Training method and device for anomaly detection model based on differential privacy
An anomaly detection and differential privacy technology, applied in the computer field, can solve the problems of leaking training samples, insufficient generalization ability, insufficient robustness, etc., and achieve the effect of improving robustness and predictive performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
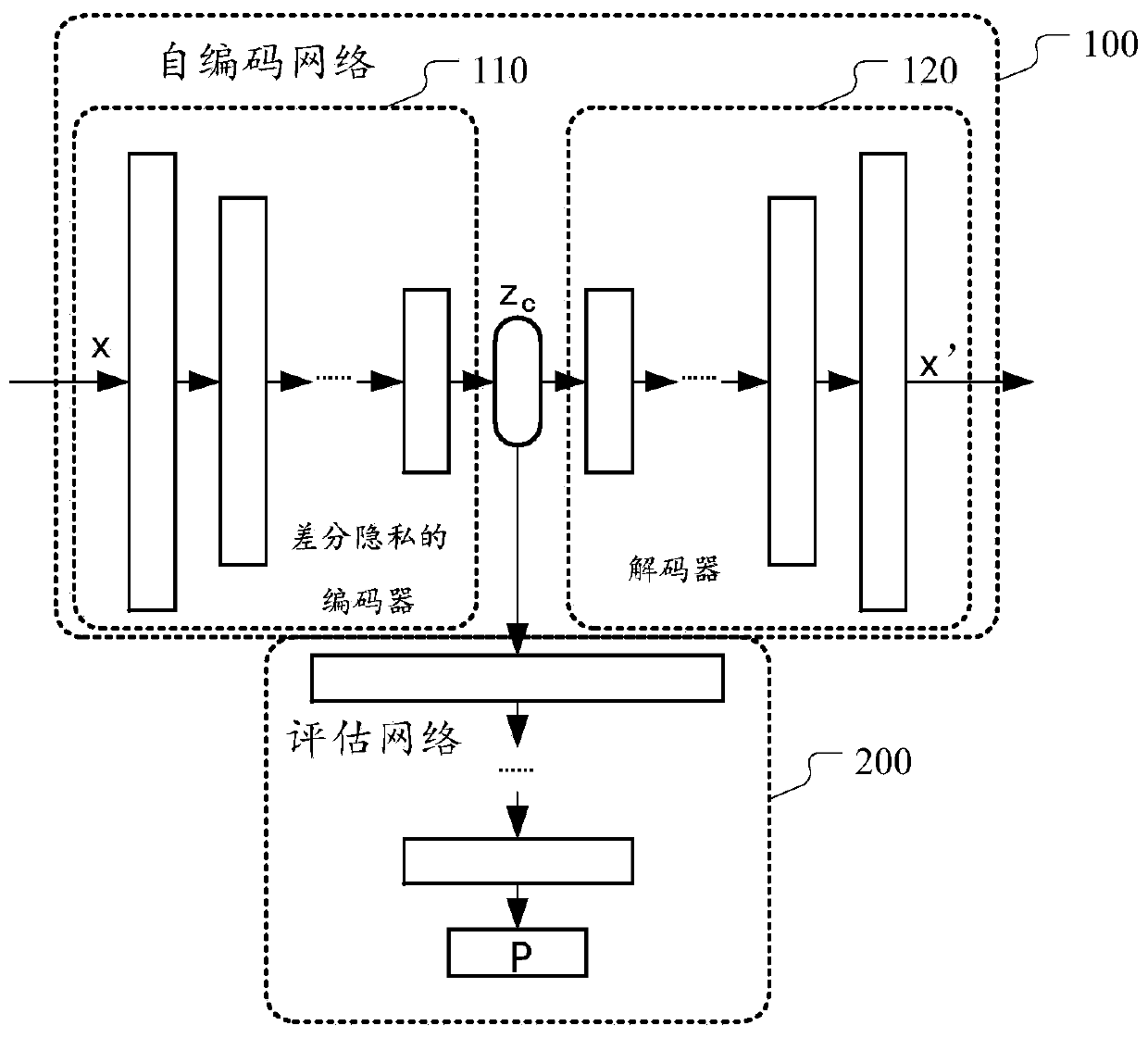
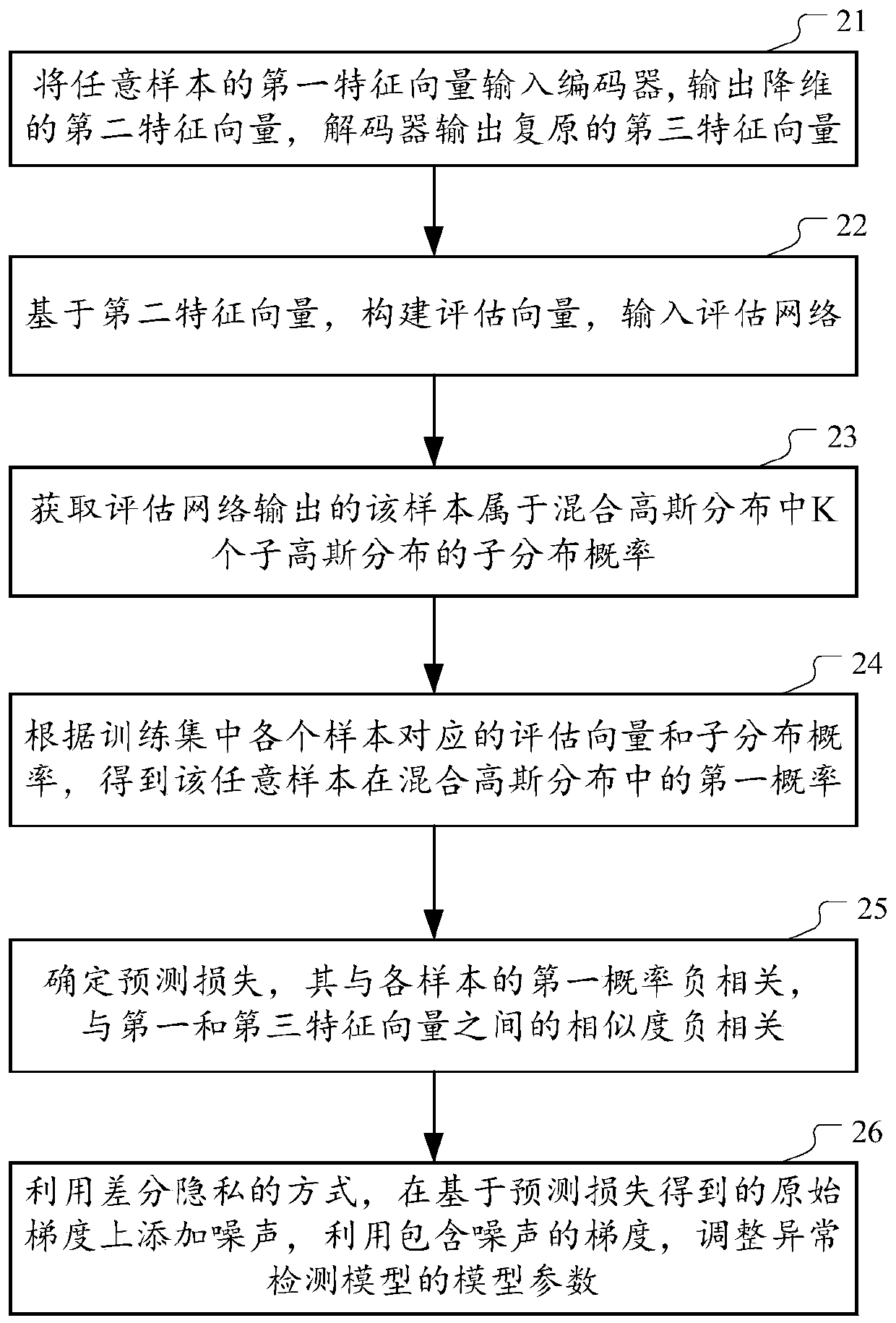
