Voice spoofing attack detection method based on voice signal spectrum characteristics and deep learning
A technology of spectrum characteristics and voice signals, applied in the field of voice authentication technology and security, can solve the problems of low detection accuracy, poor user experience, difficult to apply, etc., and achieve the effect of solving network degradation, low cost, and improving sensitivity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043]The present invention will be further described below in conjunction with the drawings.
[0044]The complete implementation of the method according to the present invention and its implementation are as follows:
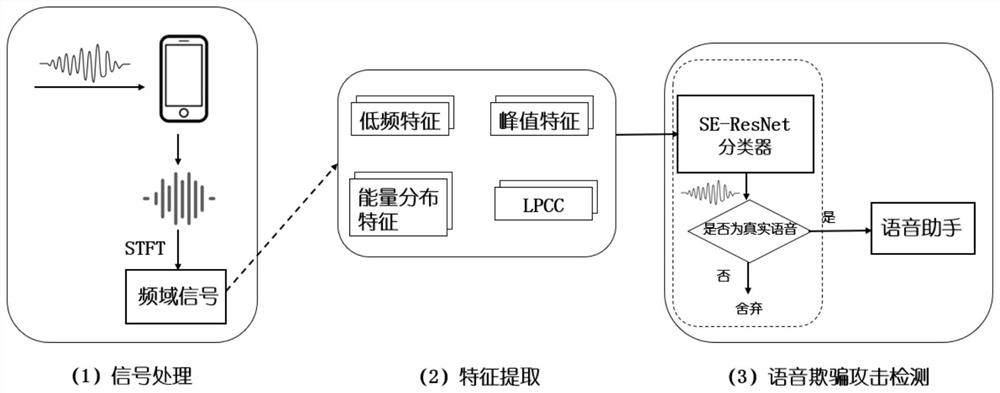
[0045]1) Signal processing:
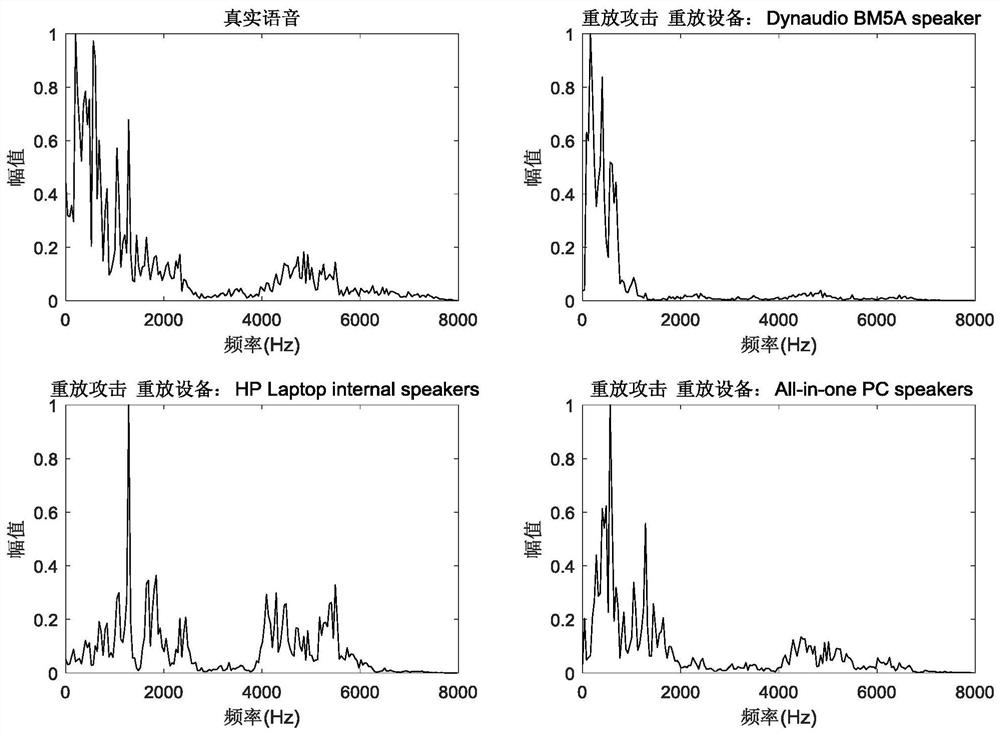
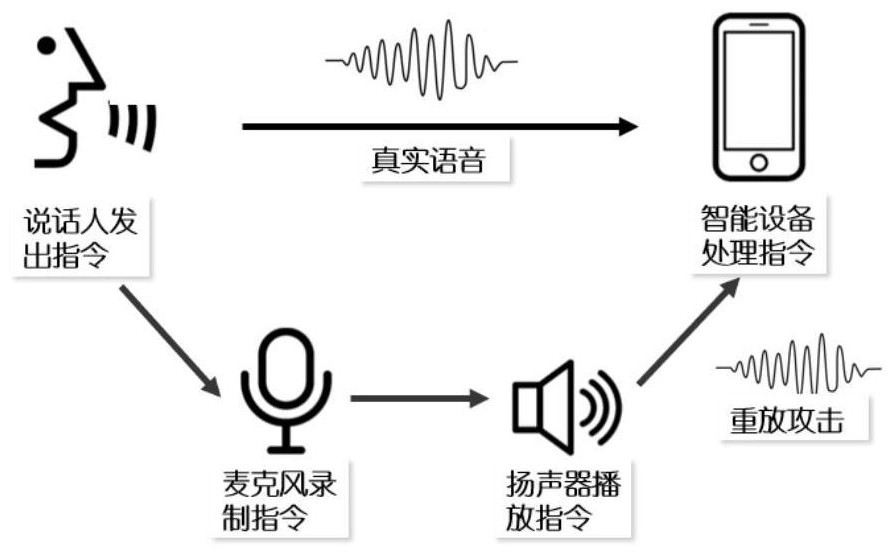
[0046]Such asfigure 1 As shown, the original voice signal Voicein Follow the following two steps to obtain the cumulative power spectrum Spow :
[0047]The first step adopts short-time Fourier transform. The process of short-time Fourier transform is as follows: First, use a periodic Hamming window with a length of 1024 (representing 1024 data points) and an overlap length of 768 to compare the original voice signal Voicein Perform windowing processing to convert the original voice signal Voicein Divide into multiple data frames with a length of 1024, and then perform fast Fourier transform on each data frame, and the number of Fourier transform points nfft is 4096;
[0048]The second step is to accumulate the results of the fast Fourier transform of e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com