Binary code tracing method for multi-granularity information fusion under software gene perspective
A binary code, multi-granularity technology, applied in the field of network security, can solve problems such as difficulty in obtaining source code, loss of semantic information of binary code, etc., to achieve the effect of improving the accuracy of traceability, the accuracy of traceability, and the effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further explained below in conjunction with accompanying drawing and specific embodiment:
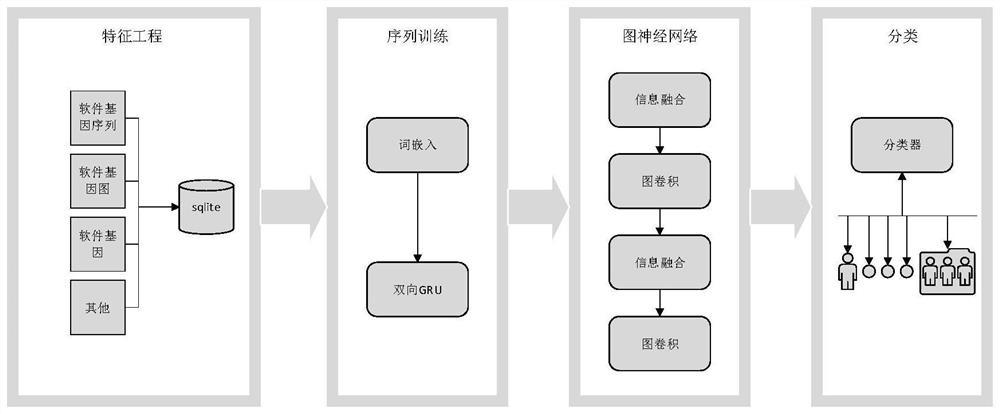
[0039] Such as figure 1 As shown, a binary code traceability method for multi-granularity information fusion from the perspective of software genes, including:
[0040] Step 1: Extract the software gene sequence, software gene, software gene map of the target program and common information directly extractable from IDA to the sqlite database;
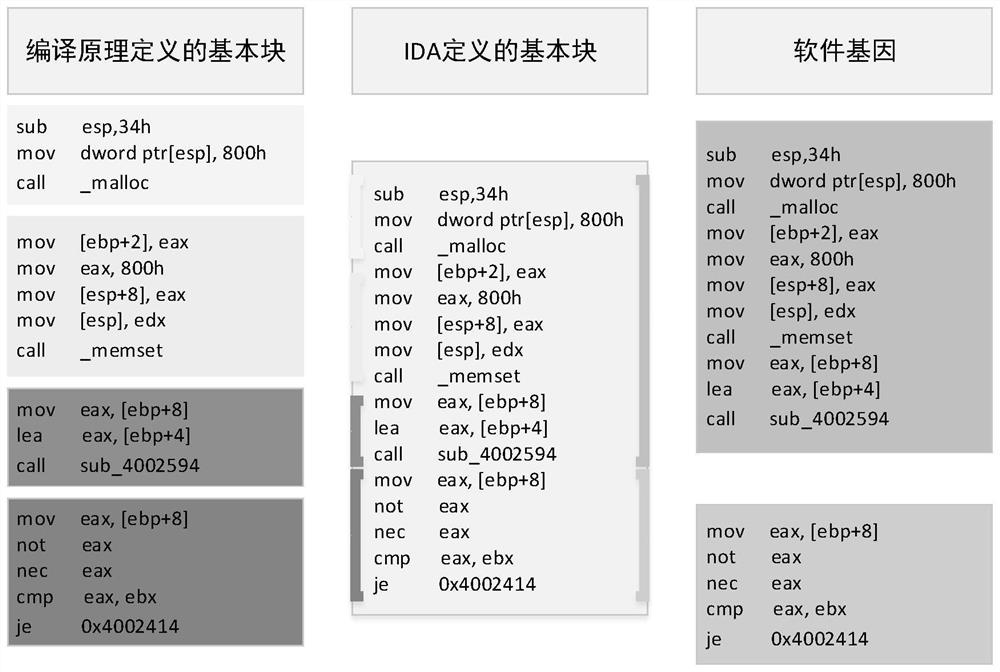
[0041] Further, the commonly used information directly extractable from IDA includes: normal instruction sequences, basic blocks, and information of control flow graphs and program call graphs extracted by IDA.
[0042] Specifically, the software gene sequence is defined as follows:
[0043] For a binary executable F, P is the set of all instructions in F, s i is a series of factors that affect the control flow of the program, Exec(s i ) is in factor s i A set of instruction sequences that have been execu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com