Performance evaluation method for RFID reader anti-collision protocol
A reader and anti-collision technology, which is applied in the field of RFID radio frequency identification, can solve problems such as complex constraints, lack of a unified comparison standard for anti-collision protocols, difficulties in anti-collision protocols, etc., and achieve the effect of simple deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
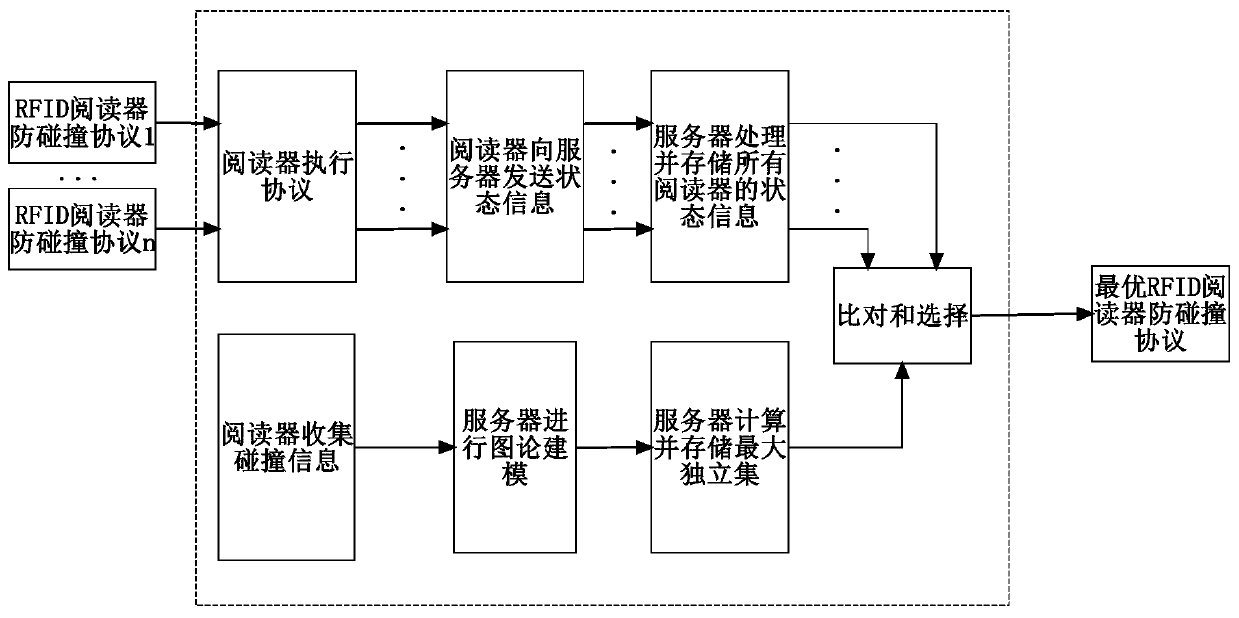
[0030] Such as figure 1 As shown, a performance evaluation method of RFID reader anti-collision protocol, including the following stages: RFID reader collision information collection stage, RFID server graph theory modeling stage, RFID reader anti-collision protocol testing stage and comparison and selection stage ;
[0031] RFID reader collision information collection stage: Under the unified coordination of the RFID server, each RFID reader sends a collision detection signal to the surrounding according to the power of the RFID tag read, and the RFID reader that receives the collision detection signal according to the collision The signal strength of the detection signal judges whether there will be a collision when the RFID reader sending the collision detection signal reads the tag at the same time, and sends the collision information to the RFID server;
[0032] RFID server graph theory modeling stage: the RFID server summarizes the collision information of all RFID read...