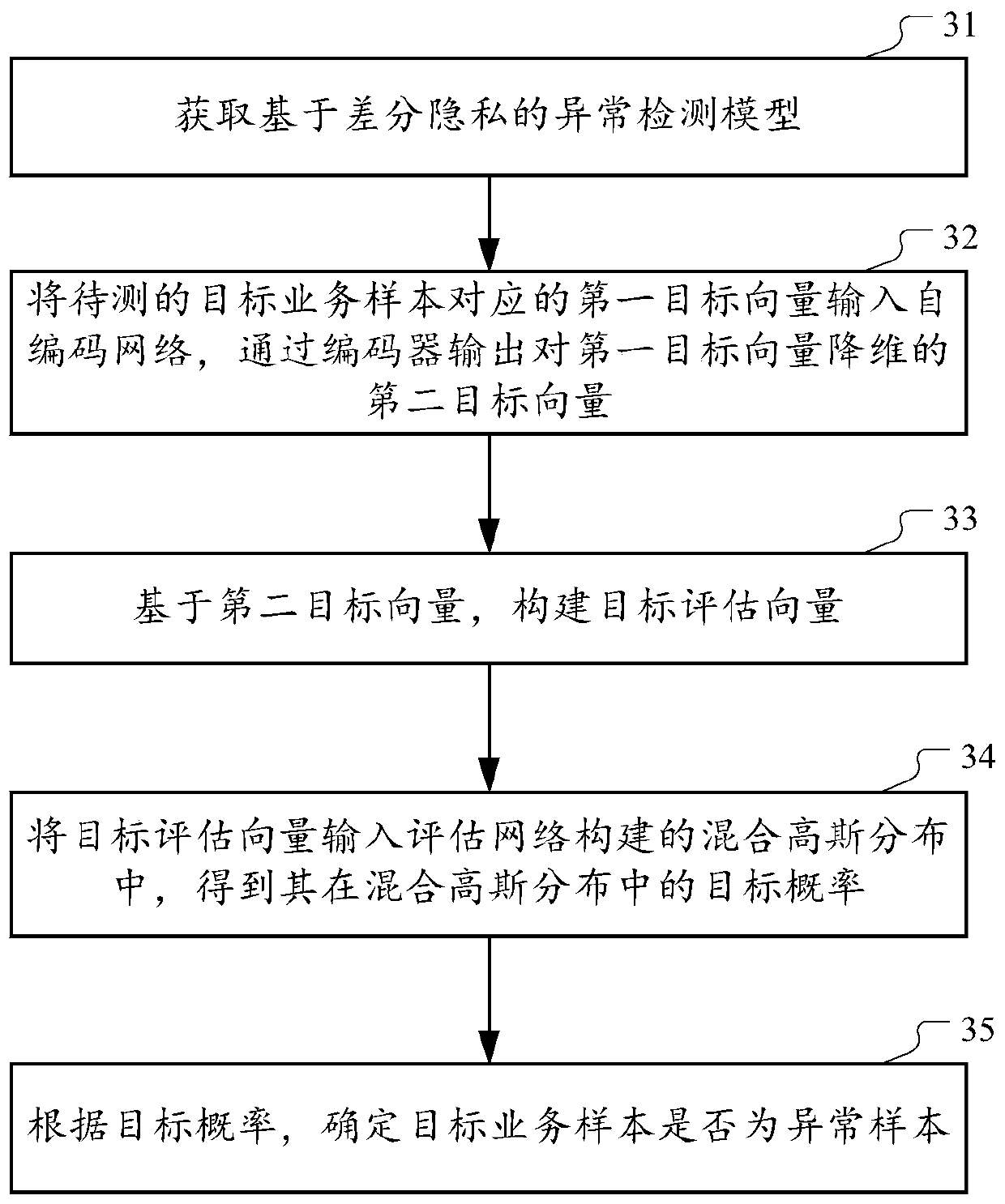
[0051] figure 1 A schematic diagram of the architecture of the anomaly detection model according to the technical conception of this specification is shown. Such as figure 1 As shown, the anomaly detection model generally includes an autoencoder network 100 and an evaluation network 200 , and the autoencoder network 100 includes an encoder 110 and a decoder 120 . The encoder 110 is used to encode the high-dimensional feature vector x of the input service sample into a low-dimensional vector z c , the decoder 120 is based on the low-dimensional vector z c , output the decoded vector x' for restoring the high-dimensional feature vector x. The trained self-encoder network, the low-dimensional vector z obtained by the encoder c It can well characterize the core features of the original high-dimensional feature vector x and play a role in vector dimensio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com