Cracking method of encryption equipment
A technology of encryption equipment and equipment, which is applied in the direction of metal processing equipment, welding equipment, internal/peripheral computer component protection, etc., can solve the problems of long time consumption, no duplication, high cost, etc., achieve low cost, reduce cost and time, and improve The effect of cracking success rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The implementation of the present invention is described below through specific examples and in conjunction with the accompanying drawings, and those skilled in the art can easily understand other advantages and effects of the present invention from the content disclosed in this specification. The present invention can also be implemented or applied through other different specific examples, and various modifications and changes can be made to the details in this specification based on different viewpoints and applications without departing from the spirit of the present invention.
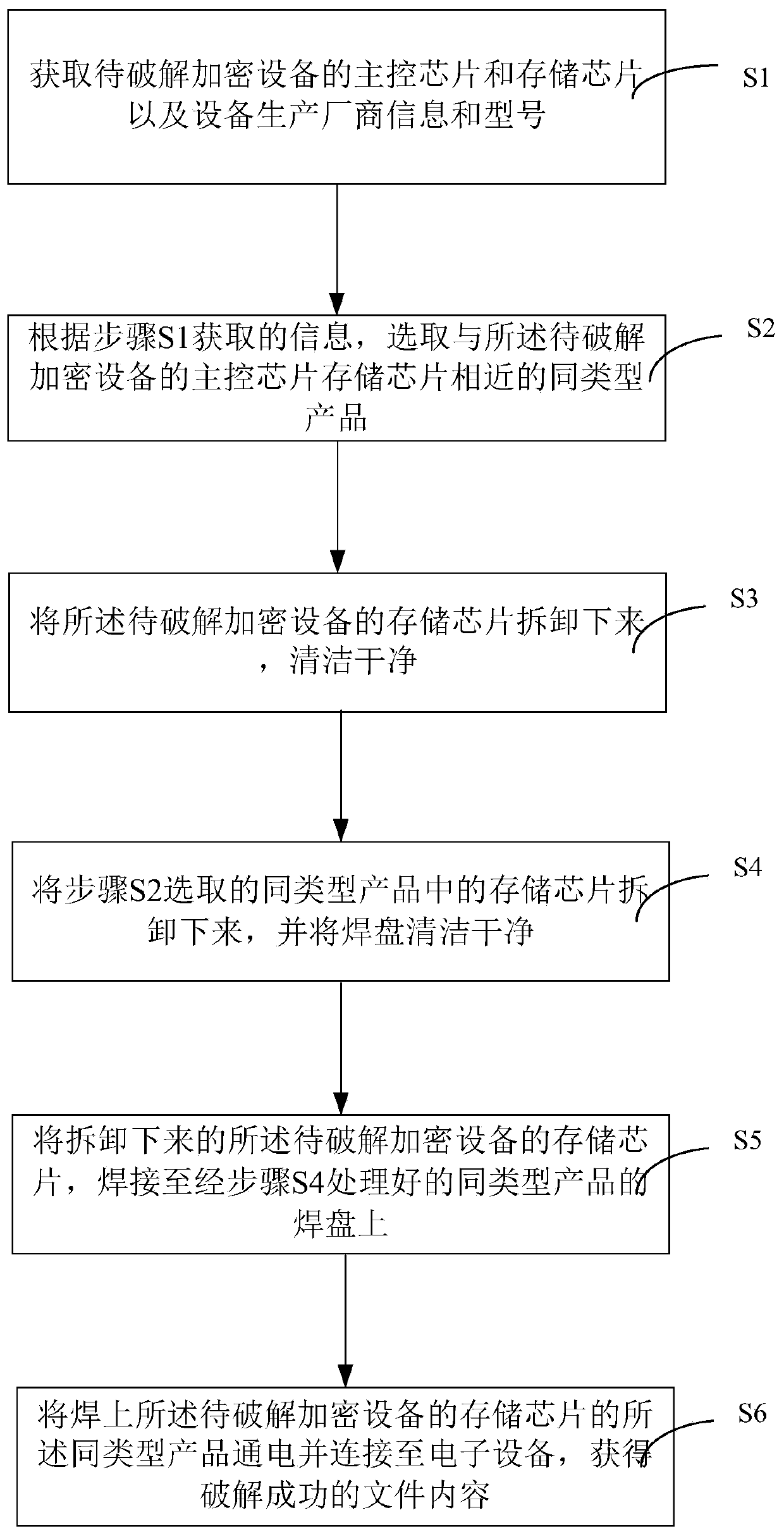
[0026] figure 1 It is a flow chart of steps of a cracking method of an encryption device according to the present invention. Such as figure 1 As shown, a method for cracking an encryption device of the present invention comprises the following steps:
[0027] Step S1, obtaining the main control chip and storage chip of the encrypted device to be cracked, as well as the information of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com