Symmetric encryption system and method for vehicle bluetooth key identity authentication mode
A bluetooth key and identity authentication technology, which is applied in the field of symmetric encryption system of vehicle bluetooth key identity authentication, can solve the problems of information leakage, illegal users or attackers unable to carry out replay attacks, unable to restore plaintext of identity information, etc., to achieve improved Security, avoiding plaintext leaks, avoiding missed checks, and the effects of replay attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
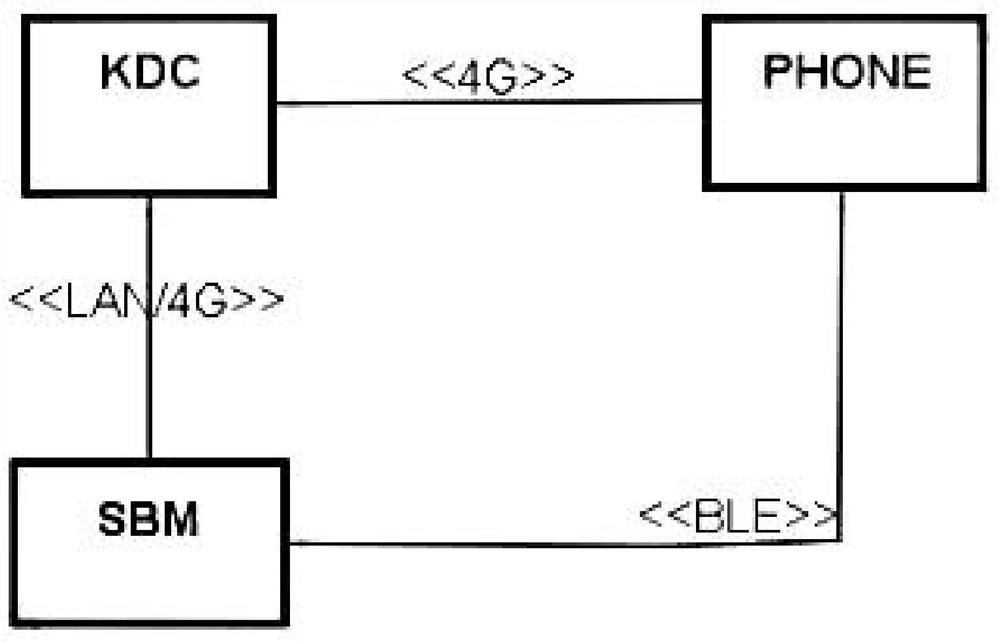
[0038] This embodiment discloses as figure 1 A symmetric encryption system of a vehicle bluetooth key identity authentication method is shown, the system is provided with a smart bluetooth module SBM and a bluetooth key BlueKey, and the smart bluetooth module SBM and the bluetooth key BlueKey realize data transparent transmission through low-power bluetooth BLE; When the vehicle is produced, the smart bluetooth module SBM is deployed on the vehicle and connected to the key distribution center KDC through LAN or 4G network to obtain and generate the vehicle master key CMPK; after sales, the Bluetooth key BlueKey is distributed through the 4G network connection key The central KDC generates the digital key VCK after acquisition, and sends back the Bluetooth key BlueKey with VCKINO information. There is a functional relationship between the generated vehicle master key CMPK and the digital key VCK.
[0039] There is a functional relationship between the vehicle master key CMPK and ...
