Big data desensitization method in urban planning
A technology of urban planning and big data, applied in the fields of digital data protection, data processing application, electrical digital data processing, etc., can solve the problem of no protection method, etc., and achieve the effect of protecting the privacy of needs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] figure 1 It is a flow chart of the method for desensitizing big data in urban planning according to the first specific embodiment of the present invention.
[0035] The desensitization method of big data in urban planning is applied to the desensitization system. The desensitization system includes a data demander, a data provider and a third-party trust platform. The third-party trust platform includes an external inaccessible encryption mode confirmation chip. The externally inaccessible encryption mode in the third-party trust platform confirms that the hash algorithm in the chip is implanted by the manufacturer when it leaves the factory, and cannot be modified later.
[0036] The method includes:
[0037] Step 1: The data demander uses the random number generator to generate the first random number t.
[0038] Step 2: The data requester generates a data request message and sends it to the third-party trusted platform. The data request message includes: the first ...
Embodiment 2
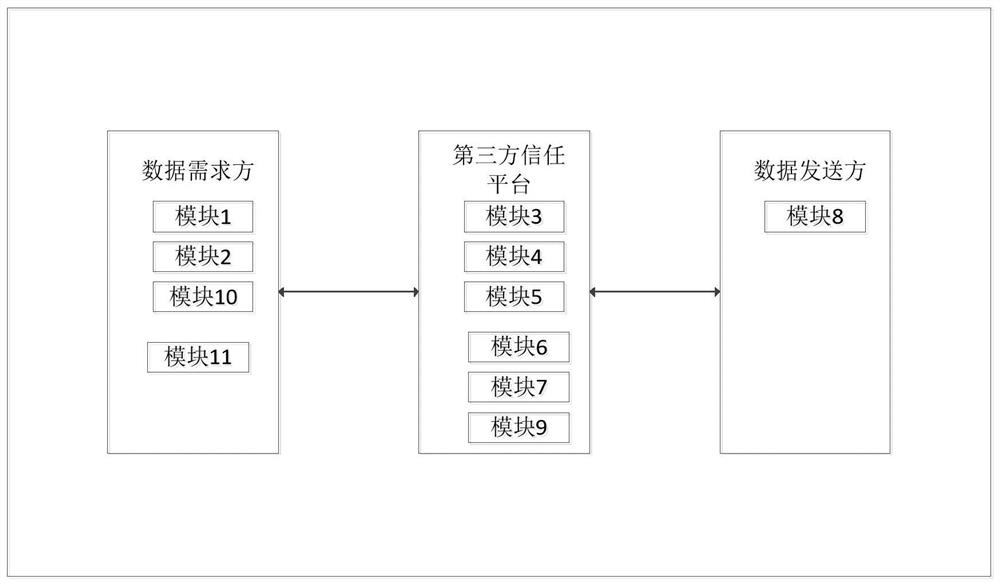
[0057] figure 2 The block diagram of the big data desensitization system in urban planning according to the second specific embodiment of the present invention.
[0058] A desensitization system for big data in urban planning. The desensitization system includes a data demander, a data provider, and a third-party trust platform. The third-party trust platform includes an externally inaccessible encryption mode confirmation chip. The externally inaccessible encryption mode in the third-party trust platform confirms that the hash algorithm in the chip is implanted by the manufacturer when it leaves the factory, and cannot be modified later.
[0059] The system includes:
[0060] Module 1: The data demander uses the random number generator to generate the first random number t.
[0061] Module 2: The data requester generates a data request message and sends it to the third-party trusted platform. The data request message includes: the first random data t, the data provider ID,...
Embodiment 3
[0080] A computer system for desensitizing big data in urban planning, including a processor, a memory, and the memory is used to perform the following steps:
[0081] Step 1: The data demander uses the random number generator to generate the first random number t.
[0082] Step 2: The data requester generates a data request message and sends it to the third-party trusted platform. The data request message includes: the first random data t, the data provider ID, and the desired data.
[0083] Step 3: After the third-party trusted platform obtains the data request message, the first random number t therein is sent to an external inaccessible encryption mode confirmation chip, which includes a hash operation logic module k=hash(t), The input is the first random number t, and the output value k is between [0, n-1]; n is the number of homomorphic encryption modes that the third-party trusted platform can provide, and is a natural number greater than 1.
[0084] Preferably, the en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com