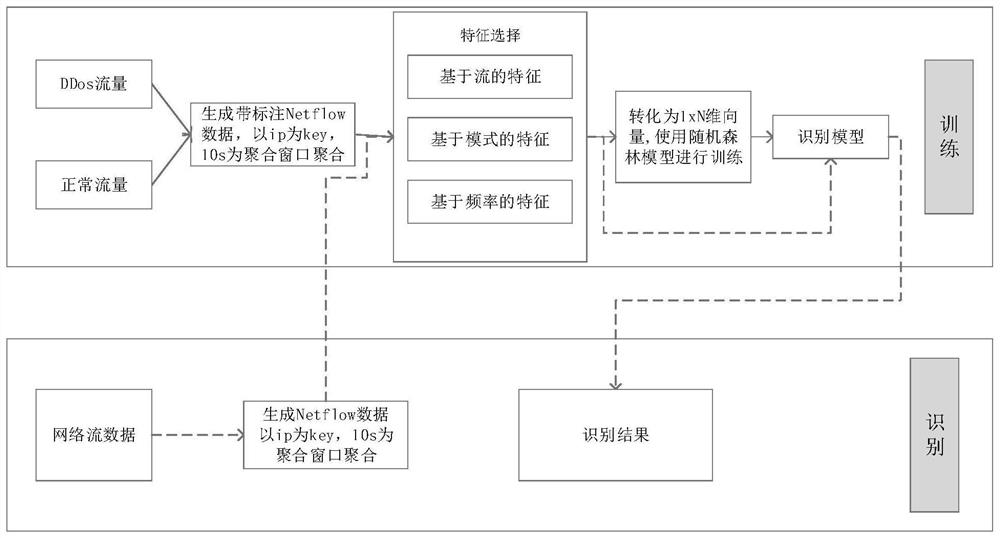
A ddos identification method and system based on multi-dimensional state transition matrix features
A state transition matrix, multi-dimensional technology, applied in the field of information, can solve problems such as low precision, not yet covered pattern features, etc., to achieve the effect of low consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0071] Example 1: DDos identification on the deployment environment
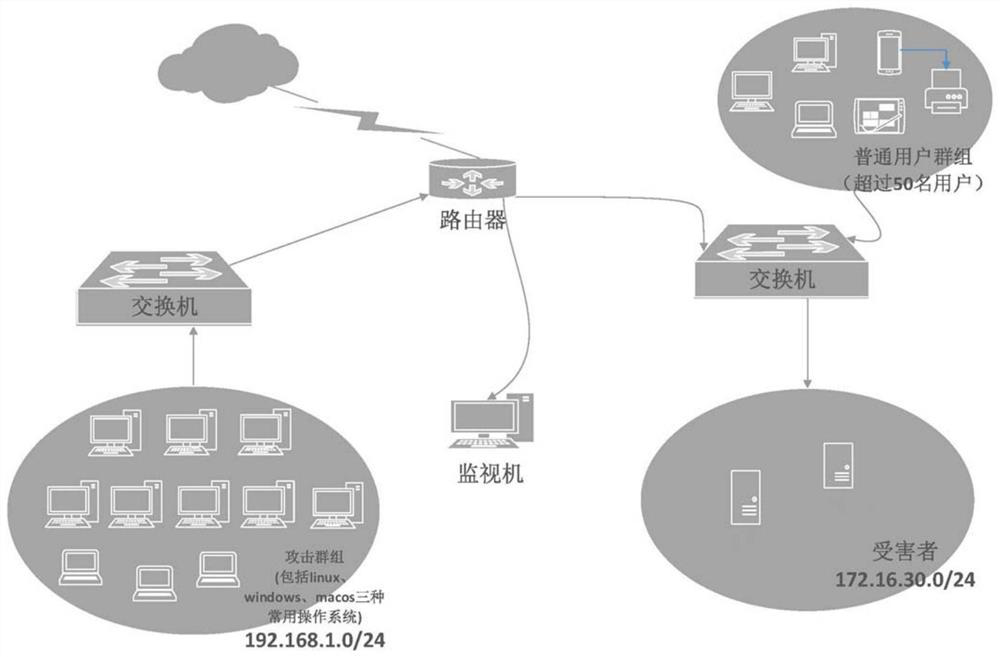
[0072] exist figure 2 Experiments were carried out in the environment shown. The DDos traffic is generated by LOIC, PyLoris, DABOSET, Glodeneye, Hulk, Slowsloris, Torshammer, and hping3, eight commonly used DDos attack tools used by hackers, and the normal traffic is generated by the normal behavior of users. After feature extraction, 20W pieces of DDos data and 40W pieces of normal data are obtained for training to generate a recognition model. 10W pieces of DDos data in the same dimension and 10W pieces of normal data were tested, with an accuracy rate of 99.5% and a misjudgment rate of only 0.4%.
example 2
[0073] Example 2: Identification on the public dataset CIC-IDS-2017
[0074] The public data set CIC-IDS-2017 contains 8.23GB of Pcap files. After feature extraction, 13W pieces of normal data and 9W pieces of DDos data are obtained. Using ten-fold cross-validation for evaluation, the accuracy rate is 97.4%, and the misjudgment rate is 1.7%.
[0075] Another embodiment of the present invention provides a DDos identification system based on multi-dimensional state transition matrix features, which includes:
[0076] The data collection module is responsible for collecting network flow metadata and marking DDos traffic and normal traffic;
[0077] The multi-dimensional feature building module is responsible for extracting multi-dimensional features of DDos based on the state transition matrix by using the collected and labeled network flow metadata;
[0078] The model training module is responsible for using the extracted multi-dimensional features and using machine learning a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com