Safety control method, device and system
A technology of security control and security control module, applied in the field of electronics, can solve the problems of illegal attacks on office systems, inability to monitor user usage status in real time, information leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0035] This embodiment provides a safety control system.
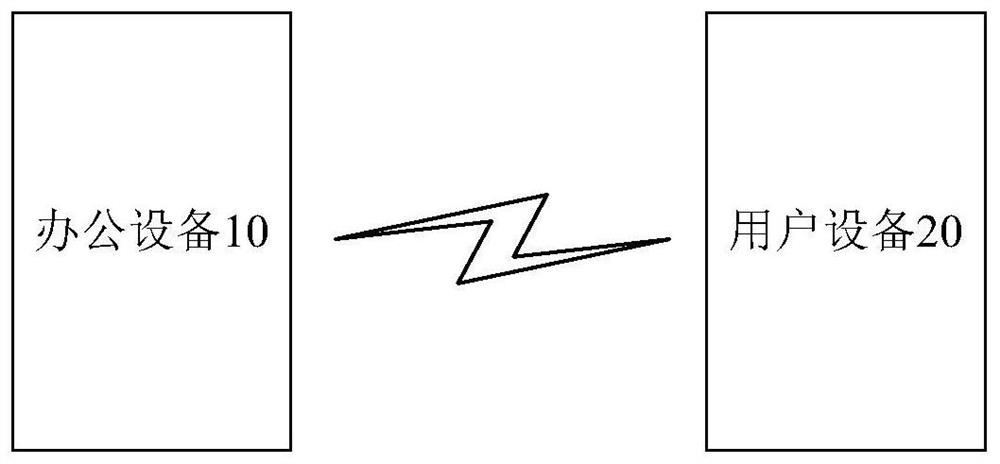
[0036] figure 1 A schematic diagram of the architecture of a safety control system provided in this embodiment, such as figure 1 As shown, the security control system mainly includes: office equipment 10 and user equipment 20 . In this embodiment, the office device 10 may be a computer, or a peripheral device with a certain processing capability, such as a security keyboard. The user equipment 20 may be an electronic device that is convenient for the user to carry with him, such as a mobile phone, or a smart card, etc., and the user equipment 20 may store a unique user identification, such as a user ID, through which the user's identity can be determined.
[0037] In this embodiment, the office equipment 10 establishes a short-range wireless communication connection with the user equipment 20 . In a specific application, wireless communication can be established between the office equipment 10 and the user equipment...
Embodiment 2
[0072] An embodiment of the present invention provides a safety control method, which can be implemented by the safety control system described in Embodiment 1.
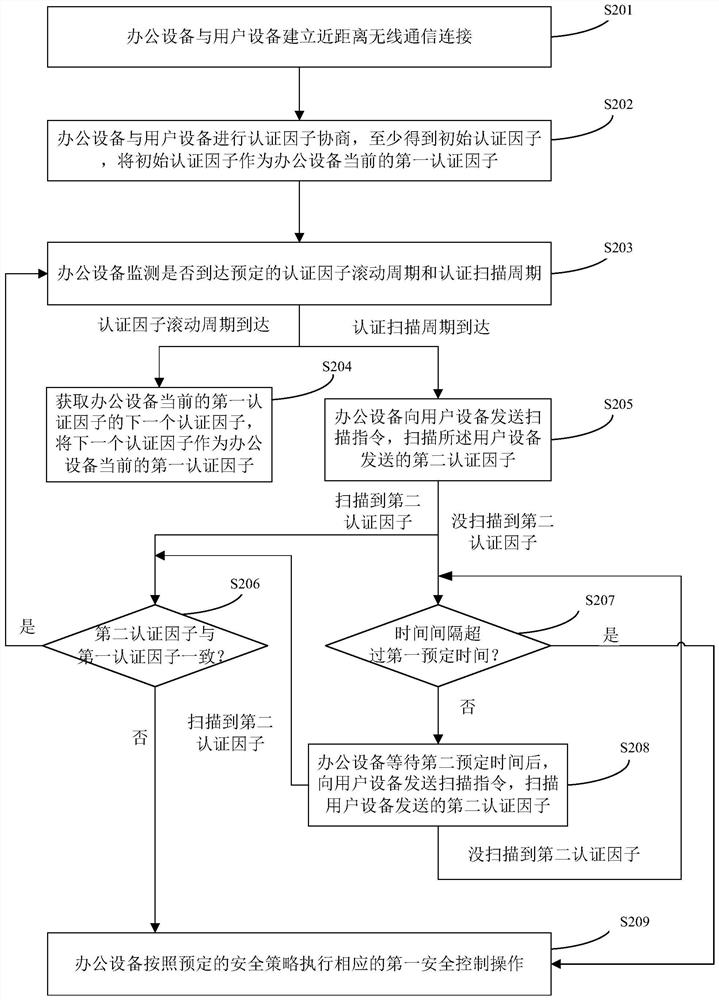
[0073] figure 2 is a flowchart of a security control method provided by an embodiment of the present invention, such as figure 2 As shown, the method mainly includes the following steps:
[0074] Step 201, the office equipment establishes a short-range wireless communication connection with the user equipment.
