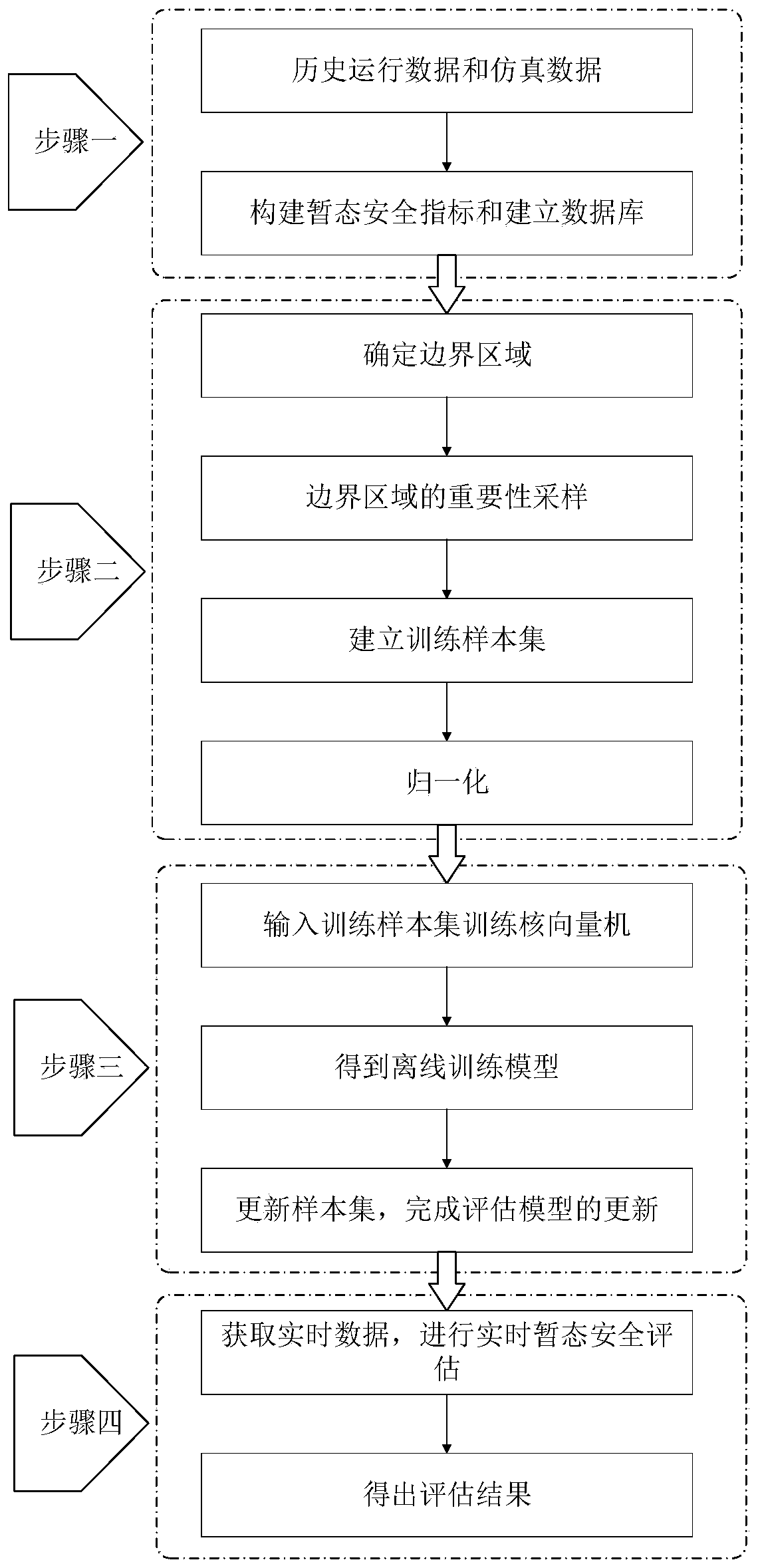
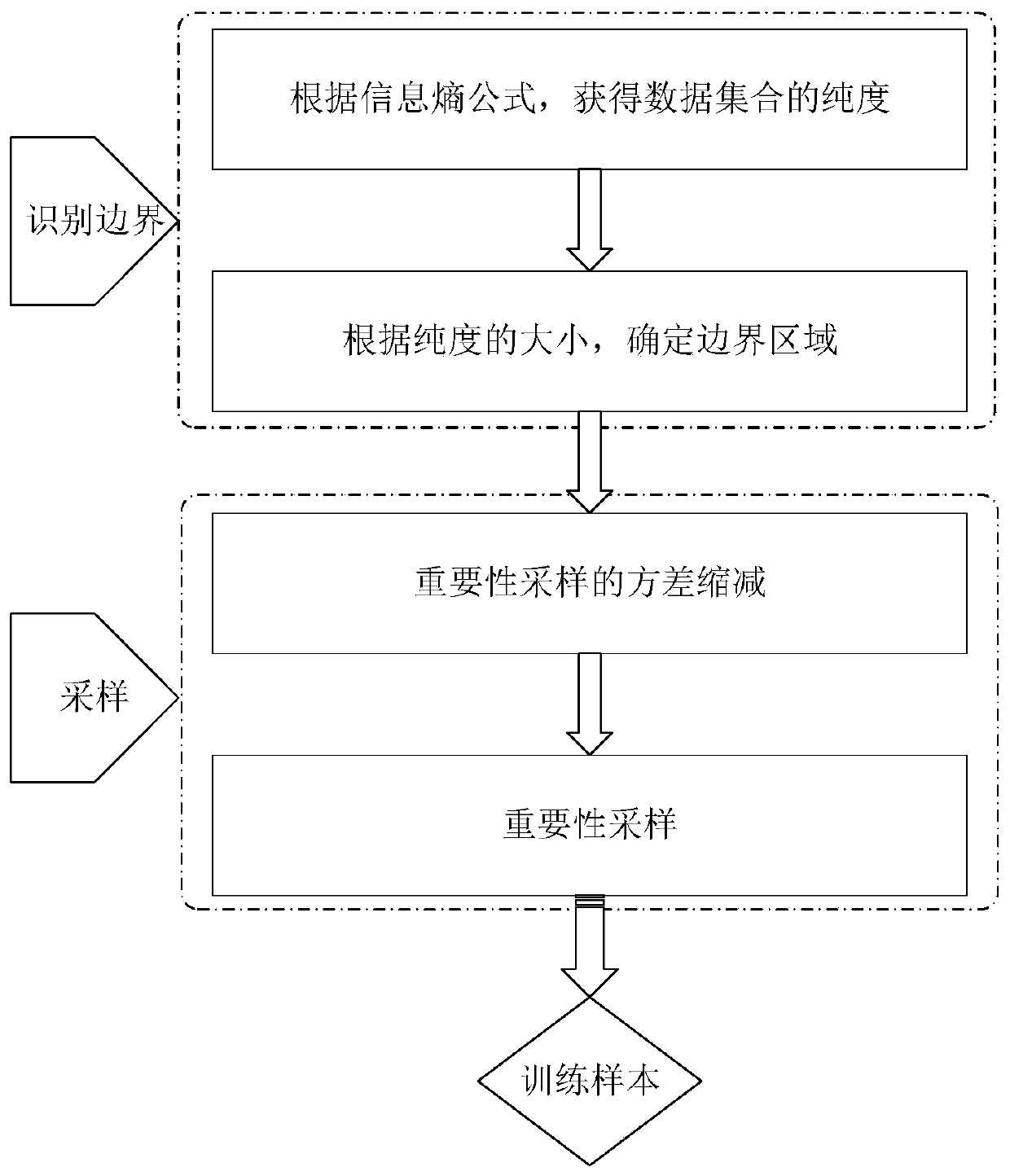
Transient security evaluation method based on boundary region importance sampling and kernel vector machine
A technology of importance sampling and boundary areas, applied in nuclear methods, computer components, instruments, etc., can solve time-consuming problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
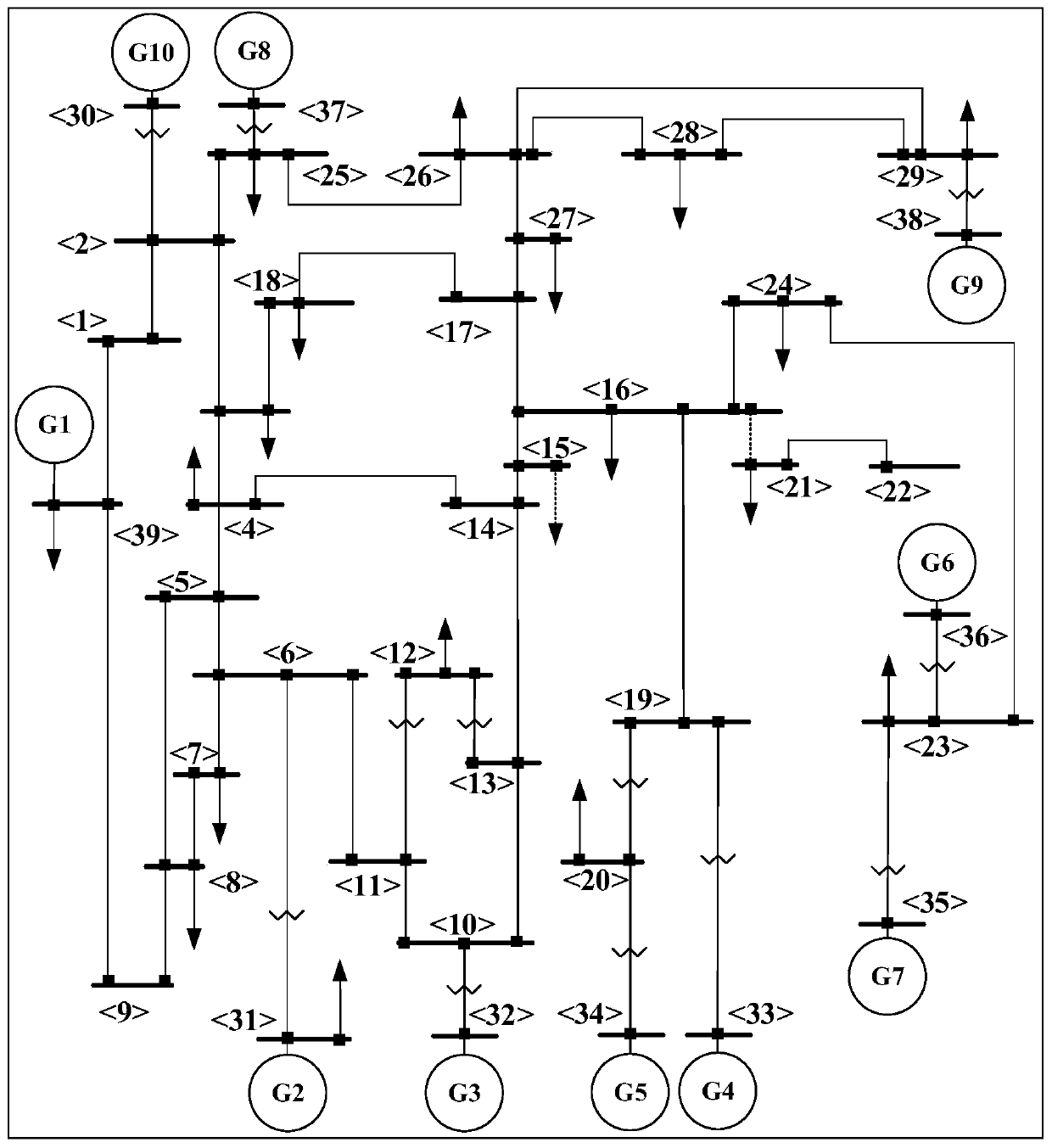
[0120] This inventive example uses the IEEE39 node system. Such as image 3 As shown, the test system involves 39 nodes, 10 generators, and 46 transmission lines. The reference power is 100MVA, and the reference voltage is 345kV. It is assumed that synchro-vector measurement units are installed on all buses in order to collect large data sets. To generate a reasonable dataset, the operating conditions of the test system were varied randomly. Consider 10 different load levels (80%, 85%, 90%, 95%, 100%, 105%, 110%, 115%, 120%, 125%) and change the generator output accordingly. On this basis, the method of variable load and variable generation is used to solve the power flow problem of the power system. The contingencies considered are mainly three phase-to-earth faults on each busbar, and three locations on each transmission line (25%, 50% and 75% of the line length). The simulation assumes that a specific fault occurs at 0.1 seconds and is cut off at 0.3 seconds (or 0.35 s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com