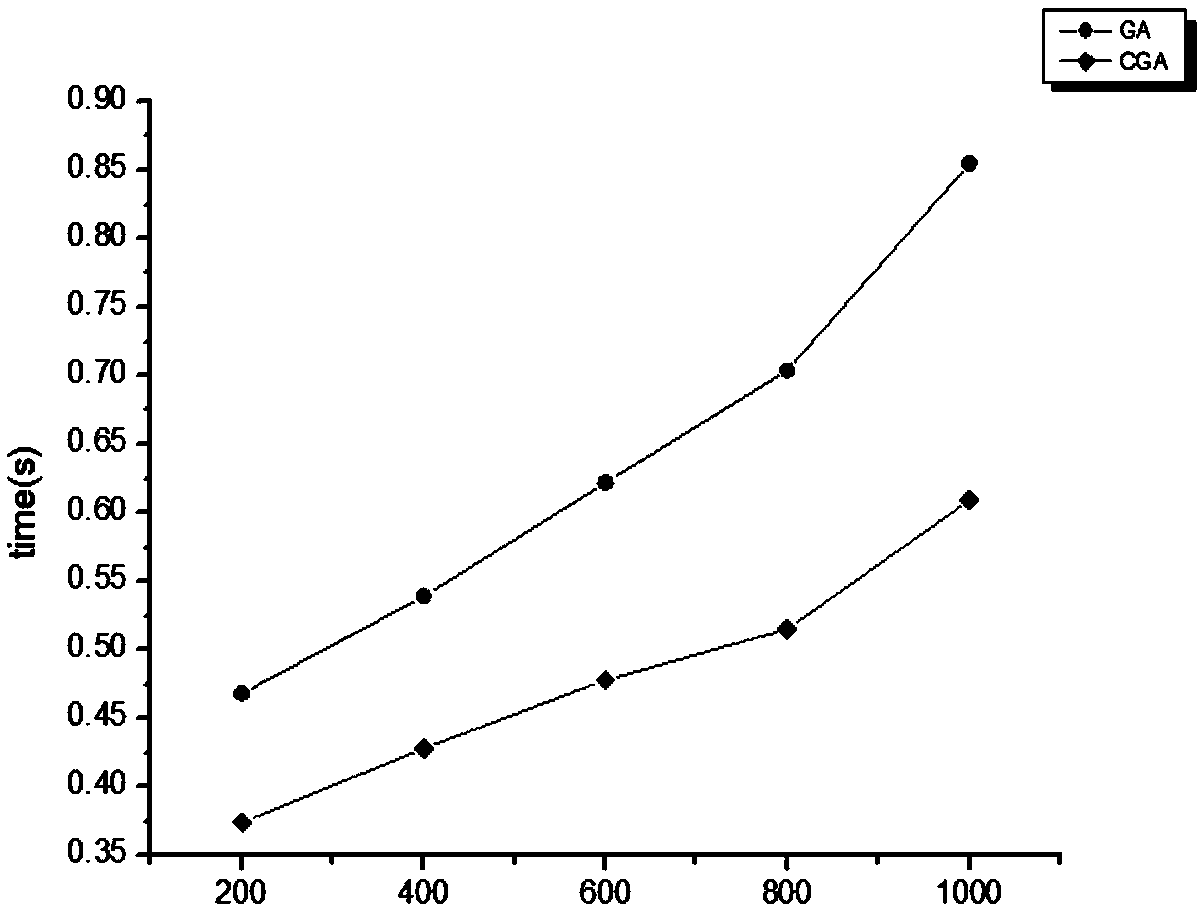
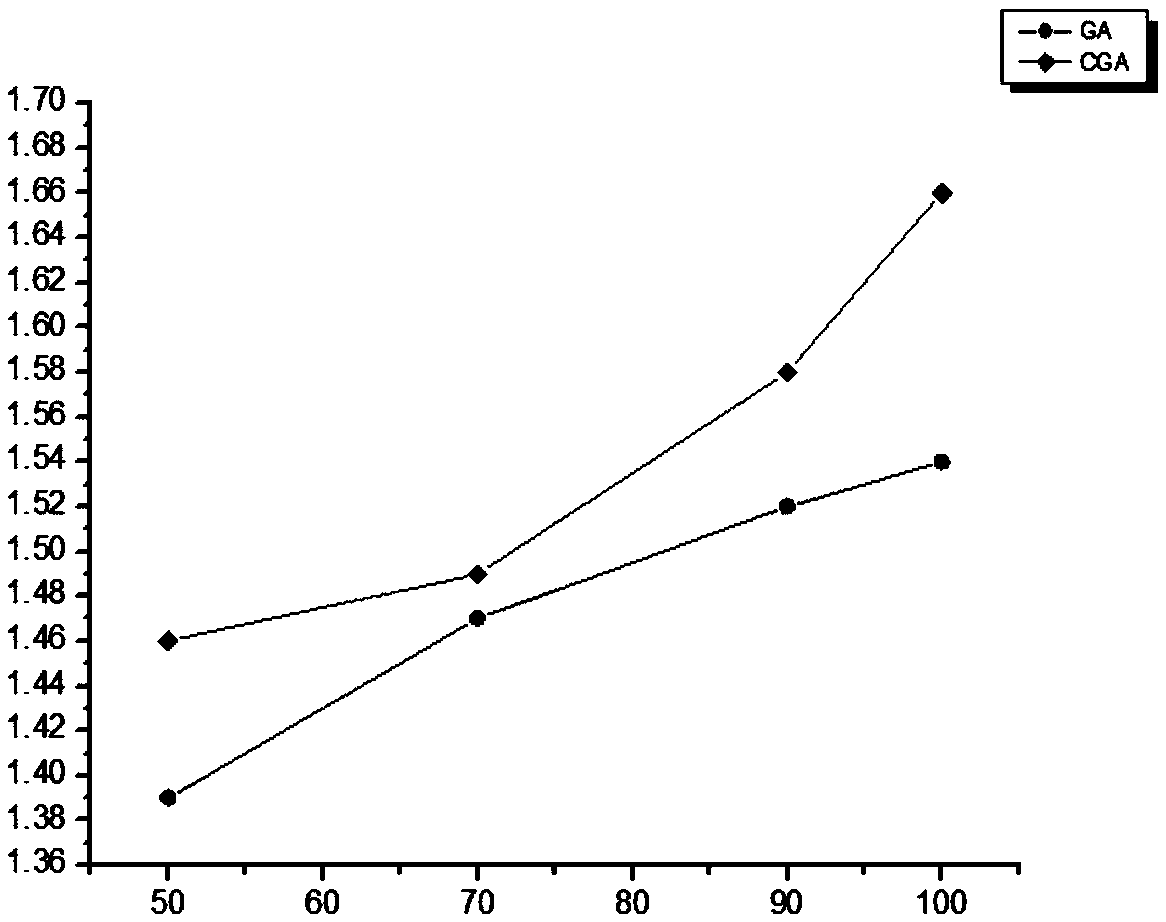
[0033] The attack graph model considers the network topology information in the network modeling work, which provides comprehensive information for the evaluation, and the model detector provides an automatic means for the generation of the attack graph model, which reduces the human subjective factors in the evaluation work. Influence, more scientifically. The attack graph model can be used to qualitatively or quantitatively analyze the vulnerable links, vulnerable links, attack paths, and system loss risks of computer network systems.
[0034] The co-evolutionary algorithm is a new algorithm proposed for the deficiencies of the current popular intelligent optimization algorithms. It considers the influence of the relationship between individuals and between individuals and the environment on the evolution of individuals. Compared with the genetic algor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com