Threat response method and device based on threat intelligence and ATT&CK
An ATT&CK and intelligence technology, applied in computer security devices, machine learning, instruments, etc., can solve the problems of high load overhead, disorder and disorder of the policy system, lack of effective evidence in the traceability process, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
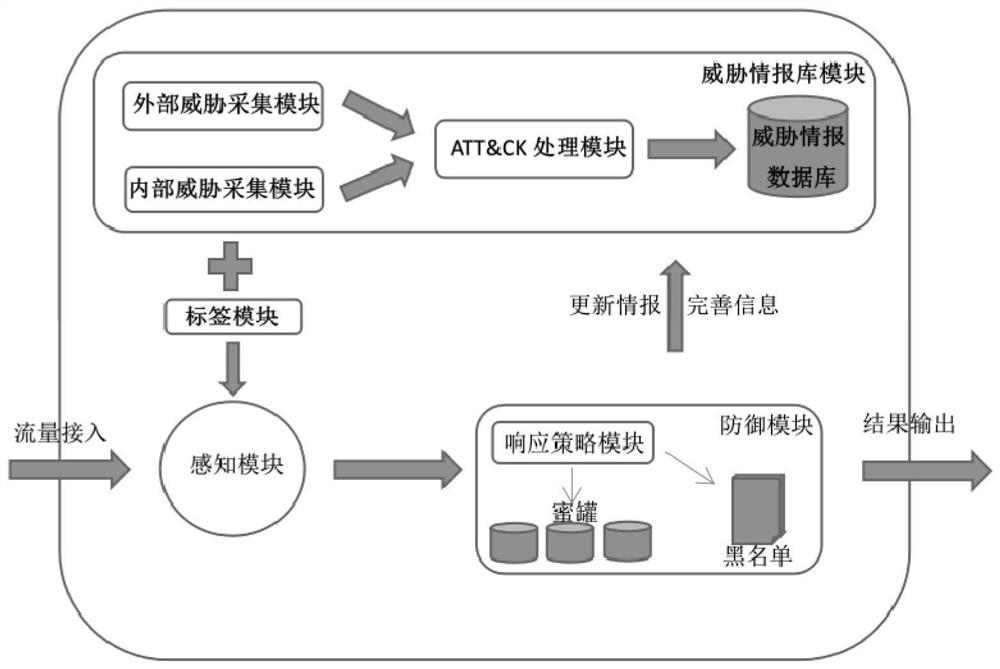
[0060] figure 1 An overall structural diagram of a threat response method based on threat intelligence and ATT&CK provided by an embodiment of the present invention.
[0061] S1 establishes a threat intelligence library:
[0062] S11 External threat collection steps: Use crawlers and open source threat intelligence sharing platform APIs to automatically collect external threat intelligence from public resources as the first collection result;
[0063] Specifically, to establish an open source threat intelligence collection and query framework, automatically collect threat intelligence from various public resources, use crawlers and open source threat intelligence sharing platform APIs, simplify the external collection process, and quickly collect and organize. Among them, the crawler part is mainly aimed at targets such as Twitter, Tor, dark web forums, security portal 360, freebuf, fireeye, MCAfee, etc., and uses libraries such as BeautifulSoup, Requests, and Scrapy in Pytho...
Embodiment 2
[0110] Further, another embodiment of the present invention provides a threat response device based on threat intelligence and ATT&CK as an implementation of the methods shown in the above embodiments. This device embodiment corresponds to the foregoing method embodiment. For the convenience of reading, this device embodiment does not repeat the details in the foregoing method embodiment one by one, but it should be clear that the device in this embodiment can correspond to the foregoing method implementation. Everything in the example. In the device of this embodiment, there are following modules:
[0111] One: Threat intelligence database module, corresponding to S1 in Embodiment 1, establishes a threat intelligence database.
[0112] The external threat collection sub-module uses crawlers and open source threat intelligence sharing platform APIs to automatically collect external threat intelligence from public resources as the first collection result. The external threat ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com