A Secure Coprocessor Structure Based on RISC-V Instruction Extension
A technology of RISC-V and instruction expansion, which is applied in the direction of concurrent instruction execution, electronic digital data processing, computer security devices, etc., and can solve problems such as poor universality and universality, existence of authorization and universality, and efficiency that cannot meet expectations. , achieve high efficiency and versatility, save resource overhead, and achieve high cost-effective effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] In the description of the present invention, it should be noted that unless otherwise specified and limited, the terms "installation", "connection" and "connection" should be understood in a broad sense, for example, it can be a fixed connection or a detachable connection. Connected, or integrally connected; it can be mechanically connected or electrically connected; it can be directly connected or indirectly connected through an intermediary, and it can be the internal communication of two components. Those of ordinary skill in the art can understand the specific meanings of the above terms in the present invention in specific situations.
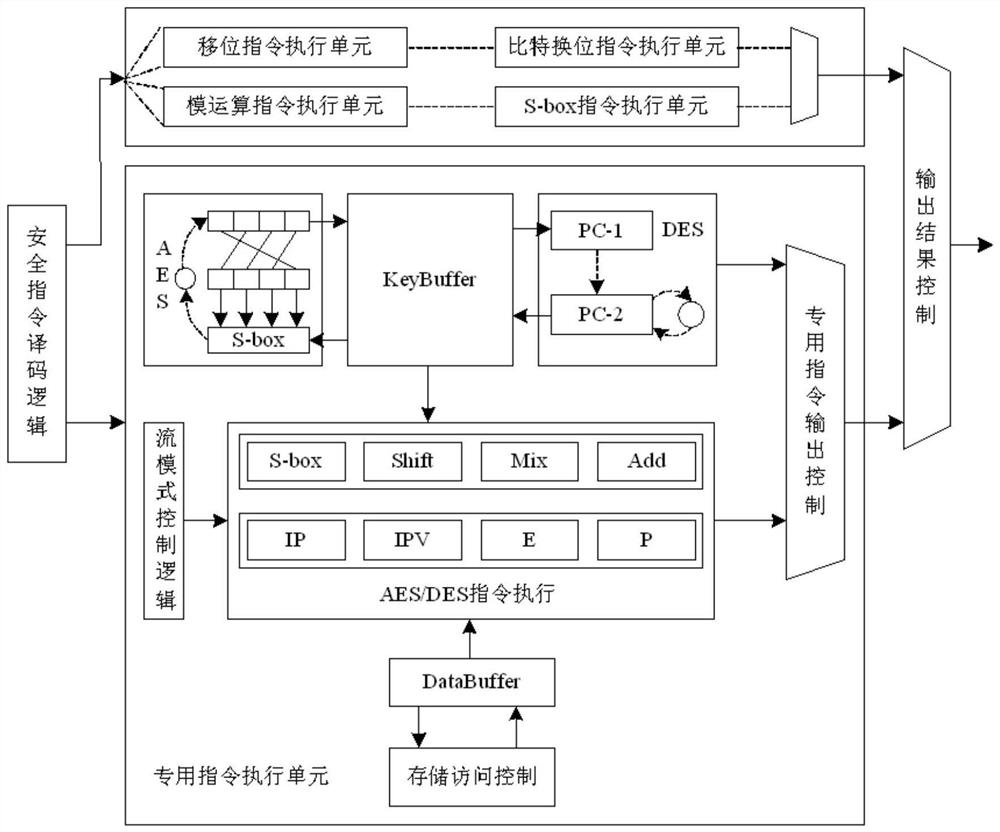
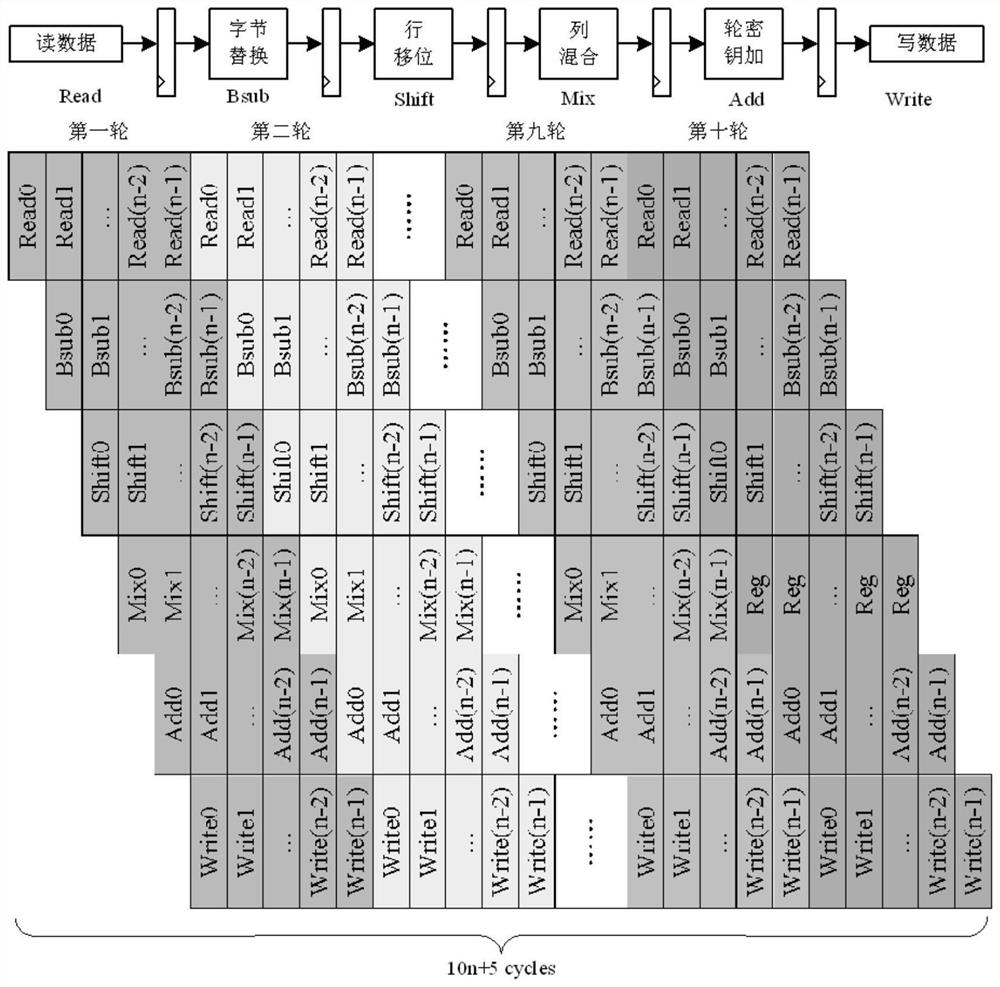
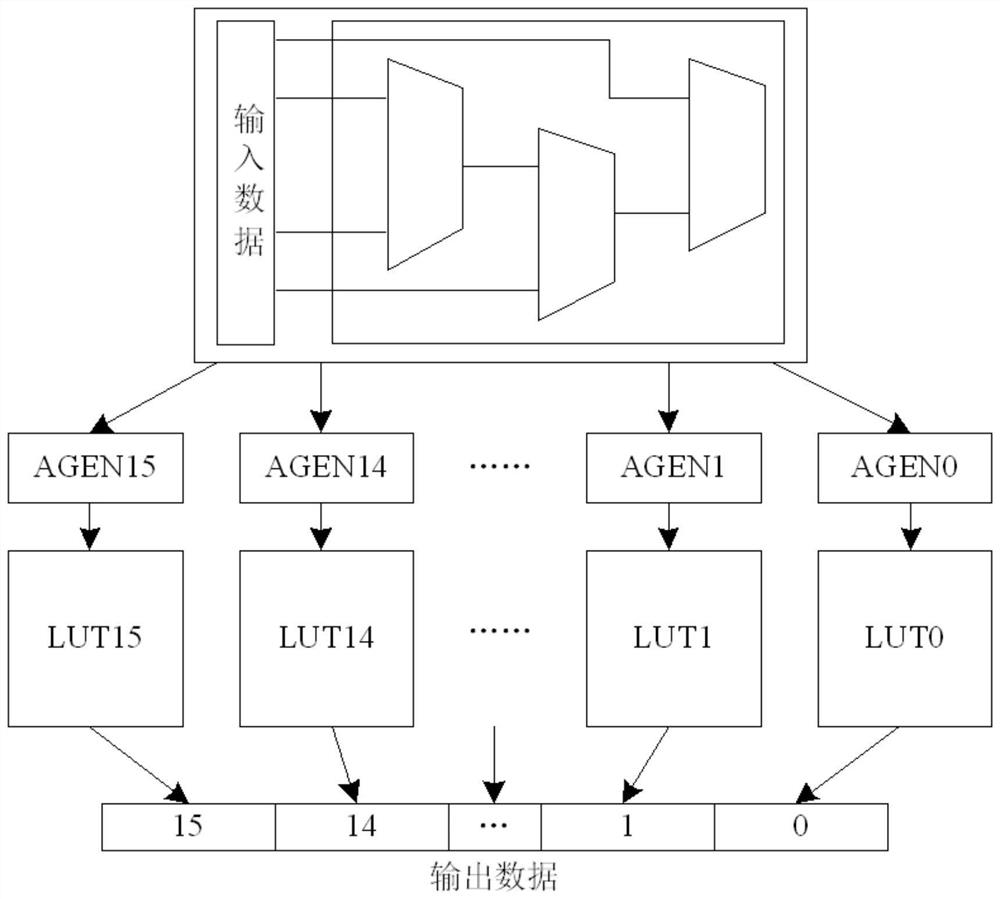
[0047] The present invention provides a security coprocessor structure based on RISC-V instruction expansion, adopts the user expandable capability provided by the current open source instruction set RISC-V, and summarizes and extracts various mainstream symmetric packet encryption and decryption algorithms, Construct a security cop...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com