Network data flow detection method and device
A detection device and detection method technology, applied in the computer field, can solve the problems of non-adaptability of the network and high requirements for black and white traffic training sets, and achieve the effects of cost reduction and low dependence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
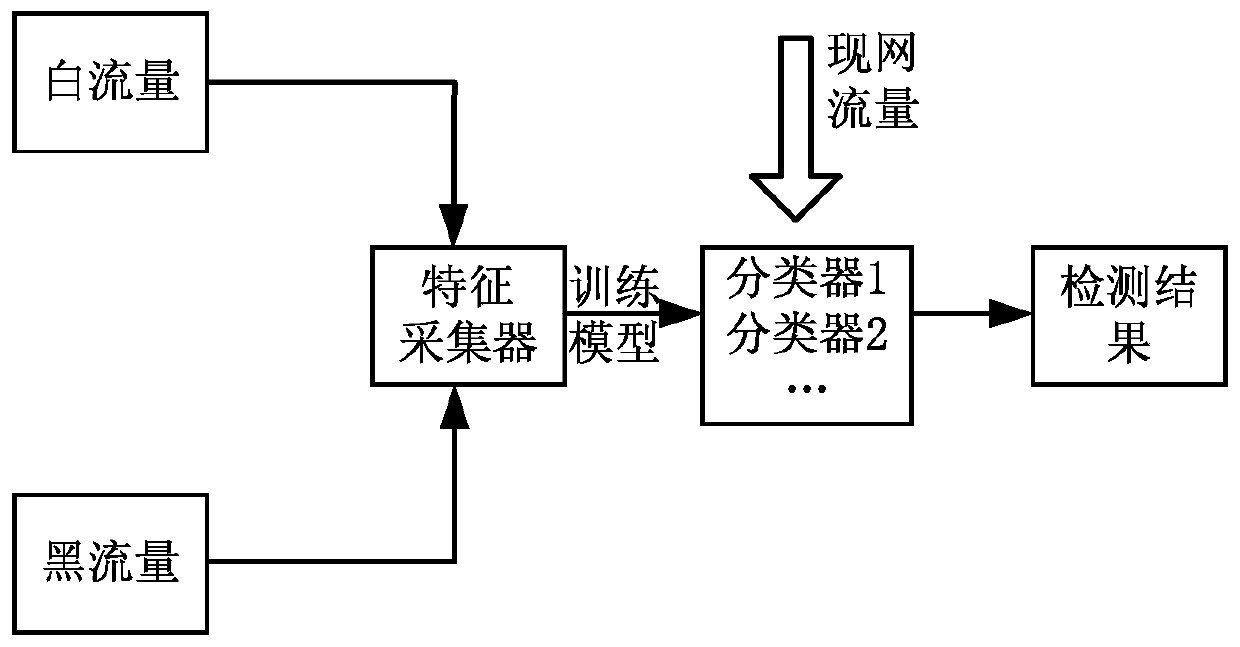
[0037] The embodiment of the present application provides a network data flow detection method and device, which are used to judge the type of the cluster by the size of the cluster, which can not rely on the extensiveness and accuracy of the training set, but requires the support of a high-quality training set, effectively reducing the The cost problem brought about by high-quality training sets has realized adaptive malicious traffic identification in different network environments, and is less dependent on human experience and has network adaptability.
[0038] In order to enable those skilled in the art to better understand the solution of the present application, the technical solution in the embodiment of the application will be described below in conjunction with the drawings in the embodiment of the application. Obviously, the described embodiment is only a part of the application Examples, but not all examples. Based on the embodiments in this application, all should ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com