Browser sample set acquisition method based on deep learning and genetic algorithm
A deep learning and genetic algorithm technology, applied in the field of browser sample set acquisition, can solve problems such as inability to bypass protective measures, vulnerability mining sample set generation and optimization without general processes and frameworks, waste of computing resources, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The present invention will be further described below in combination with specific embodiments and accompanying drawings.
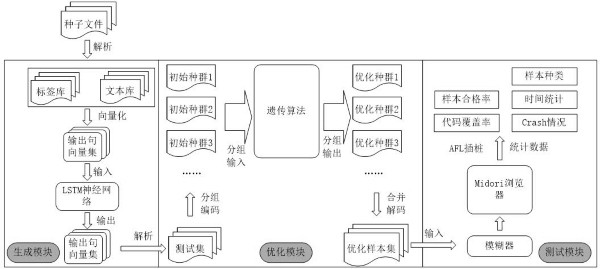
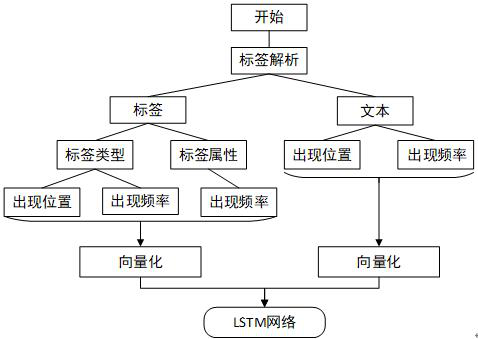
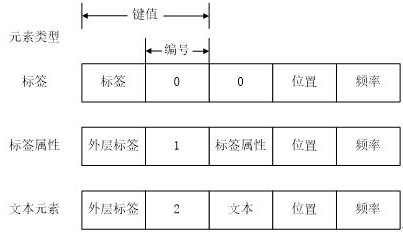
[0058] In order to make the browser vulnerability mining sample acquisition method described in the present invention easier to understand and close to the real application, the following describes the overall process from the sample generation and optimization model and the actual browser vulnerability mining, including the core neural network of the present invention. Network structure and optimization genetic operator:
[0059] (1) Collect relevant samples and classify them, and filter out memory corruption exploit samples such as stack overflow, heap overflow, integer overflow, and reuse after free. When constructing the sample library, only select samples of memory corruption exploits. In order to improve the learning efficiency of the deep neural network and clarify the learning direction, artificial variation is used to expand the sample se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com