Simple and rapid communication encryption and decryption algorithm
An encryption and decryption algorithm and fast technology, applied in wireless communication, encryption device with shift register/memory, secure communication device, etc., can solve problems such as long decryption time, long ciphertext, complicated operation process, etc., and achieve machine work Less time consumption, improved security performance, fast and easy encryption and encryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
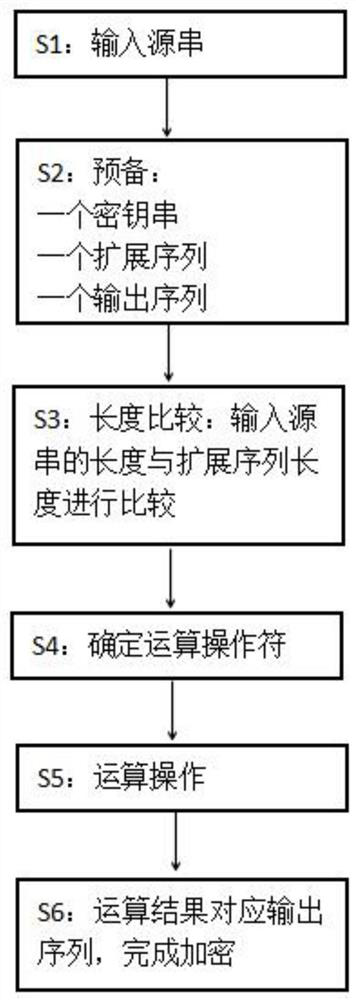
[0030] A simple and fast communication encryption and decryption algorithm includes an encryption step and a corresponding decryption step, and the encryption algorithm includes the following steps:
[0031] S1: Input: Process the data to be encrypted in bytes as the input source string; for example, a binary or ASCII data string;
[0032] S2: Preparation: Prepare a key string, an extension sequence and an output sequence. The extension sequence is composed of countless extension codes. Each extension code is an integer and can be repeated. The extension code represents the number of extension bits. The value of the extension code in the extension sequence marks the corresponding extension bit in the output sequence; the data in the key string can be a binary code or ASCII data string, and the input source string and the key string can be the same binary code or ASCII data string;
[0033] S3: length comparison: the length of the input source string is compared with the exten...
Embodiment 2
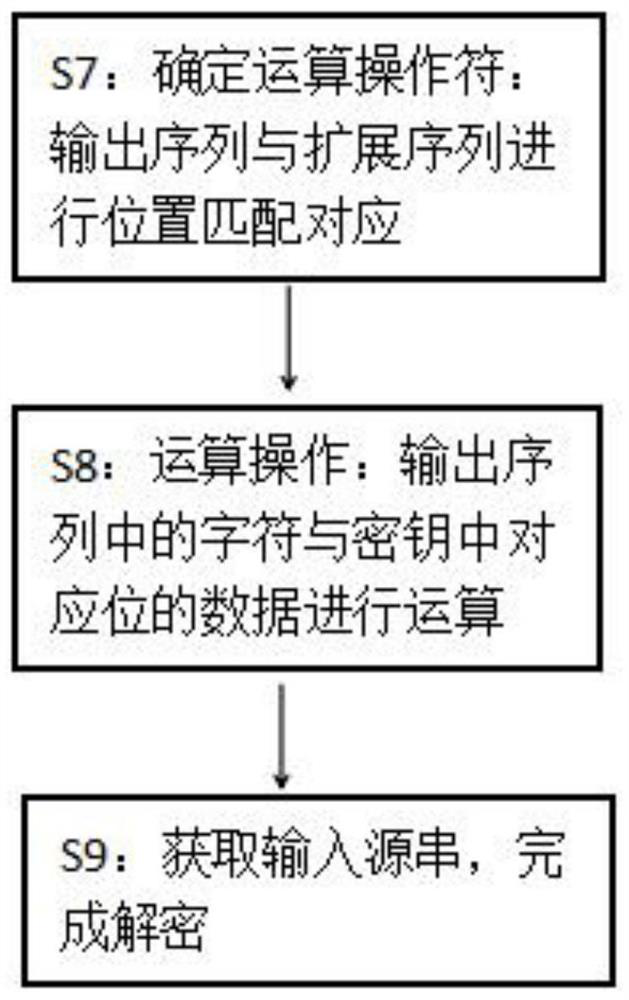
[0045] On the basis of Embodiment 1, the extension of the extended sequence length or the key length is in the form of a ring string, and the ring position can start from the first bit of the extended sequence length or the key, or from other positions after the first bit. The encryption step The looping position in is consistent with the looping position in the decryption step.
[0046] As the value of the extension code in the extension sequence in the above S2 step, the length is the length of 15 figures, byteextendceode[]={1,3,2,6,3,1,4,6,8,1,2,3, 4,5,1}, if it needs to be extended to 20 digits to match the length of the input source string, the subsequent digits can be followed by the last digit 1 followed by the first digit 1 or the second digit 2 Loop, or start looping from other digit positions behind to form a ring string. Similarly, in the process of step S5, the length of the key data string is compared with the length of the input data string. When the length of t...
Embodiment 3
[0049] On the basis of Embodiment 1, the input source string data in the step S1 is preprocessed by custom byte. For example, a byte of data can be shifted left or right by a few bits. For example, define α to move 4 bits to the left, define β to move 4 bits to the right, and define γ to move 3 bits to the left. If the input source string is 0x43, 0xA4, 0xA4, perform α operation on 0x43 to get 0x34; Perform β operation to obtain 0x4A, and perform γ operation on 0xA4 to obtain 0x25, that is, the input source string data 0x43, 0xA4, 0xA4 becomes 0x34, 0x4A, 0x25 after preprocessing, which further strengthens the security performance of the file to be encrypted.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com