ivr risk emergency control method and system
An emergency control and risk technology, applied in subscriber special services, electrical components, automatic exchange, etc., can solve problems such as automatic switching, remote manual switching and operation, and inflexible methods, so as to increase risk prevention and processing methods, improving timeliness and flexibility, and avoiding direct losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
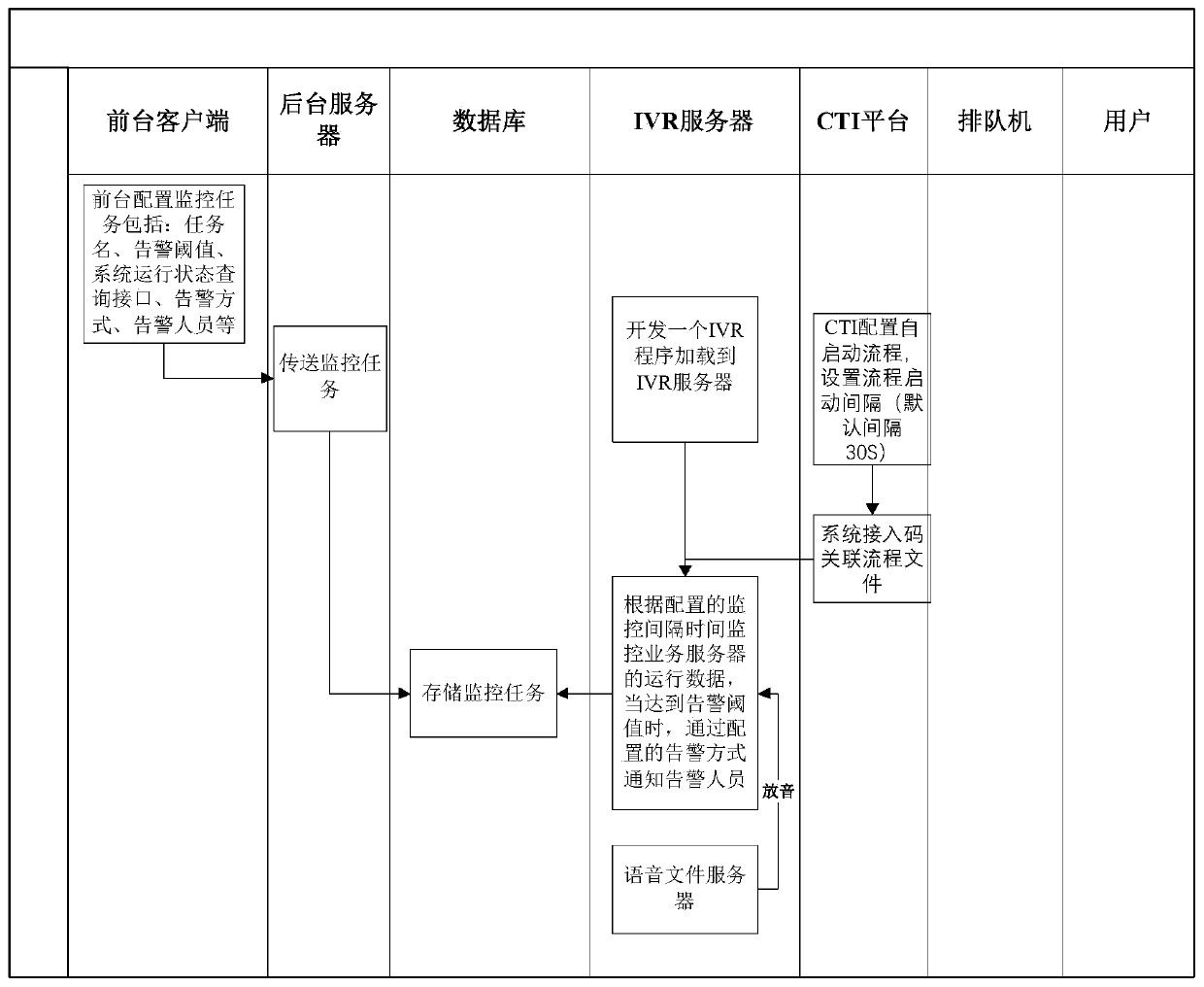
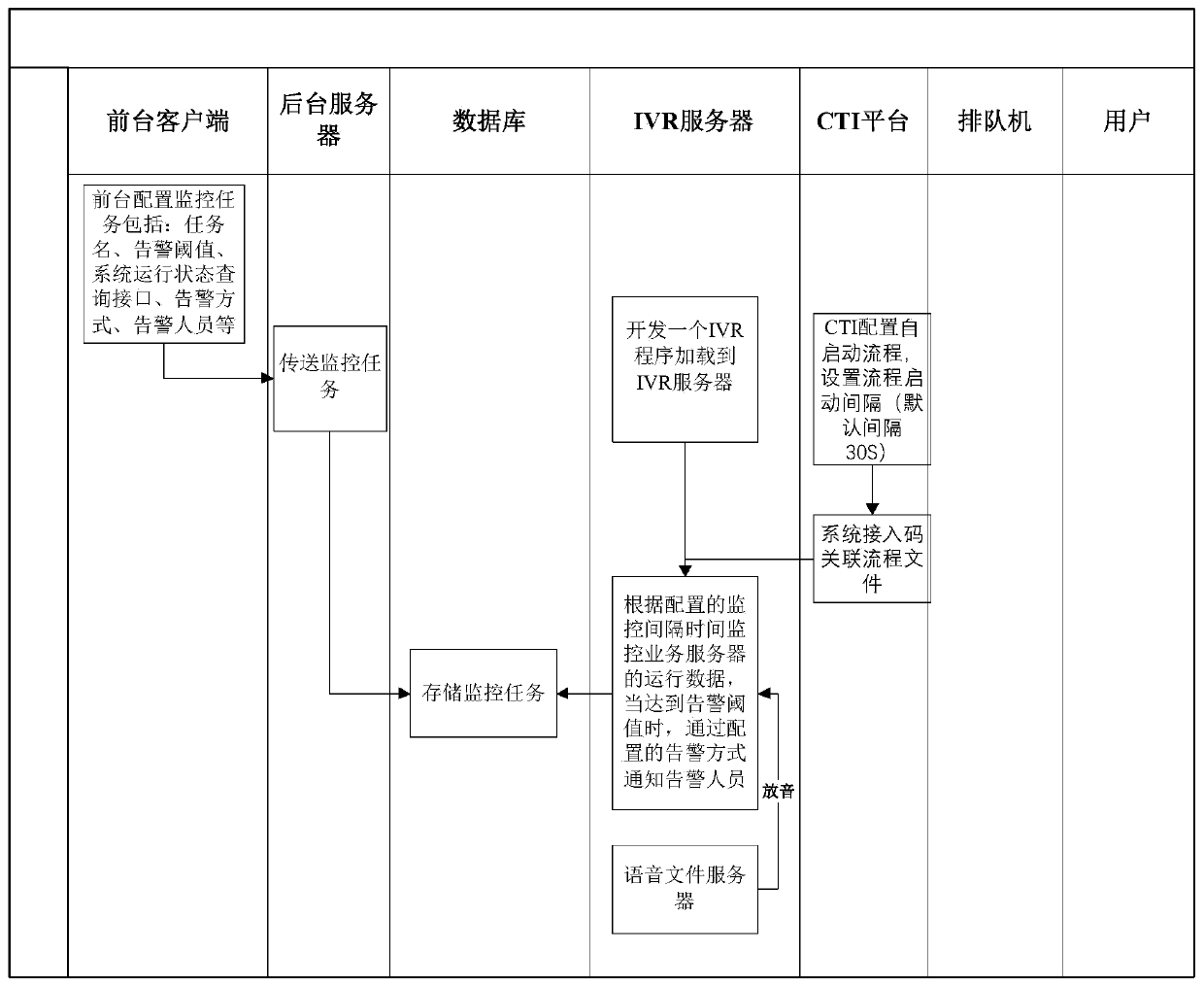
[0044] A kind of IVR risk emergency control method, see figure 1 , including the following steps:
[0045] The foreground client configures at least one monitoring task, and stores the monitoring task in the database;
[0046] Specifically, the monitoring task includes a task name, an alarm threshold, a monitoring interface of a service server, an alarm method, an alarm person, an alarm frequency, a do-not-disturb time, and the like. Each business can set a monitoring task independently. The monitoring task provides the monitoring interface of the service server, so that the subsequent IVR server can read the operation data of the service server through this interface. The operating data of the business server includes the number of users, memory, hard disk usage, etc. Alarm methods include interactive response methods such as text messages and telephone calls. The alarm person is the person to be notified when an alarm occurs.
[0047] When the IVR server detects that th...
