Truncated TCP stream splicing method
A destination and source address technology, applied in electrical components, transmission systems, etc., can solve problems such as truncation, and achieve the effect of enhancing accuracy and avoiding port scanning attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
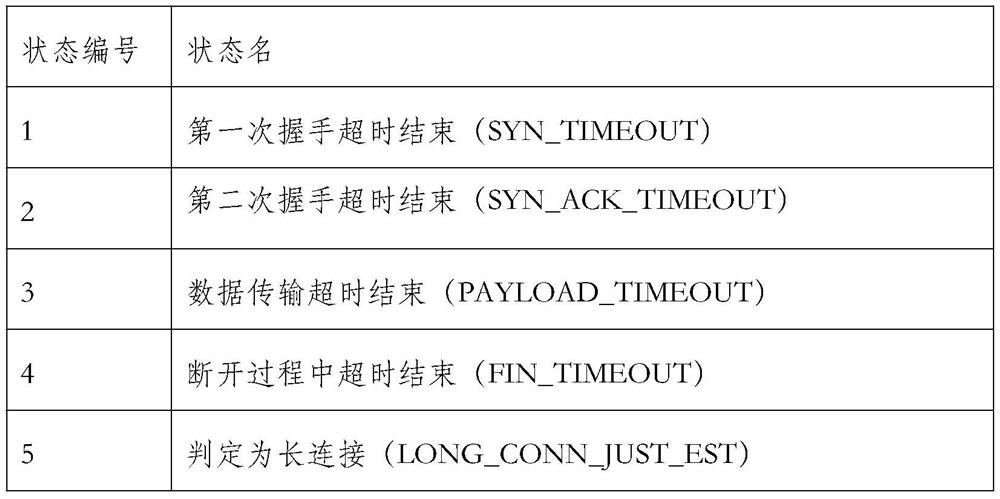
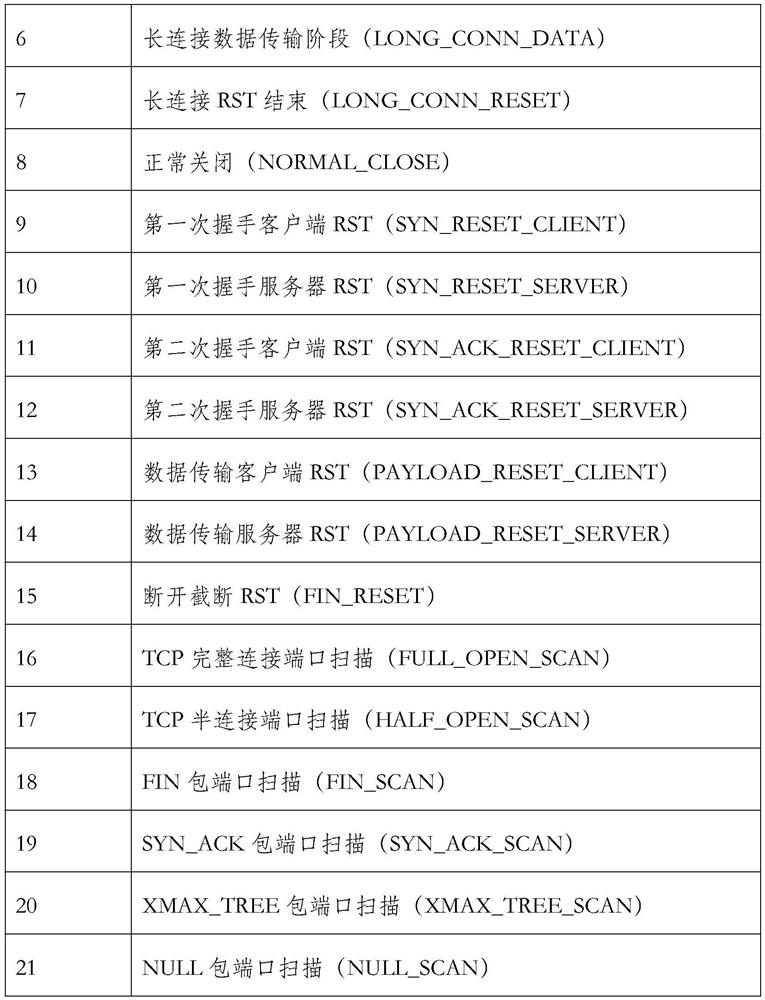
[0076] Embodiment 2 of the present invention: based on the TCP flow splicing method of analyzing the end state of the TCP flow and the direction of the TCP flow, the truncated TCP flow is spliced, including the following steps:
[0077] 1. The bypass data collection and analysis system collects mirrored traffic, receives the SYN packet sent by the first client, and adds a record to the TCP record queue.
[0078] 2. Then receive the SYN / ACK packet sent by the server. Since the delay time of the SYN / ACK exceeds the RTO set by the bypass data acquisition and analysis system, the system records the end state of the TCP stream as SYN_TIMEOUT. At this time, the system adds a record for the SYN / ACK packet in the record queue, and the direction of the new TCP flow record is reversed.
[0079] 3. The newly created TCP flow completes the three-way handshake and four-way wave, and the bypass data acquisition and analysis system records the end state of the TCP flow as NOMAL_CLOSE.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com