Embodiment 2
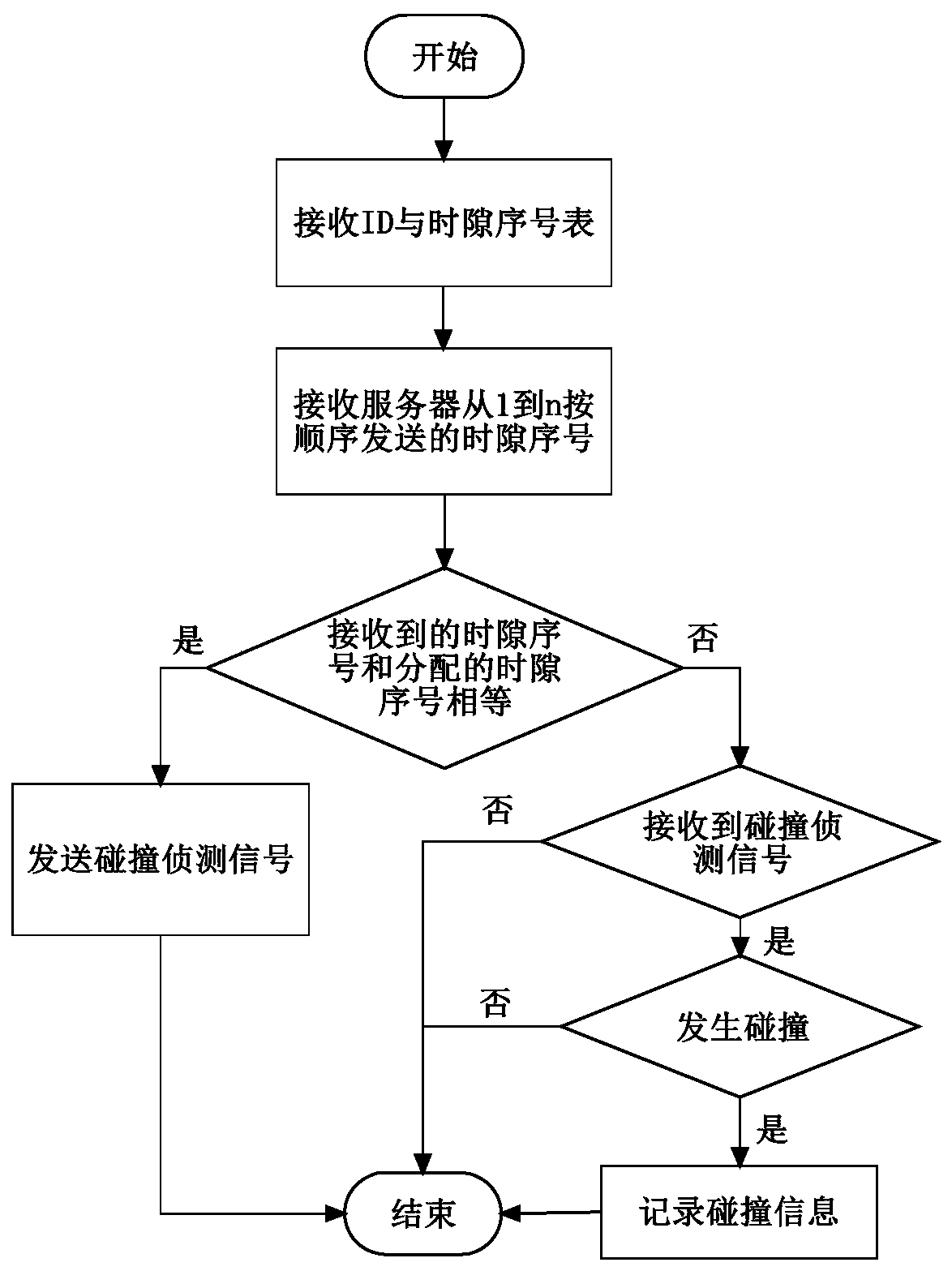
[0041] Such as Figure 1 to Figure 7 As shown, this embodiment proposes a performance evaluation method for an RFID reader anti-collision protocol, including an RFID reader collision information collection stage, an RFID server graph theory modeling stage, an RFID reader anti-collision protocol test stage, and comparison and selection stage. Among them, the specific application scenarios of RFID readers can be warehousing to identify goods, amusement parks to identify pedestrians, etc., where the exact or heuristic algorithm for solving the largest independent set can be exhaustive algorithm, Bron-Kerbosch algorithm, Vertex Support algorithm, etc.
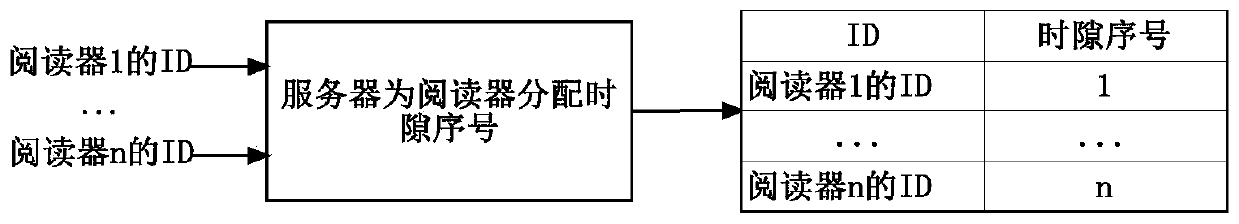
[0042] figure 2 It is a system block diagram of the server allocating time slots for the reader in the stage of reader collision information collection. All readers have been connected to the server in the form of wired or wireless, the server obtains the IDs of all readers and assigns a unique time slot number to each reader, f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com