System and method for security protection of Internet of things equipment
An IoT device and security protection technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve the problems of security loopholes, low efficiency ratio, and low security of communication encryption and decryption, and achieve high security and efficiency. High ratio, the effect of solving security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
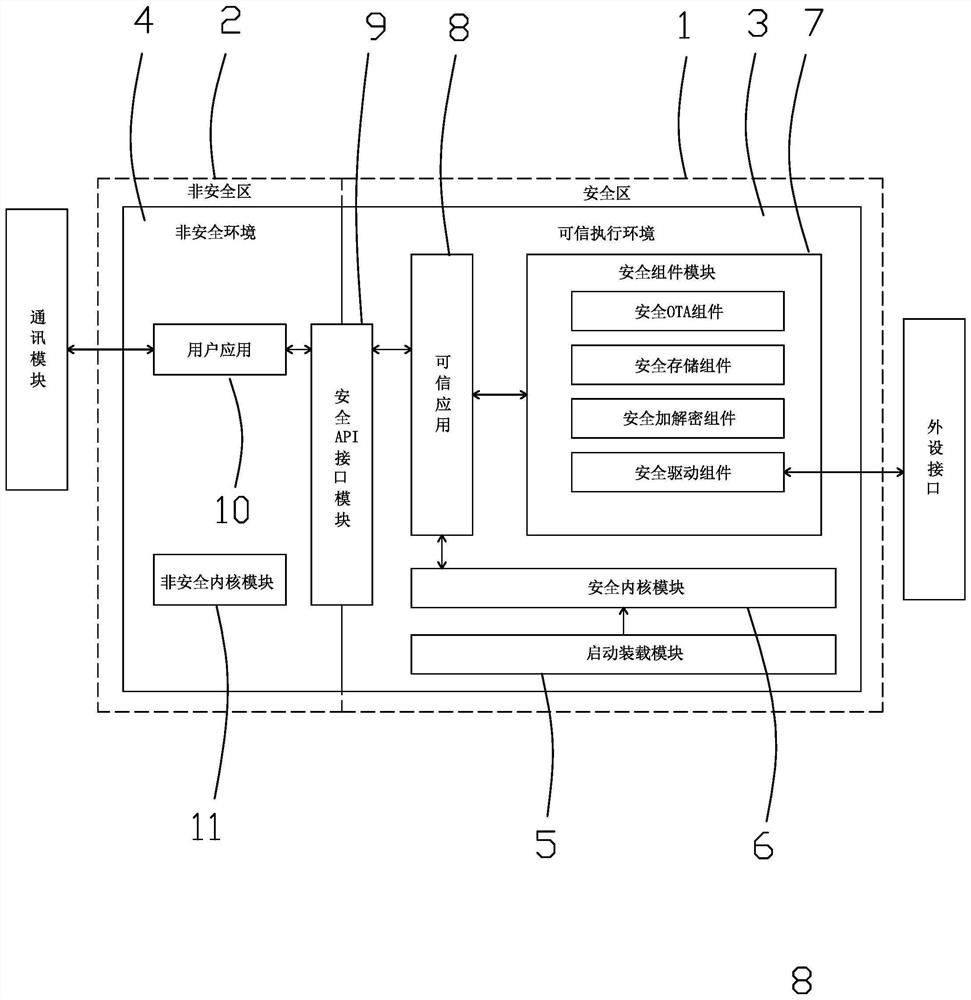
[0094] In this embodiment, a security protection system for Internet of Things equipment includes communication-connected equipment and servers, and the equipment includes an MCU controller, such as figure 1 As shown, the MCU controller includes safe area 1 and non-safe area 2,
[0095] The safe area can access all resources, and the non-safe area can only access the resources of the non-safe area and is forbidden to access the resources of the safe area. When the non-safe area illegally accesses the resources of the safe area, the MCU controller intercepts and generates an exception from the hardware. The safe area and the non-safe area can be switched, and are strictly monitored by the MCU controller.
[0096] In addition, set the read-write protection function for the MCU controller, and the external debugging tool cannot debug, and cannot read and modify the contents of the flash, sram, and backup registers. When the read protection is released, the hardware will automatic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com