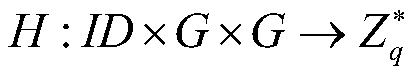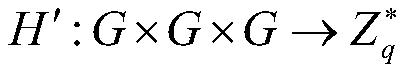Certificateless key packaging method for resisting leakage of bounded secret information
A technology of secret information and encapsulation method, applied in the field of key encapsulation system, can solve the problems of weak resistance to leakage attacks, long ciphertext length, low computational efficiency and practicability, etc., and achieves high security, high security, The effect of improving computing efficiency and practicality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
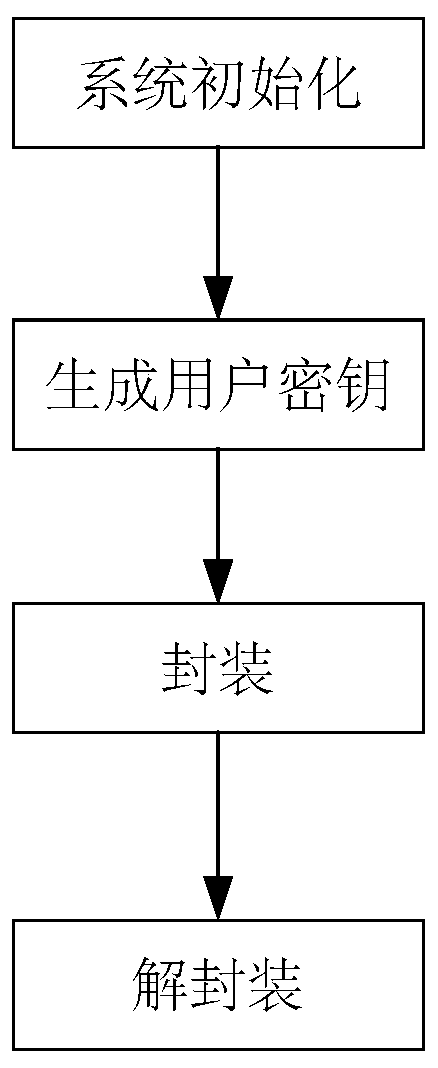
[0064] exist figure 1 Among them, the certificateless key encapsulation method against bounded secret information leakage in this embodiment consists of the following steps.
[0065] (1) System initialization
[0066] 1) Run the group generation algorithm to generate the corresponding tuple (q, G, P), where G is an additive cyclic group whose order is a large prime number q, and P is the generator of the group G.
[0067] 2) Choose a safe hash function H, hash function H', password diffraction function KDF:
[0068]
[0069]
[0070]
[0071] Where ID is the identity of the user, is an integer group of order q.
[0072] 3) From the group of integers of order q Randomly select a finite integer a as the master private key of the system and keep it secret, and set the master public key P of the system pub , the global parameter params, and expose:
[0073] P pub = a·P
[0074] params={q,G,P,P pub ,H,H′,KDF}.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com