Embodiment 2
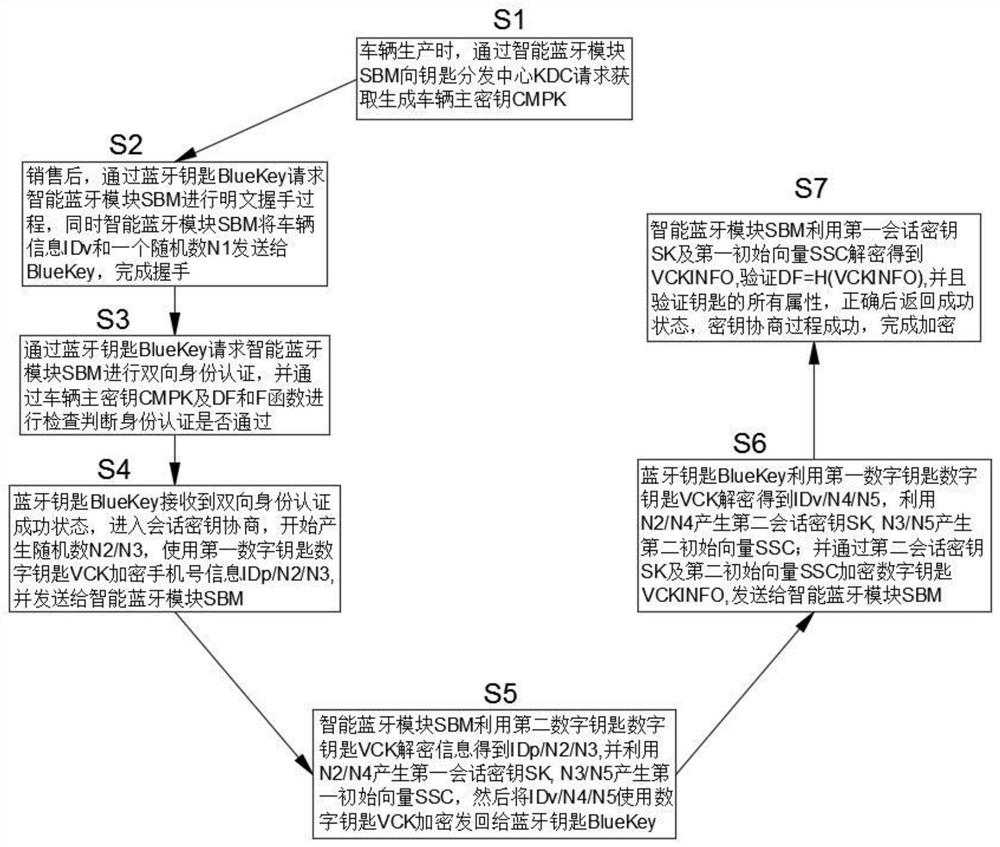
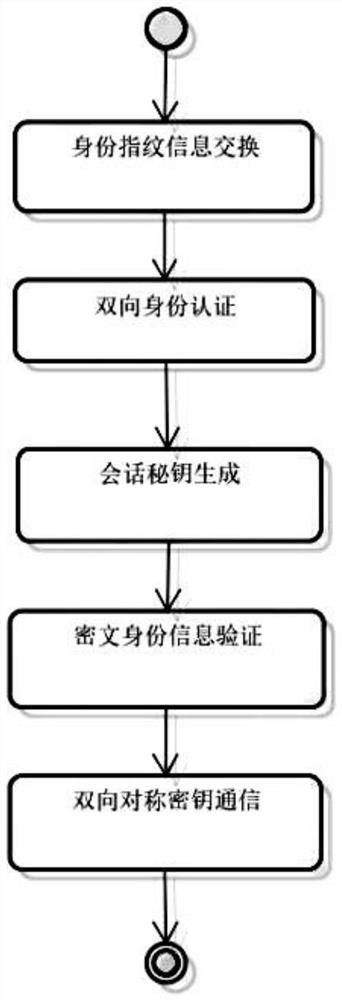
[0045] This embodiment discloses as figure 2 A symmetric encryption method of a vehicle bluetooth key identity authentication method shown, comprising the following steps:
[0046] When the S1 vehicle is produced, the smart bluetooth module SBM requests the key distribution center KDC to obtain and generate the vehicle master key CMPK;
[0047] After S2 is sold, the bluekey bluekey requests the smart bluetooth module SBM to carry out the handshake process in clear text, and the smart bluetooth module SBM sends the vehicle information IDv and a random number N1 to BlueKey to complete the handshake;
[0048] S3 requests the smart Bluetooth module SBM to perform two-way identity authentication through the Bluetooth key BlueKey, and checks through the vehicle master key CMPK and DF and F functions to determine whether the identity authentication is passed;
[0049] S4 Bluetooth key BlueKey receives the successful state of two-way identity authentication, enters the session key n...
Embodiment 3
[0064] This embodiment discloses a system, which is designed to have a VCK=F(CMPK,DF), DF=H(VCKINFO) relationship between CMPK and VCK, where F is a one-way hash message authentication code (HMAC) function, and H is a one-way to the hash function;
[0065] On the production line of the car factory, the SBM and the KDC are connected through a LAN or 4G network. The SBM requests to obtain the vehicle master key (CMPK), and the KDC agrees to the request to generate a CMPK.
[0066] After the car is sold, the Bluetooth key BlueKey and KDC are connected through 4G network, BlueKey requests the digital key (VCK), KDC agrees to the request, generates VCK, and sends it back to BlueKey with VCKINO information.
[0067] VCKINFO information includes: VCKINFO:={user ID, authority, key start time, key end time, vehicle characteristics, user mobile phone characteristics}; key fingerprint information (ECDSA mode) {DF=SHA256(VkeyInfo), eDF=ECDSA(df )}
[0068] BlueKey and SBM are connected ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com