Network intrusion detection method
A network intrusion detection and network testing technology, applied in the field of network security, can solve problems such as difficulty in obtaining the global optimal solution and poor search ability, so as to improve the detection accuracy rate, improve the overall performance, and reduce the false negative rate and false negative rate rate effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
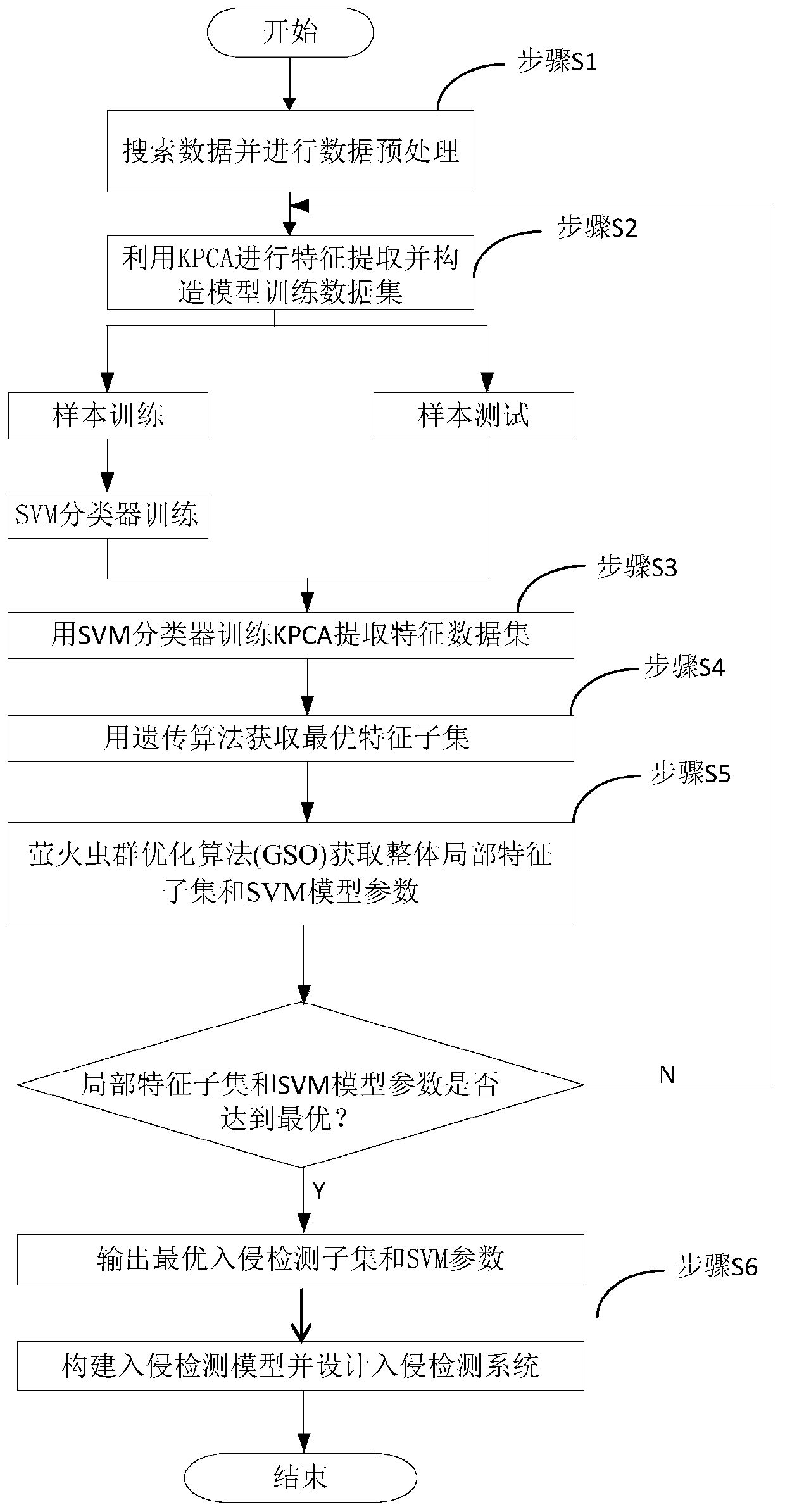
[0124] According to the following Figure 1 to Figure 4 , the preferred embodiment of the present invention is described in detail.
