Intelligent security policy configuration method based on target perception
A security policy and intelligent configuration technology, applied in the field of information security, can solve the problems of heavy manual operation of policy configuration, the impact of security policy configuration correctness on the availability of network connectivity services, security policy configuration and defense goals need to be further improved, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
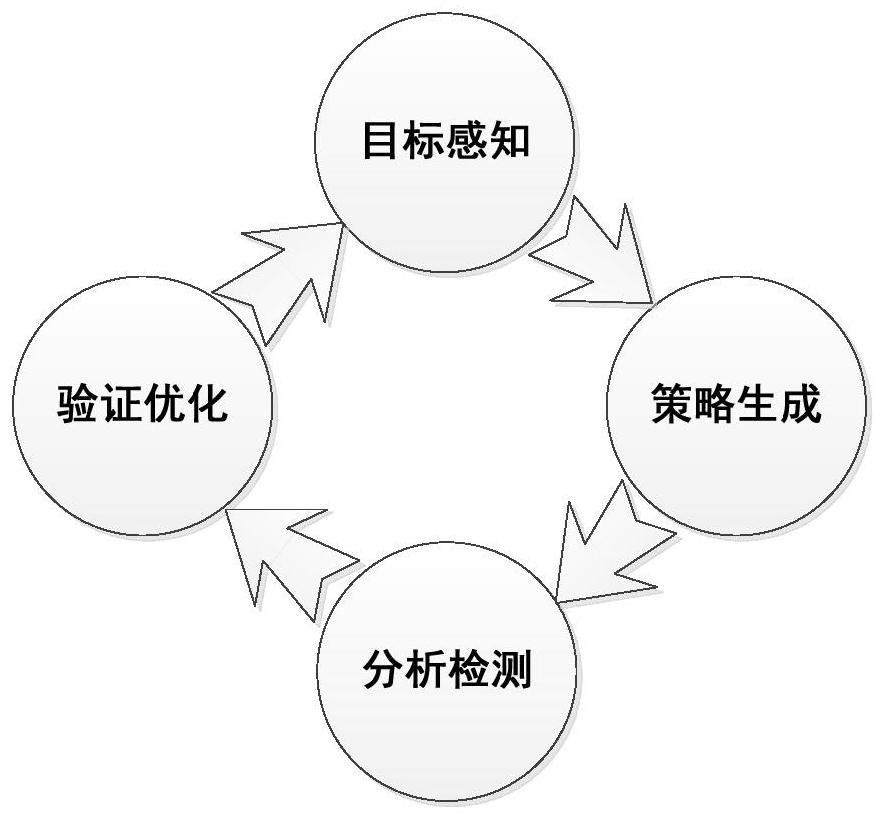
[0030] refer to Figure 1 to Figure 5 As shown, the present invention discloses a security policy intelligent configuration method based on target perception, and the security policy intelligent configuration method includes at least four stages: target perception, policy generation, analysis and detection, and acceptance optimization. The system model is as follows figure 1As shown, the four stages constitute a dynamic and closed-loop working model, reflecting the characteristics of intelligent response and continuous optimization.
