Segmented clustering-based road network trajectory semantic privacy protection method
A privacy protection and road network technology, which is applied in the field of network security and privacy protection, can solve the problems of not considering location semantics, low anonymity success rate, and poor quality of anonymous data, so as to improve the effect of semantic privacy protection, improve the quality of anonymous data, The effect of reducing data loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0073] The present invention will be further described in detail below in conjunction with the embodiments and the accompanying drawings, but the embodiments of the present invention are not limited thereto.
[0074] Such as figure 1 As shown, the segmented clustering-based road network trajectory semantic privacy protection method provided in this embodiment combines segmentation, clustering and heuristic algorithms to generate anonymous segment sets, including the following steps:
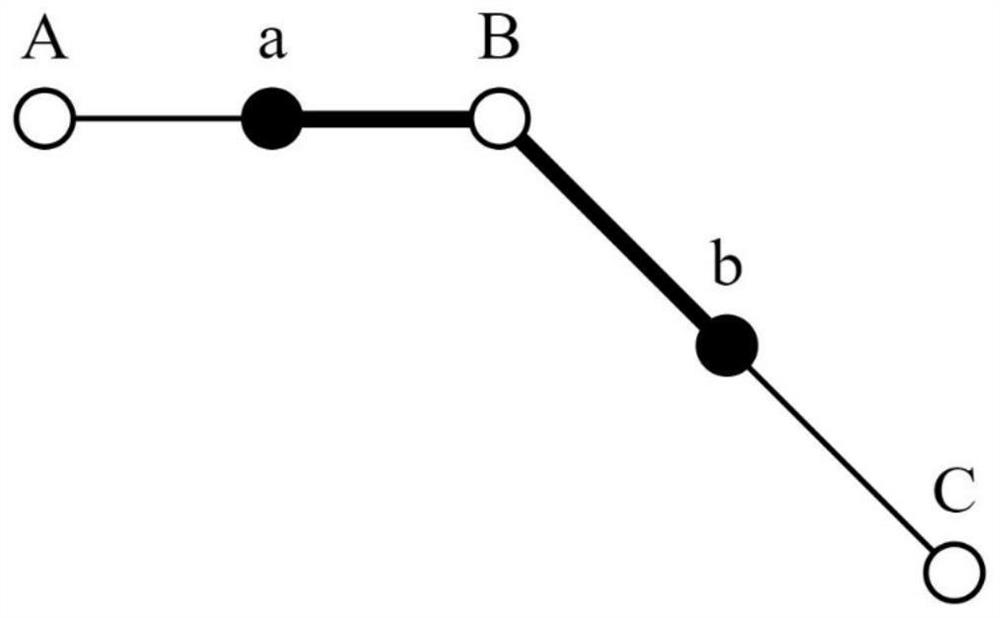
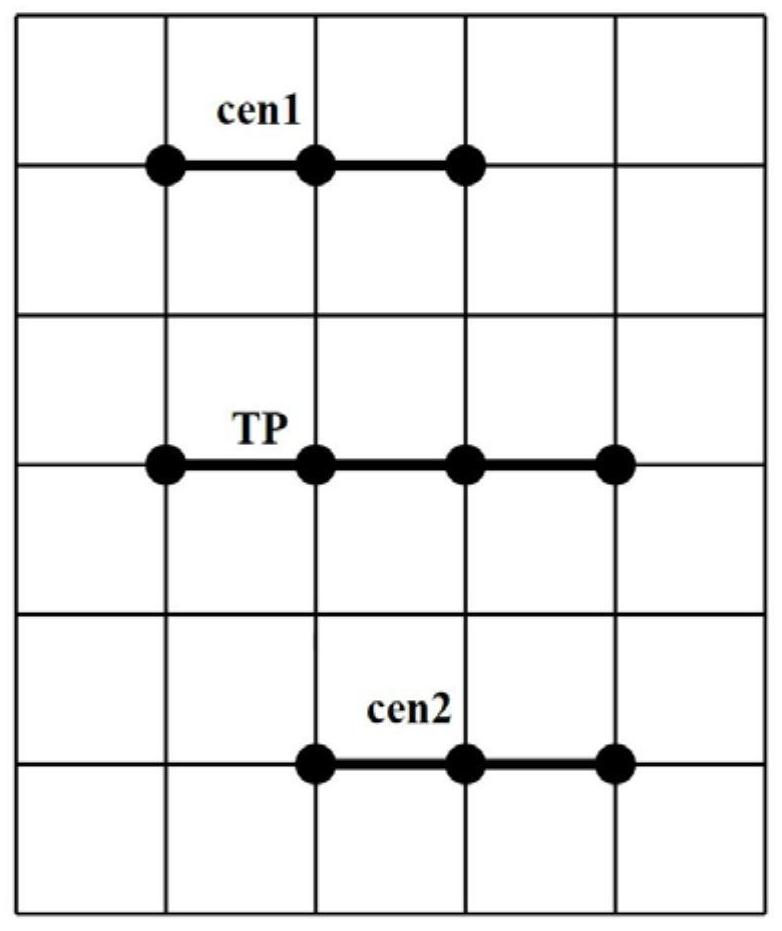
[0075] 1) Preprocess the initial trajectory data set, and resample the trajectory; wherein, a trajectory in the initial trajectory data set is expressed as T={uid,(p 1 ,p 2 ,...,p n )}, where uid is the user ID of the track, p i =(x i ,y i ,t i ) is the location point that constitutes the trajectory, indicating that the user is at t i The latitude and longitude of time is x i and y i , i=1,2,...,n; the preprocessing process performs the following resampling algorithm on the trajectory T:...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com