Generalized signcryption method based on certificate
A generalized, certificated technology, applied in the field of information security, can solve problems that few studies have covered
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be described in detail below with reference to the accompanying drawings.
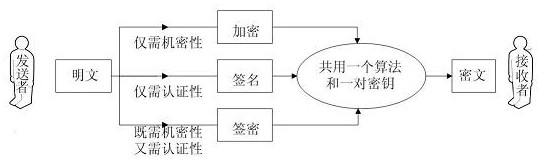
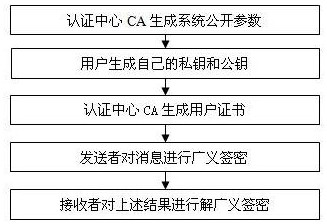
[0037] like figure 1 , 2 As shown, the present invention provides a certificate-based generalized signcryption method. In the application scenario of the generalized signcryption method, when the sender only needs confidentiality, he uses the encryption mode of the algorithm; when only authentication is required In the case of security, he uses the signature mode of the algorithm; in the case where both confidentiality and authentication are required, he uses the signcryption mode of the algorithm. The sender only needs to use one algorithm and save a pair of keys, which reduces the management overhead of keys and the complexity of system implementation. The concrete process of the present invention is as follows:
[0038] Step 1. System initialization.
[0039] The security parameter k is a positive integer; the certification center selects two prime numbers p and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com