Malicious file detection technology based on random forest algorithm
A random forest algorithm and malicious file technology, applied in the field of malicious file detection based on random forest algorithm, can solve the problems of inability to identify malicious file types, high false negative and false positive rates, and inability to effectively identify unknown malicious programs, etc. The effect of low false negatives and false positives, low consumption, and enhanced identification capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
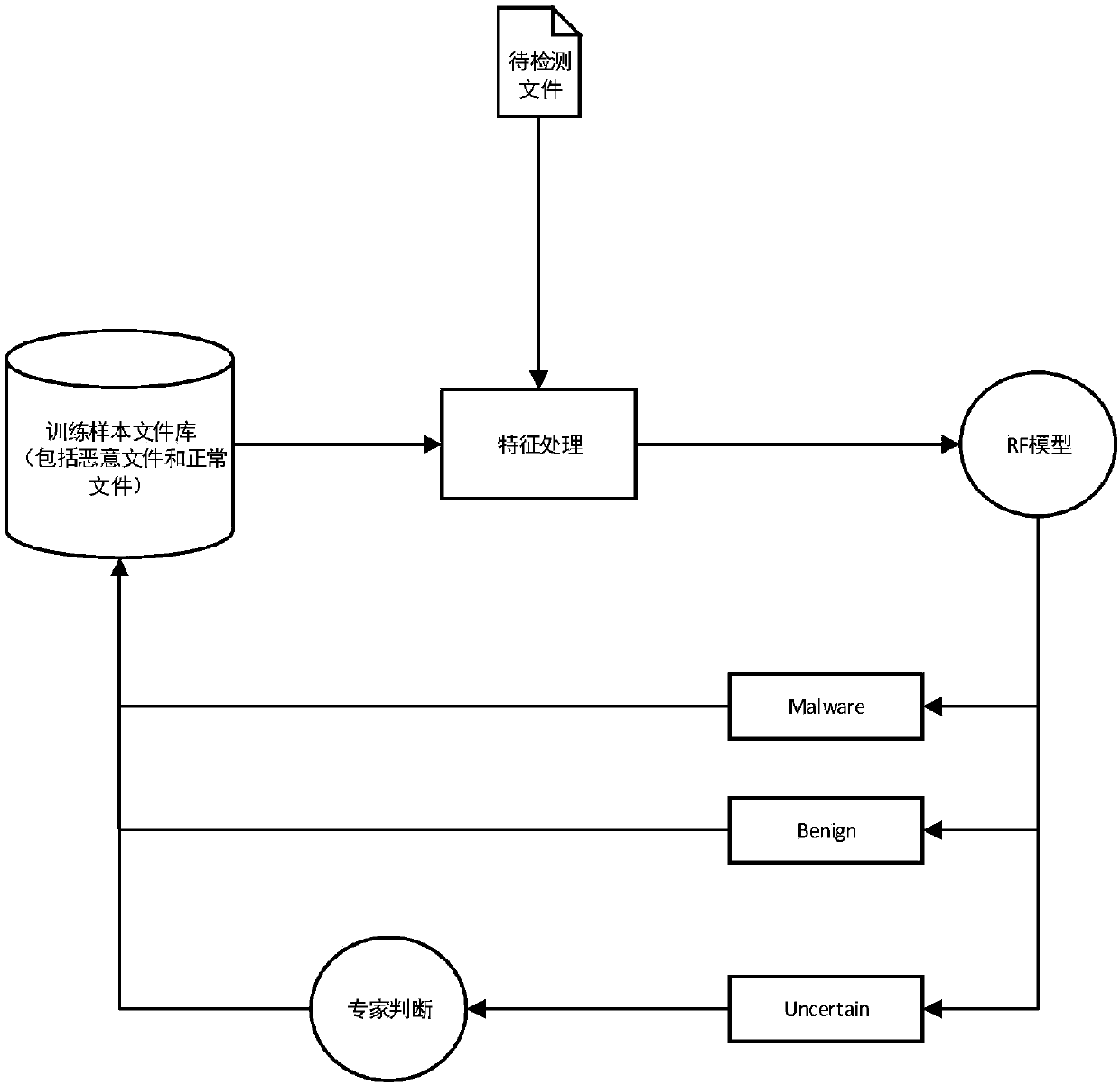
[0012] A kind of malicious file detection technical scheme based on random forest algorithm provided by the present invention is as follows:
[0013] Step 1: Collect malicious samples and normal samples. Collect public malicious, virus files and normal non-malicious files from open source virus websites as training samples.
[0014] Step 2: Build and install the sandbox module and collect all behavior information generated by malicious samples and normal samples in the sandbox.
[0015] Step 3: Construct 9 types of behavioral characteristics according to the function of the underlying API of the window.
[0016] Step 4: Process the sample data collected by the sandbox into 9 behavioral feature vectors as the training sample feature vectors.
[0017] Step 5: Use the processed training sample feature vector and input it to the random forest algorithm to learn a supervised classifier.
[0018] Step 6: Collect sandbox behavior data of unknown sample program files to be detected...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com