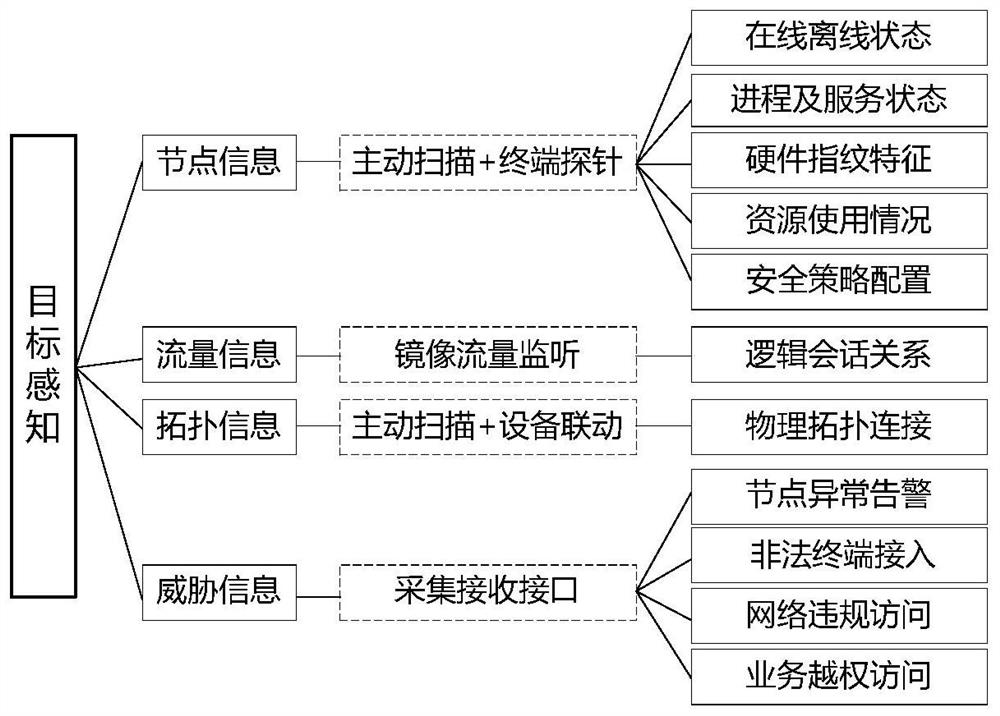
[0031] Preferably, the target sensing step acquires node information, flow information, topology information and threat information of the target network through active detection and / or passive monitoring, and analyzes and senses the state of the target network. Perceive the accurate status of the target network through comprehensive analysis, and provide information support for the generation of security protection strategies.
[0032] Further,...
Embodiment 2
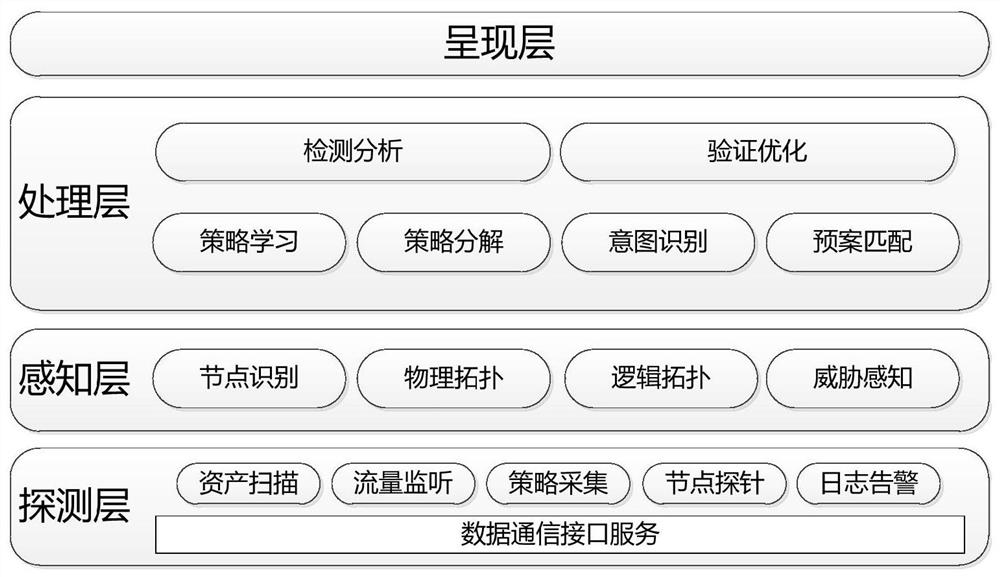
[0050] On the basis of embodiment 1, refer to figure 2 As shown, the present invention also discloses an implementation framework for the intelligent configuration method of the security policy. Its core is information detection, target perception, and intelligent analysis and processing to achieve fast and efficient security policy configuration and deployment, reduce the complicated operations of security management and maintenance personnel, and assist them in making security protection decisions.
[0051] The implementation architecture includes a detection layer, a perception layer, a processing layer and a presentation layer.
[0052] The detection layer: conduct active and passive network and target detection through data communication interface services, including discovering network nodes through active scanning and detection, monitoring network intercommunication session relationships through traffic collection such as mirroring, and collecting strategies for securi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com