Anonymous identity-based broadcast encryption method and system
A broadcast encryption and identity technology, applied in the field of cloud computing security, can solve the problem that the set of target receivers cannot decrypt the algorithm, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to make the purpose, technical solutions and advantages of the embodiments of the present application clearer, the technical solutions in the embodiments of the present application will be clearly and completely described below in conjunction with the drawings in the embodiments of the present application. It should be noted that like numerals and letters denote similar items in the following figures, therefore, once an item is defined in one figure, it does not require further definition and explanation in subsequent figures.
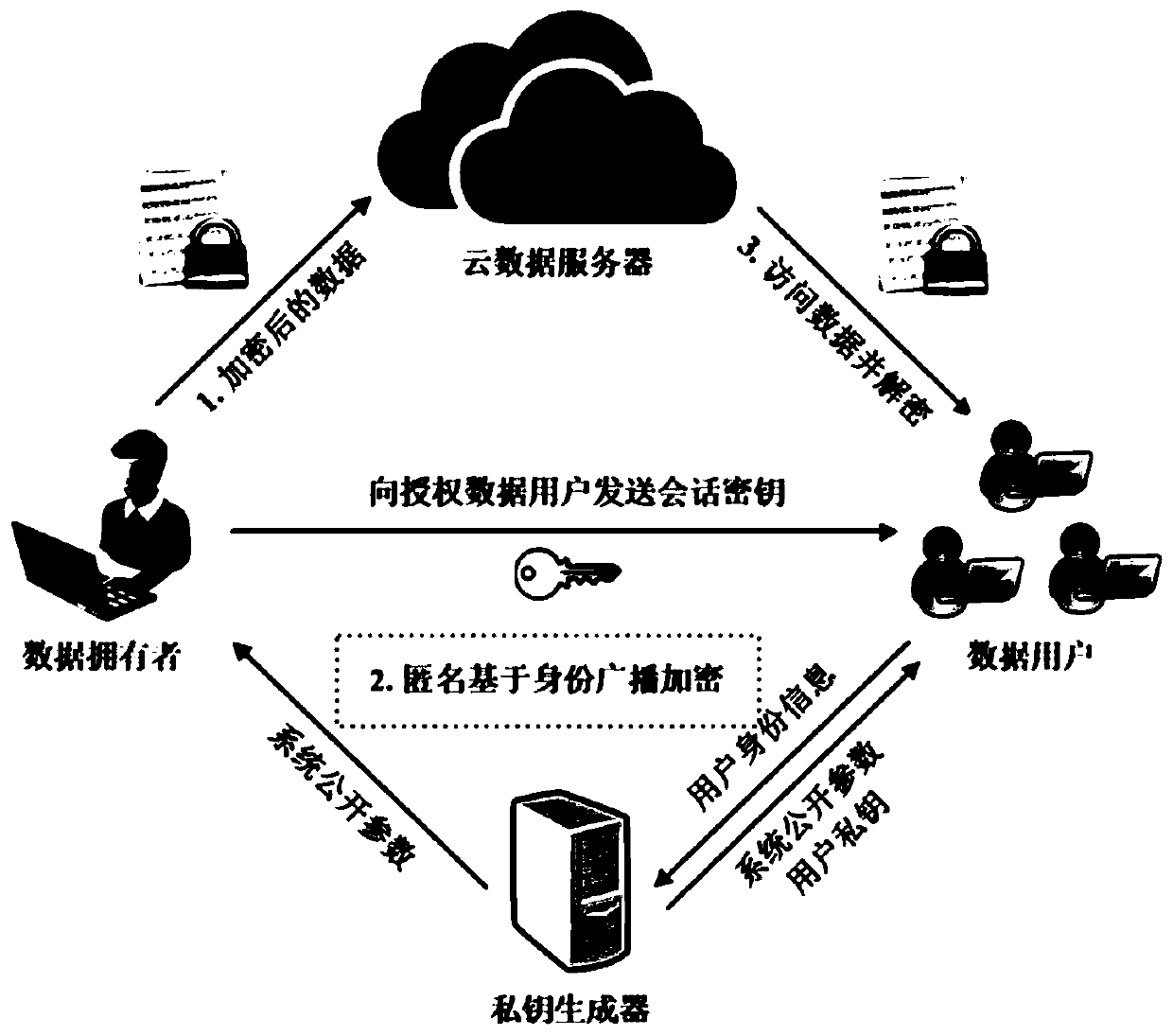
[0035] Such as figure 1 As shown, the present invention discloses an anonymous identity-based broadcast encryption method, which specifically includes:
[0036] Step S1: Input the security parameter λ, and the algorithm outputs the system public parameters params and the system master key MK. The private key generation center PKG secretly holds the system master key MK and releases system public parameters params;
[0037] Step S2: In...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com