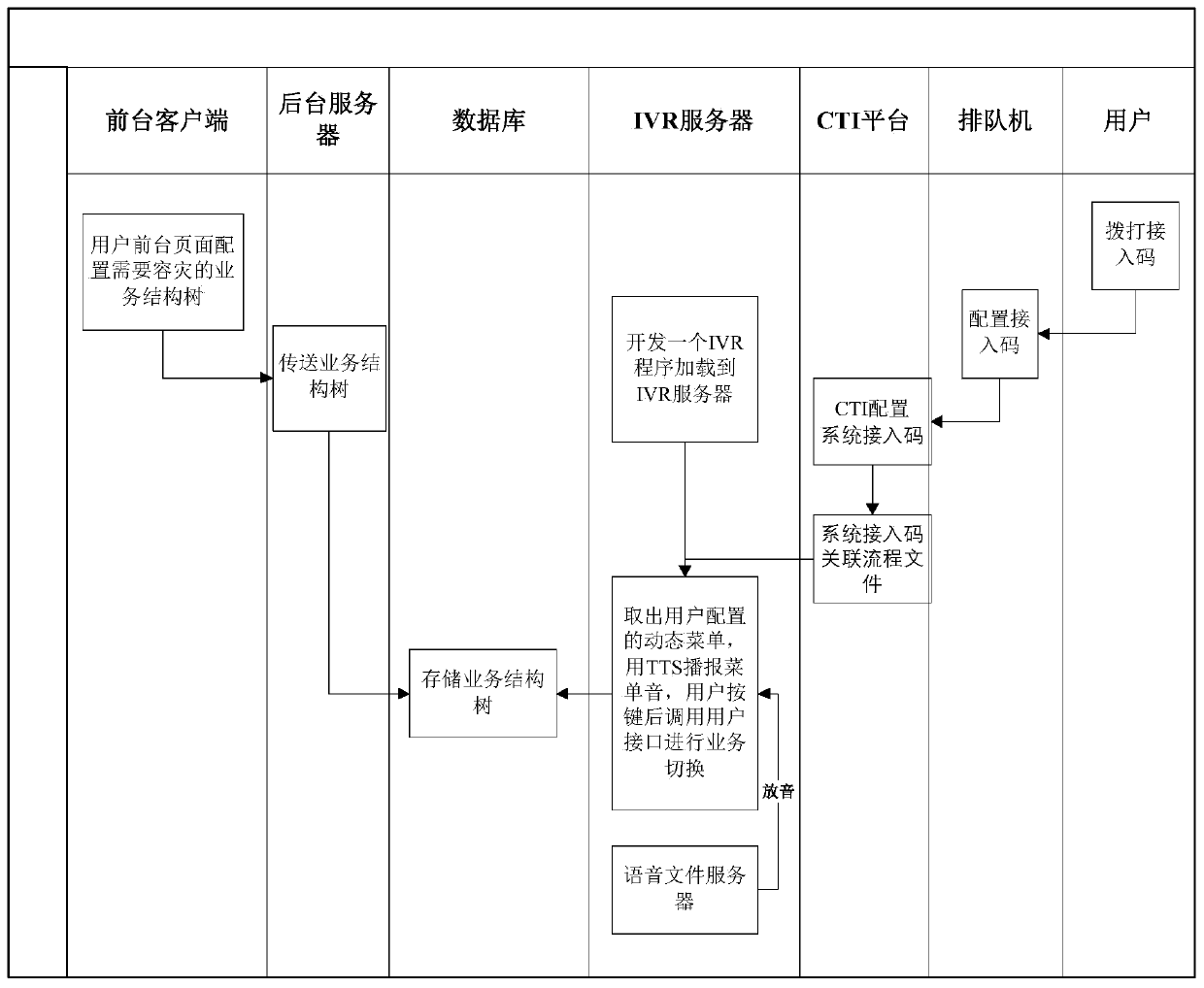
Embodiment 2
[0066] An IVR risk emergency control system, comprising:
[0067] Foreground client: used to configure at least one monitoring task, and send the monitoring task to the background server;
[0068] Background server: used to send the monitoring task to the database;
[0069] Database: used to store the monitoring tasks;
[0070] IVR server: used to read the operating data of the service server according to the monitoring task when it is detected that the preset monitoring interval time is reached; it is also used to detect that the operating data of the service server reaches the alarm set in the monitoring task When the threshold is exceeded, an alarm message is generated, and the alarm information is notified to the alarm personnel set in the monitoring task by text message or telephone.
[0071] Preferably, the monitoring task includes a task name, an alarm threshold, a monitoring interface of the service server, an alarm method and an alarm person.
[0072] Preferably, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com