Social network topology model and construction method, user confidence and intimacy calculation method and telecommunication fraud intelligent interception system
A topology model and social network technology, which is applied in the field of telecommunications fraud intelligent interception system and social network topology model, can solve the problems of poor practicality, inability to reasonably distinguish fraudulent users from harassing ordinary users, and inapplicability to deal with massive call data, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 5 example
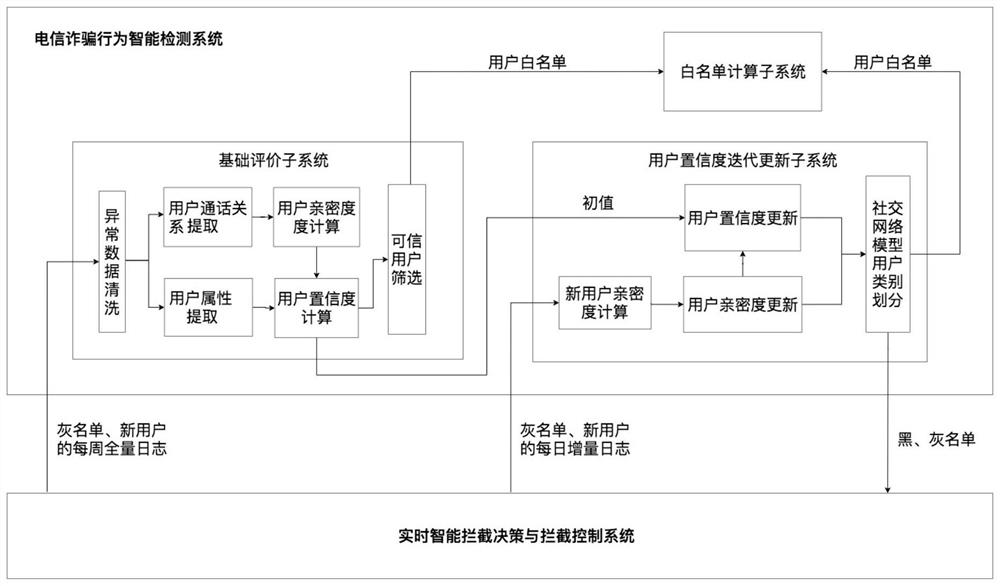
[0149] Optionally, to further improve the fifth embodiment above, the basic evaluation subsystem includes:
[0150] Abnormal data cleaning module, which is used to clean short numbers or numbers whose number of short-term calls is greater than the third threshold
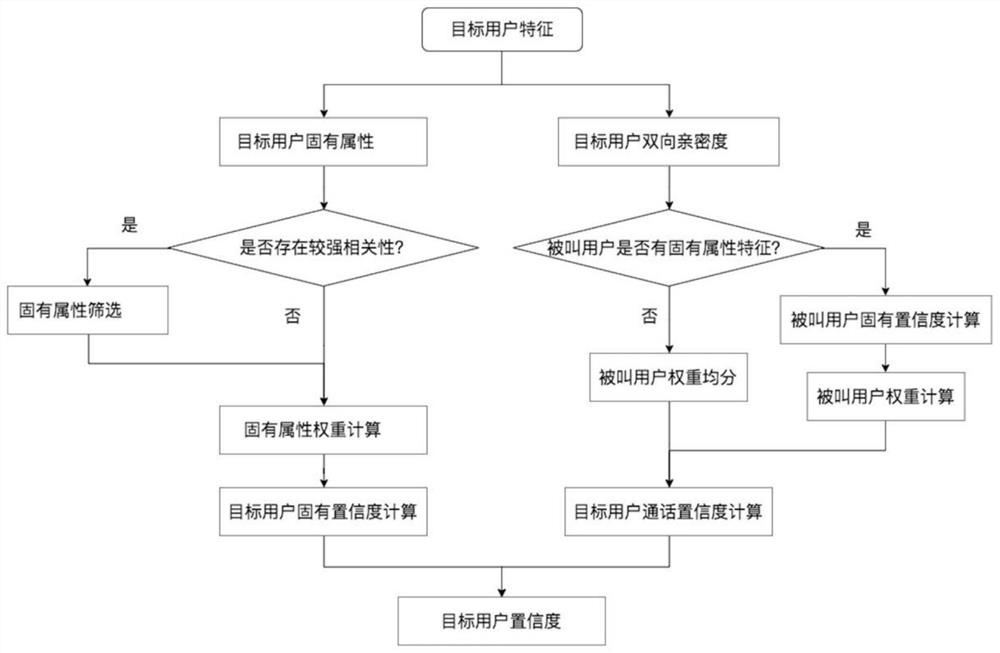
[0151] A user inherent attribute extraction module, which is used for statistics of user inherent attributes;
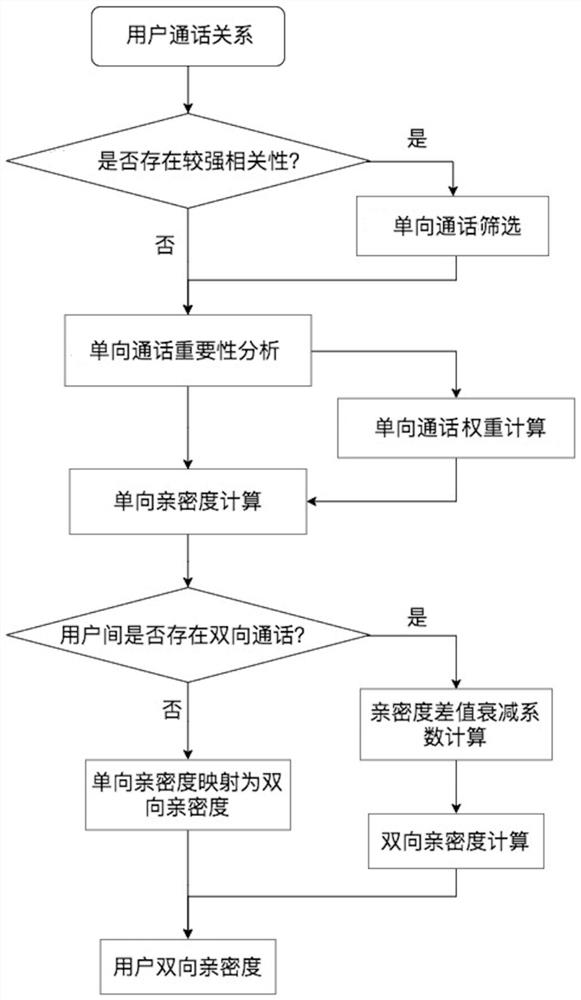
[0152] User call relationship extraction module, which is used to count the call relationship between users. The user call relationship is the data extracted according to the user's long-term call behavior, including: number of calls and call duration;
[0153] The intimacy calculation module between users is used to calculate the intimacy between users according to the user call relationship;
[0154] A user confidence degree calculation module, which is used to calculate the target user confidence degree according to the target user's inherent attributes and the target user's two-way intimacy;
[0155]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com