Trusted computing method and system
A technology of trusted computing and computing services, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as reduced computing performance, inability to apply large-scale applications, and large computing overhead, so as to reduce computing performance and improve reliability. Scalability, saving storage costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] In order to make the purpose, technical solutions and advantages of the present application clearer, the present application will be further described in detail below with reference to the accompanying drawings and examples.
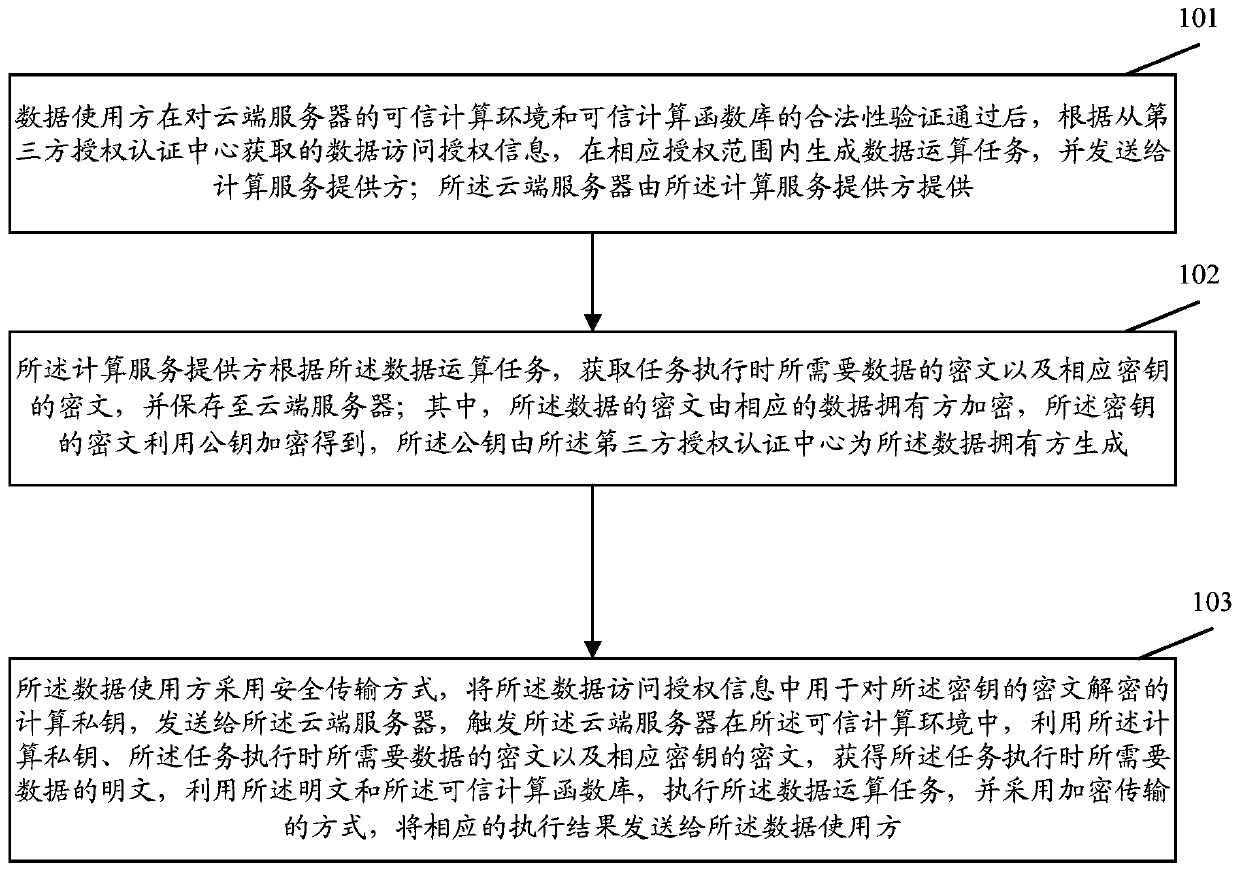