[0075] In a specific application, wireless communication may be established between the office equipment and the user equipment through Bluetooth, WIFI, etc., which is not specifically limited in this embodiment.
[0076] In a specific application, before the wireless communication connection is established between the office equipment and the user equipment, identity authentication can be performed between the user equipment by swiping cards, scanning codes, and the like. For example, if a card reader m...
Embodiment 3
[0117]This embodiment provides a safety control device, which can be set in the office equipment described in Embodiment 1, and used to implement the safety control method described in Embodiment 2.
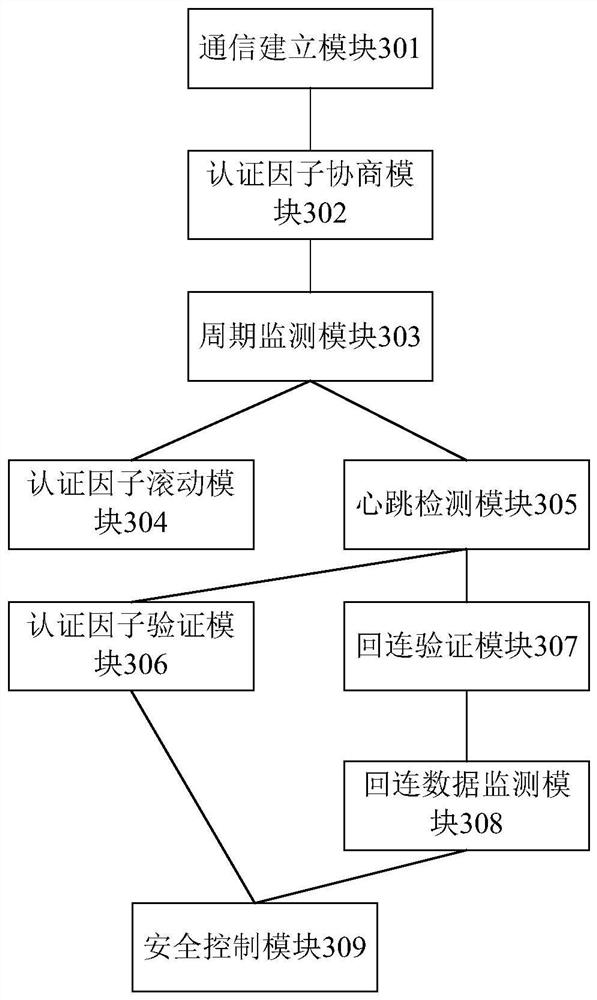
[0118] image 3 A schematic structural diagram of a safety control device provided in this embodiment, such as image 3 As shown, the security control device mainly includes: a communication establishment module 301, an authentication factor negotiation module 302, a cycle monitoring module 303, an authentication factor rolling module 304, a heartbeat detection module 305, an authentication factor verification module 306, a connection verification module 307, a return The data monitoring module 308 and the security control module 309 are connected. The functions of each module of the safety control device are mainly described below, and other relevant matters may refer to the descriptions of Embodiment 1 and Embodiment 2.
[0119] In the embodiment of the present invention, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com