Novel heterogeneous identity alliance user reputation value transmission method based on ring signature technology
A technology of ring signature and reputation value, applied in the field of user reputation value transfer of heterogeneous identity alliance, can solve the problems of transfer, user behavior privacy exposure, trust value transfer and update process without more description, to ensure validity, The effect of protecting behavioral privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
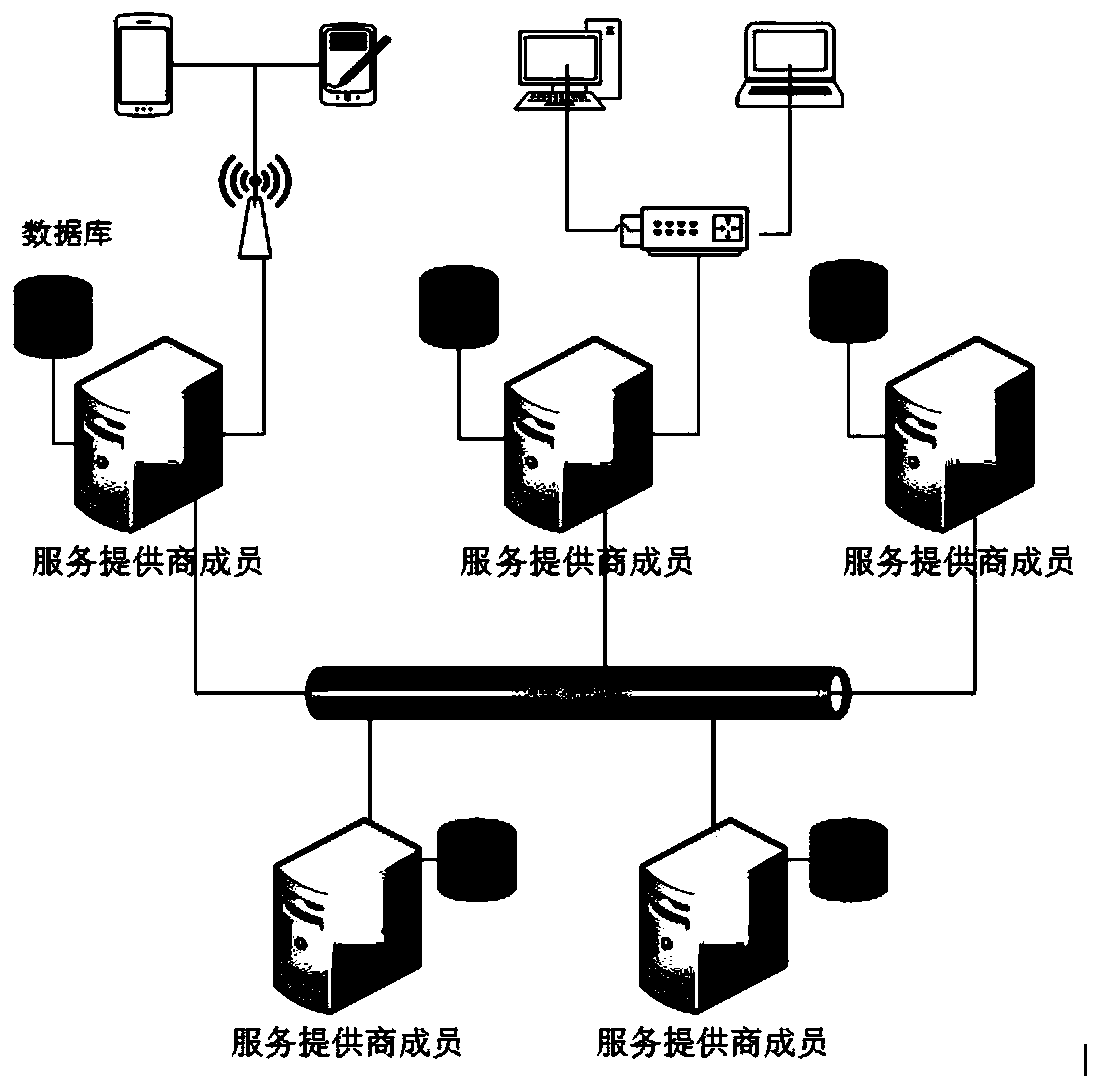
[0100] The structure of the trust management system of heterogeneous identity federation is as follows: figure 2 shown. SP members provide various services to federation users. The service provider members (SP members) of the identity alliance are connected through a chain of trust based on blockchain technology, and only service provider members of the identity alliance can add new blocks to the trust chain.
