Security cloud password manager control system and method
A control method and manager technology, applied in the field of security authentication, can solve problems such as guessing attacks, unable to decrypt cloud password manager, unable to restore passwords, etc., to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
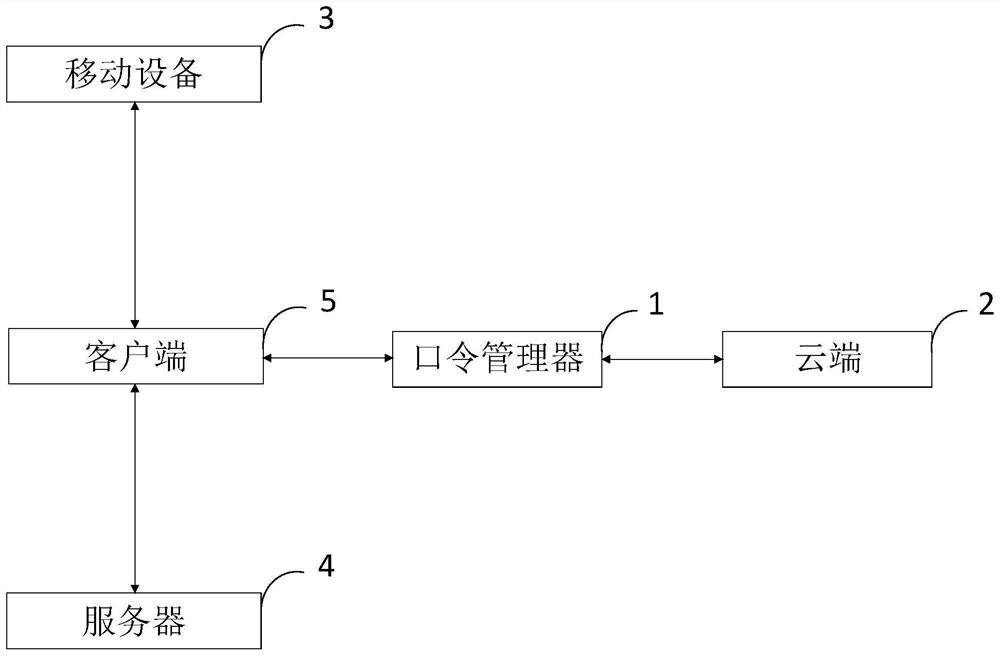
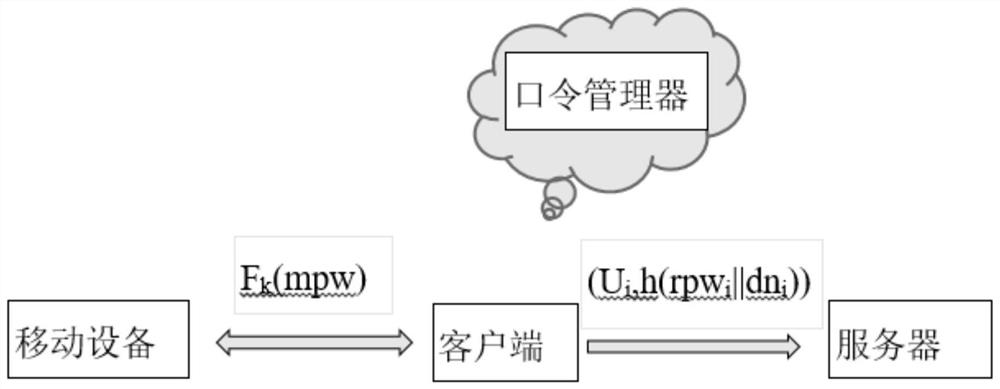
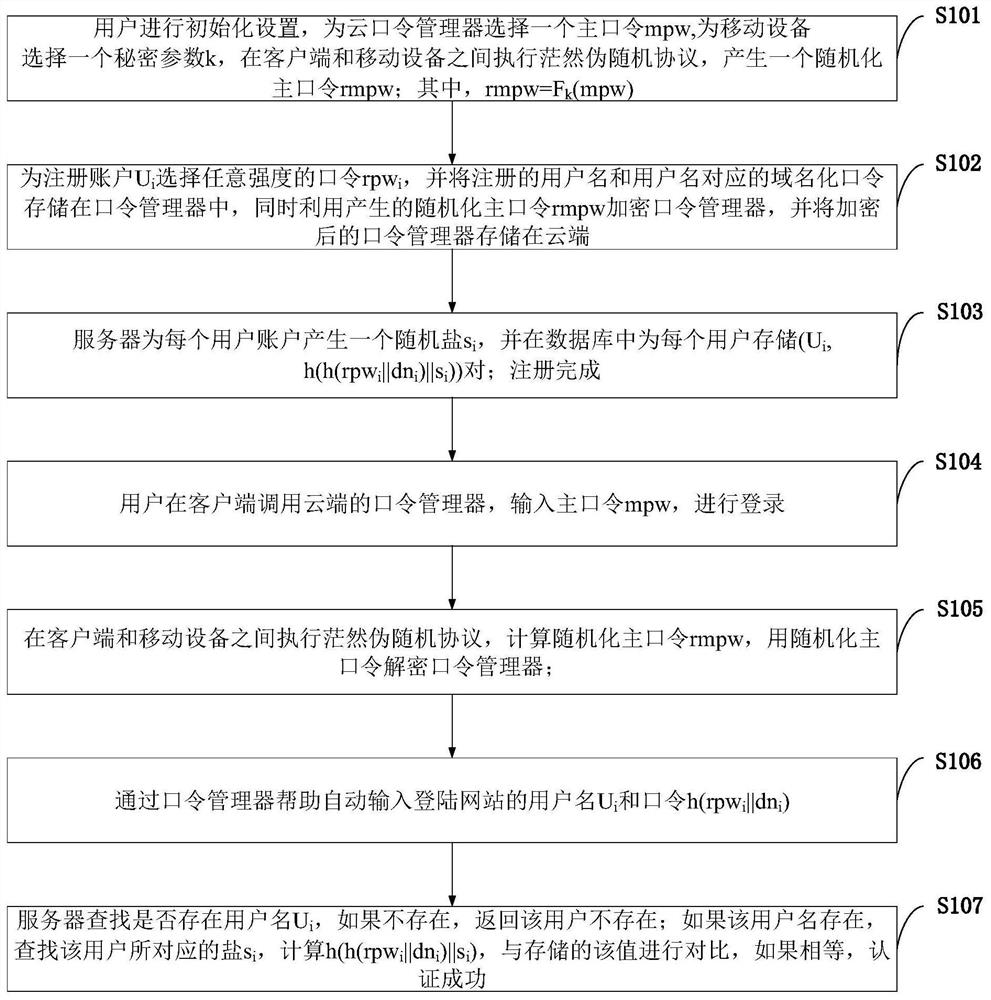
[0077] Password manager-used to store user names and corresponding passwords of various accounts of the user. Since the user does not need to memorize these stored passwords, they can be passwords of any strength. Master password - the only password that the user needs to remember. The master password is a password of general strength and only needs to be able to resist online guessing attacks. Randomized master password - a random password generated by the user's mobile device through blind calculation and extension of the master password. Randomize the master password with sufficient strength.
[0078] Blind Pseudo-Random Function - is the safe computation of F by both parties (sender and receiver) kA protocol for (x), where k and x are the inputs of the sender and receiver, respectively, and the sender can learn nothing from this interaction, and the receiver can know F k (x).
[0079] Domain-based password-a random password obtained by hashing the strong password select...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com