Log parameter anomaly detection method based on word embedding
An anomaly detection and parameter technology, applied in the Internet field, can solve the problems of model redundancy and lack of actual deployment ability, and achieve the effect of accurate detection ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention is described in further detail below in conjunction with accompanying drawing:
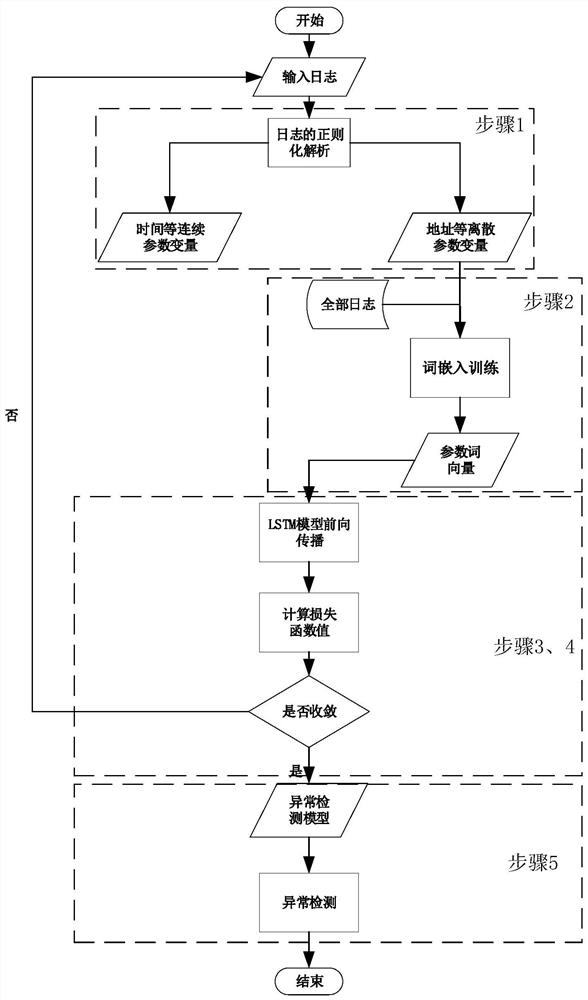
[0023] Such as figure 1 As shown, it is a flow chart of the log parameter abnormality detection method based on word embedding of the present invention, and the detection method of the present invention includes the following steps:
[0024] Step 1. Regularized analysis of parameters:
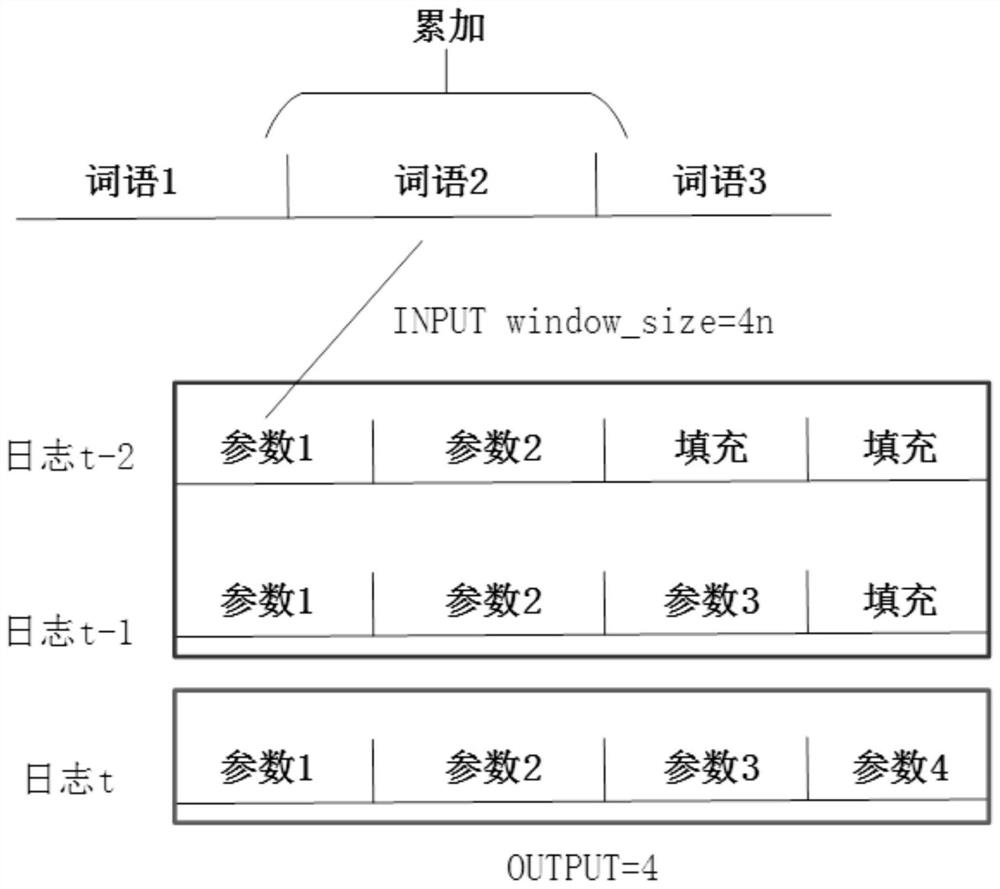
[0025] The log is plain text, with one part fixed and another part variable. For example, given the logs of "Newswitch connected from 127.0.0.1:54000" and "New switch connected from 127.0.0.1:54112", the four words "New", "switch", "connected" and "from" Treated as constant parts because they are always constant, called log templates. The remaining parts are called variable parts, because they assume different states in different situations. The variable part can be abstracted as an asterisk in the constant part, that is, "New switch connected from*", each variable part can be calle...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com