[0125] like figure 1 As shown, the present invention provides a network intrusion detection method, comprising the following steps:
[0126] Step S1, searching network data to construct a test network data set;
[0127] Step S2, using Kernel Principal Component Analysis (KPCA) to perform feature extraction on the test network data set to construct a training data set;
[0128] Step S3, put the training data set into the SVM classifier for training to obtain the characteristic data set;
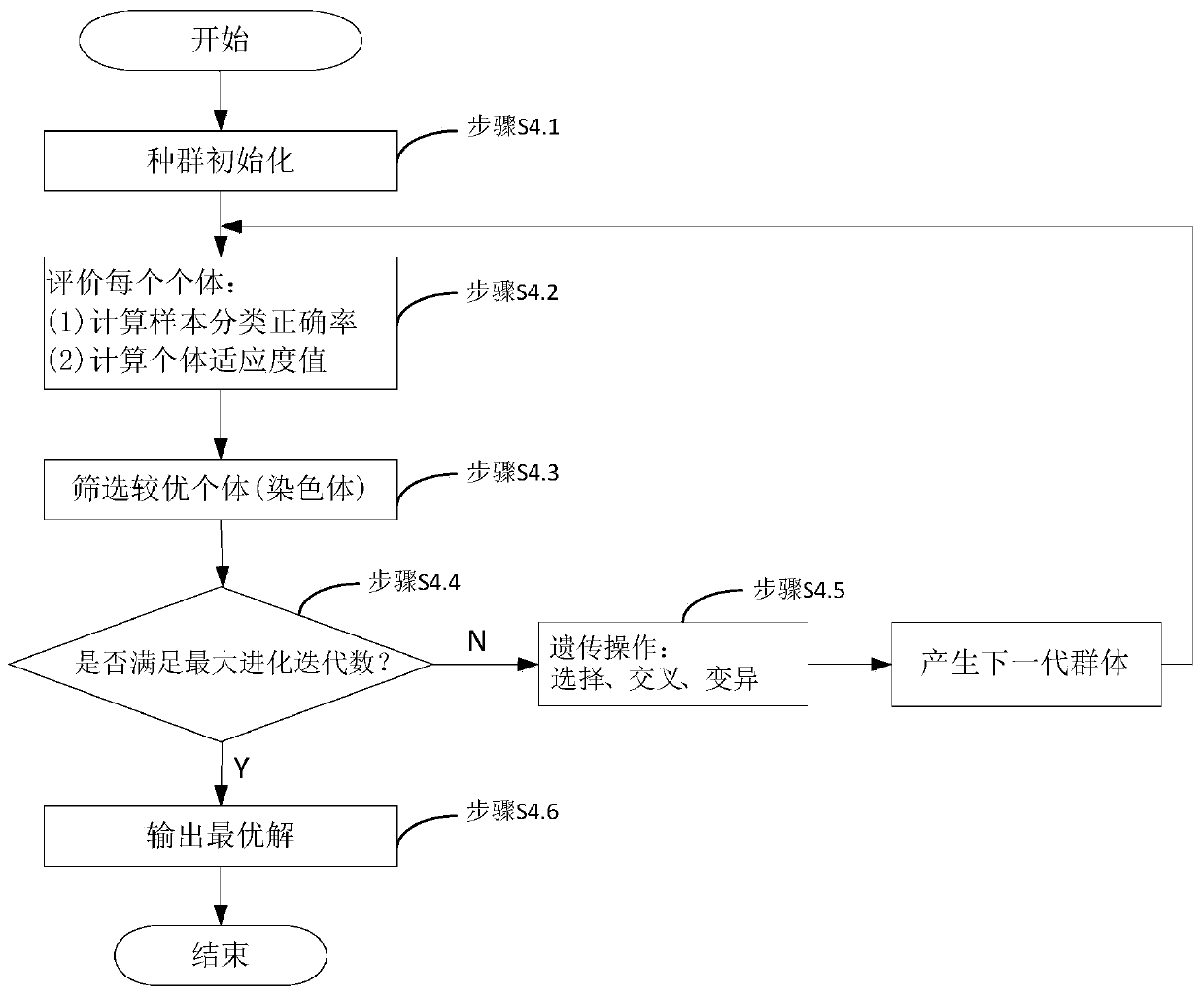
[0129] Step S4, using the Genetic Algorithm (GA) to obtain the optimal feature subset from the feature data set;
[0130] Step S5, using the firefly swarm optimization algorithm (GSO) to obtain the overall local optimal feature subset and the optimal SVM parameter from the optimal feature subset;
[0131] Step S6: Process the training data set according to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com