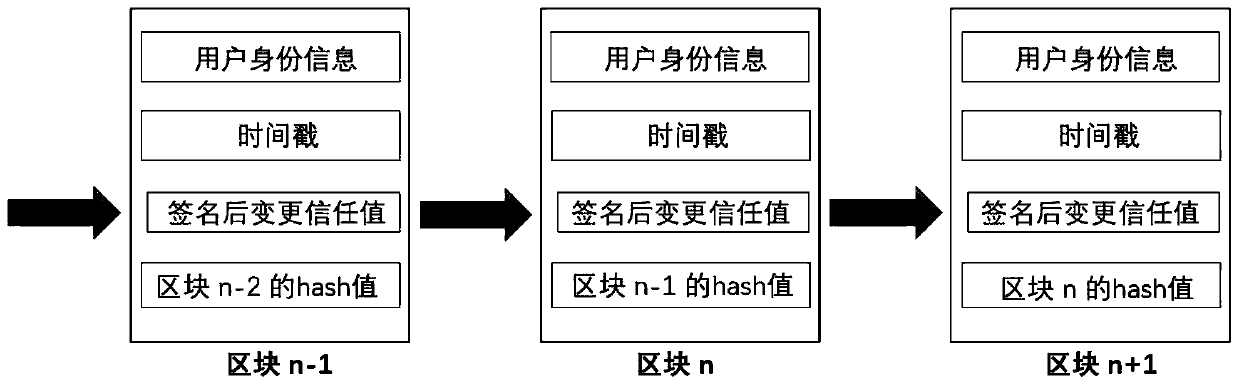
[0101] When a user's trust value is updated, the service provider member of the corresponding identity federation will create a new block and add it to the end of the trust chain. An example of a chain of trust is image 3 shown.
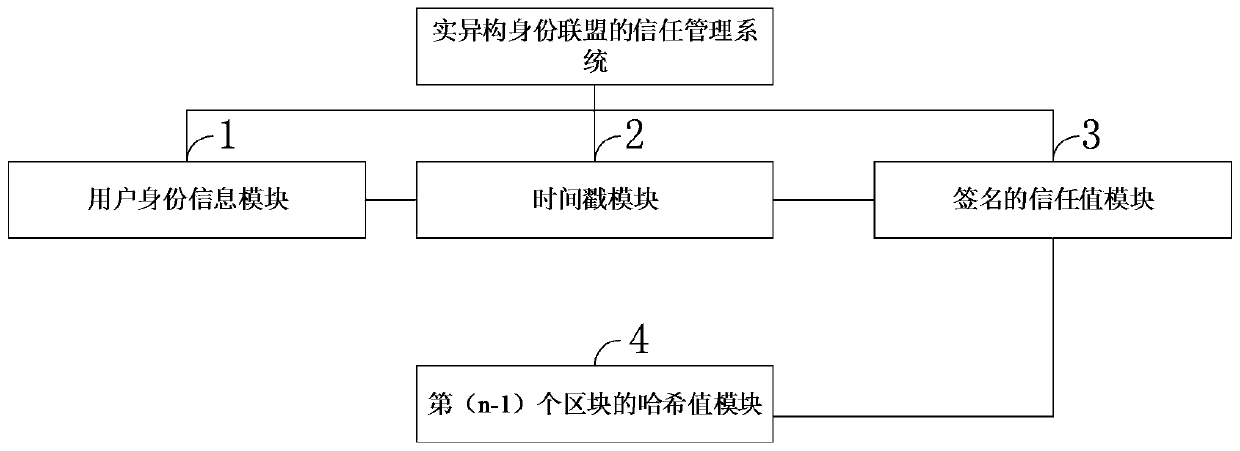
[0102] The chain of trust consists of blocks connected in series. The nth block consists of four parts.
[0103] ·User identity information: the user who declares that the trust value will be modified.
[0104] Timestamp: is the timestamp of the time the block was added.
[0105] Signed trust value: The trust value calculated by the a...
Embodiment 2
[0115] The embodiment of the present invention provides a novel ring signature technology-based heterogeneous identity federation user reputation value transfer method, including:
[0116] (1) Initialization
[0117] Let k be the security parameter. Let a positive integer N be the product of two k-bit odd prime numbers (p and q). Choose a fixed value l, let e be a randomly selected positive integer, ie 2 l l+1 , less than calculate Define the hash function used for encryption as follows: H 1 : {0, 1} * → Z N * , H 2 : {0, 1} * → {0, 1} l .
[0118] The initial parameters of the final generation system = {k, l, N, e, H 1 , H 2}.
[0119] The system keys are: {p, g, d}.
[0120] (2) Key generation:
[0121] In this step, a public key-private key pair (SH i , H(ID i )) where SK i =(H(ID i )) d as ID i service provider members of the Alliance.
[0122] (3) signature
[0123] (3.1) Let U={ID 1 ,...,ID n}Provides a collection of member identity informatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com