[0056] figure 1 It is a schematic flow chart of the method of the embodiment of the present invention. Such as figure 1 As shown, the trusted computing method implemented in this embodiment mainly includes the following steps:
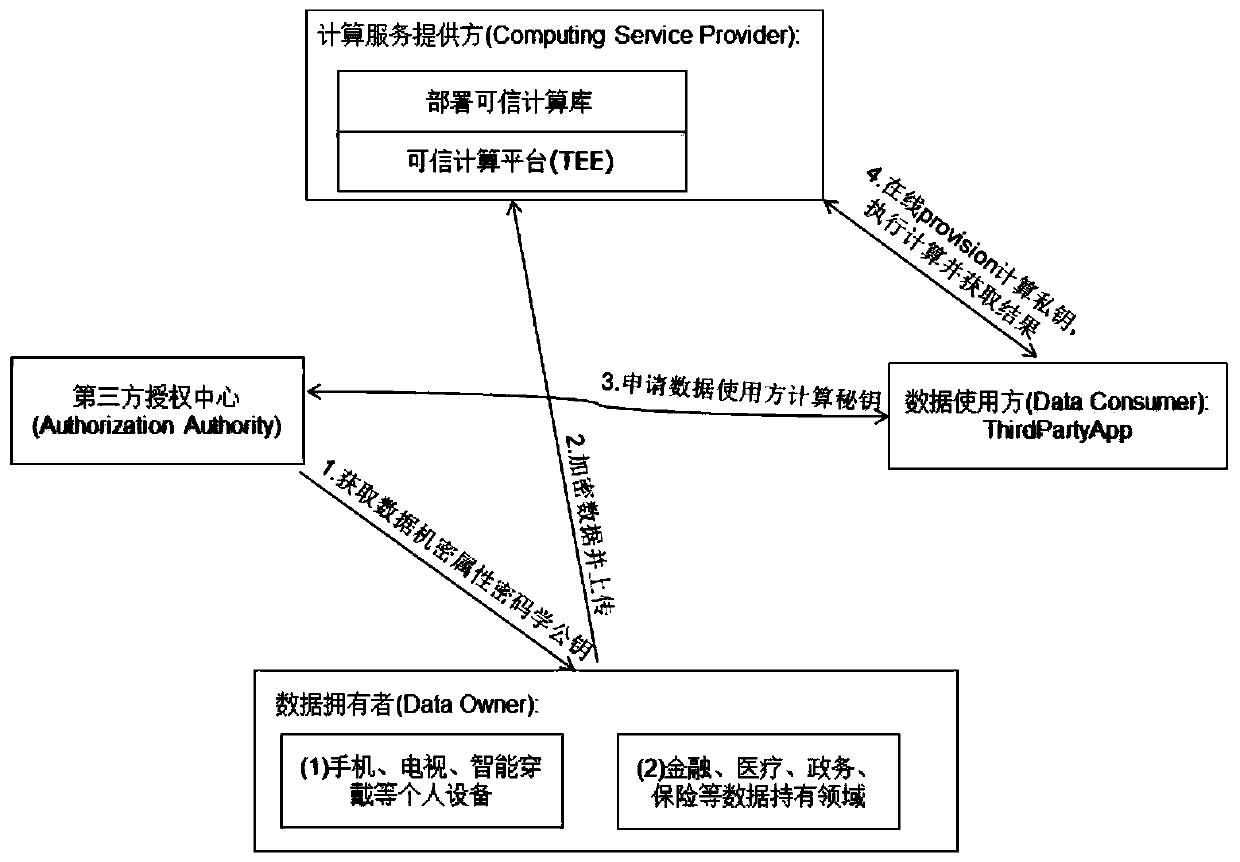
[0057] Step 101: After passing the legality verification of the trusted computing environment of the cloud server and the trusted computing function library, the data user generates data calculations within the corresponding authorized scope according to the data access authorization information obtained from the third-party authorized authentication center. The task is sent to the computing service provider; the cloud server is provided by the computing service provider.
[0058] In this step, after the data user deter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com