Edge computing data auditing system and auditing method based on hash binary tree
An edge computing and data auditing technology, applied in the field of network security, can solve the problem that the audit protocol is not applicable to the MEC environment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] The present invention will be further described in detail below with reference to the drawings and specific embodiments.
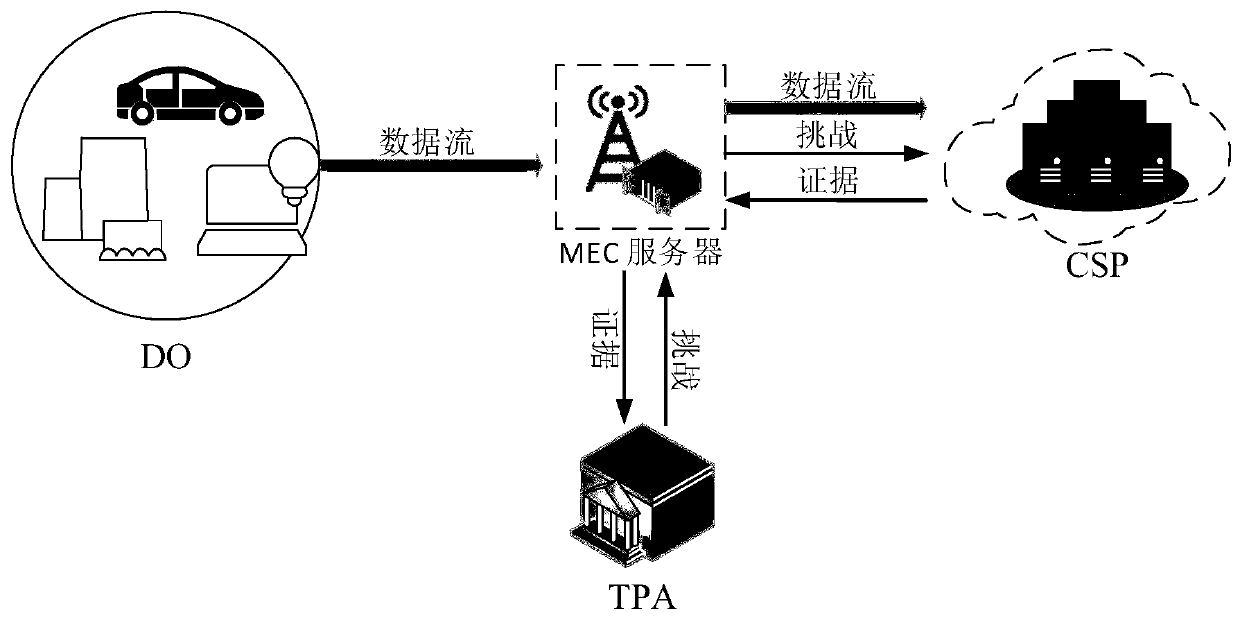
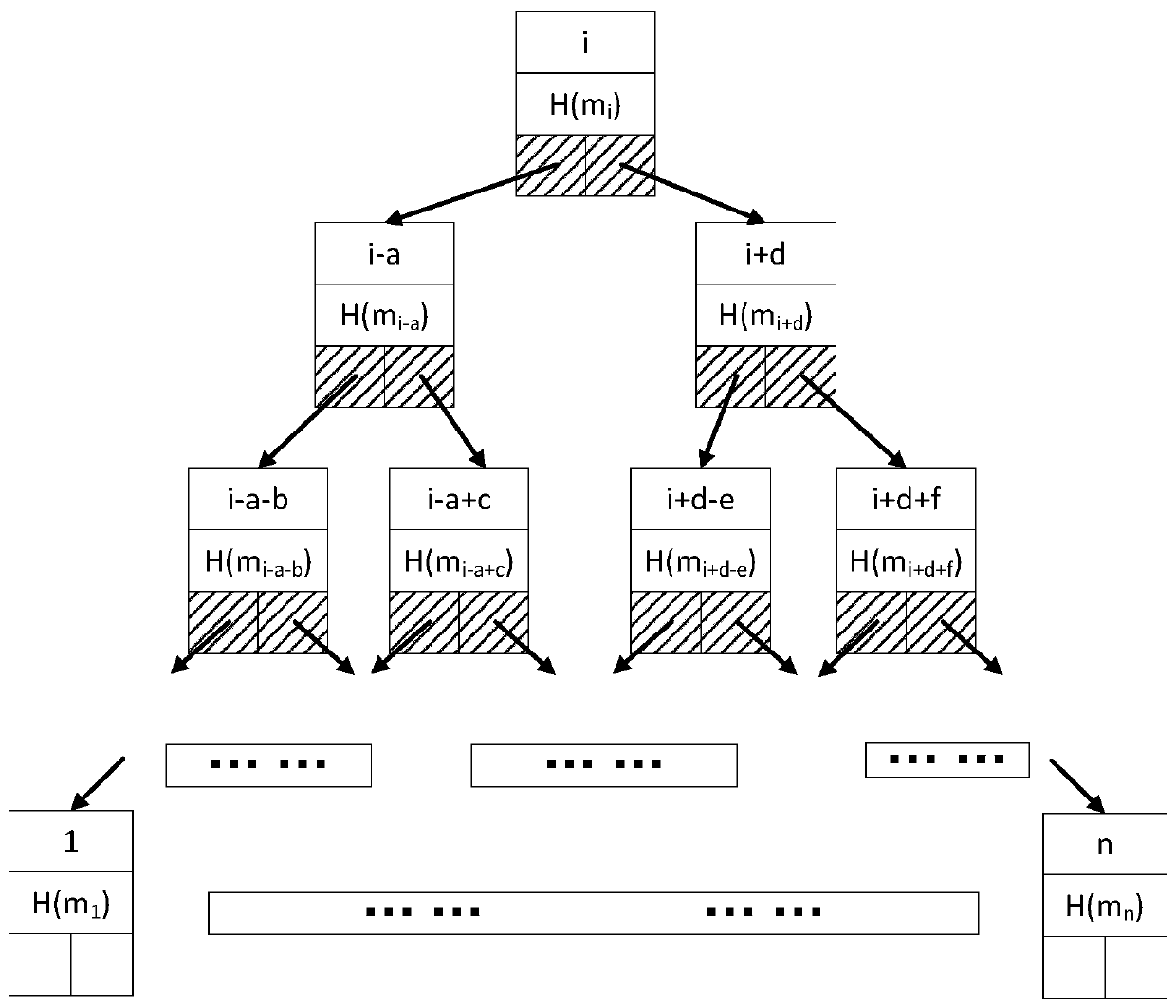
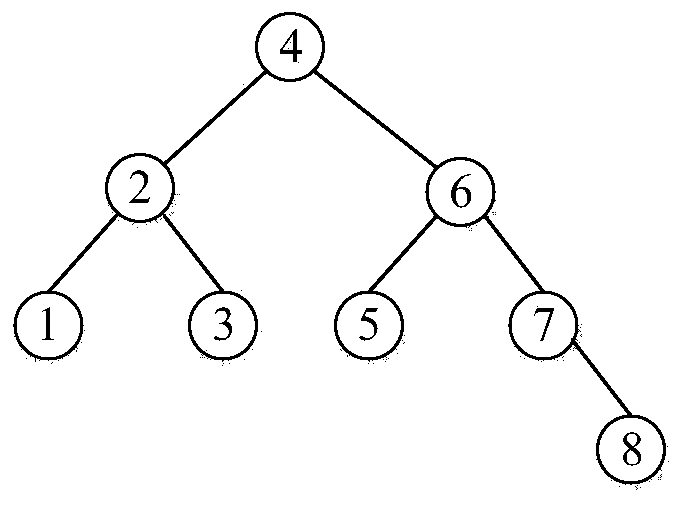
[0063] A hash binary tree-based edge computing data audit system, including DO, MS, CSP and TPA; the DO divides the data to be sent to the CSP into several data blocks, generates signatures for these data blocks, and then These data blocks and signatures are sent to the MS; after the MS receives the data, it verifies the source of the data, and after verification is legal, saves the tags of all data blocks and the data blocks commonly used by DO, and then sends the data blocks to the cloud server; when the audit cycle When it comes, TPA generates a set of challenge information and sends it to the MS. After receiving the challenge information, the MS generates a part of the evidence based on the data blocks and data tags it caches, and then sends the other part of the challenge information to the CSP, and the CSP sends it after generating the evidence T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com