Network attack recovery method of cascaded condition-based energy generative adversarial network
An energy generation and network attack technology, applied in the field of network information security, can solve problems such as difficult control, data recovery accuracy depends on physical system modeling accuracy, recovery accuracy and poor stability, etc., to achieve improved accuracy, high recovery accuracy and stability The effect of high reliability and high data recovery accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
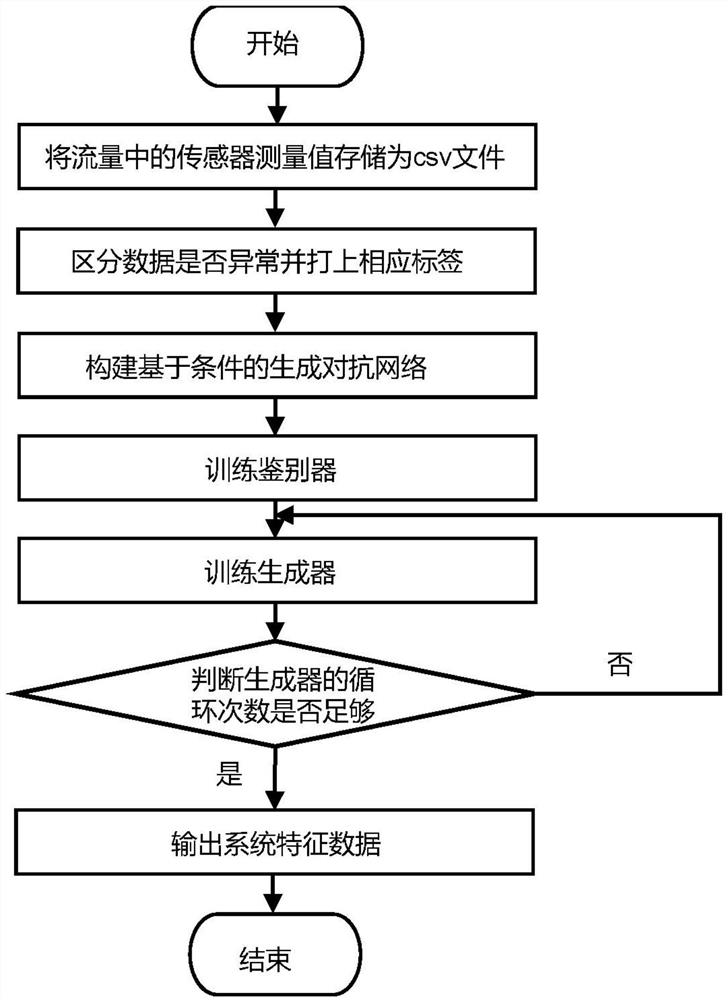
[0058] Such as figure 1 As shown, Embodiment 1 is a cascading condition-based energy generation confrontation network method, which consists of three steps: training a condition-based generation confrontation network model that can simulate the normal operation of the system, and establishing a condition-based energy generation confrontation network model. Generate an adversarial network model and implement an adaptive decision-making strategy, and evaluate the recovery performance of different models using the absolute error between the recovered measurement value and the real measurement value and the spatiotemporal loss caused by the model. The specific content is described as follows:
[0059] In step 1, the sensor measurement value expressed in the traffic data is used as input, the condition-based generative confrontation network is trained, and the trained model is used to generate feature data.
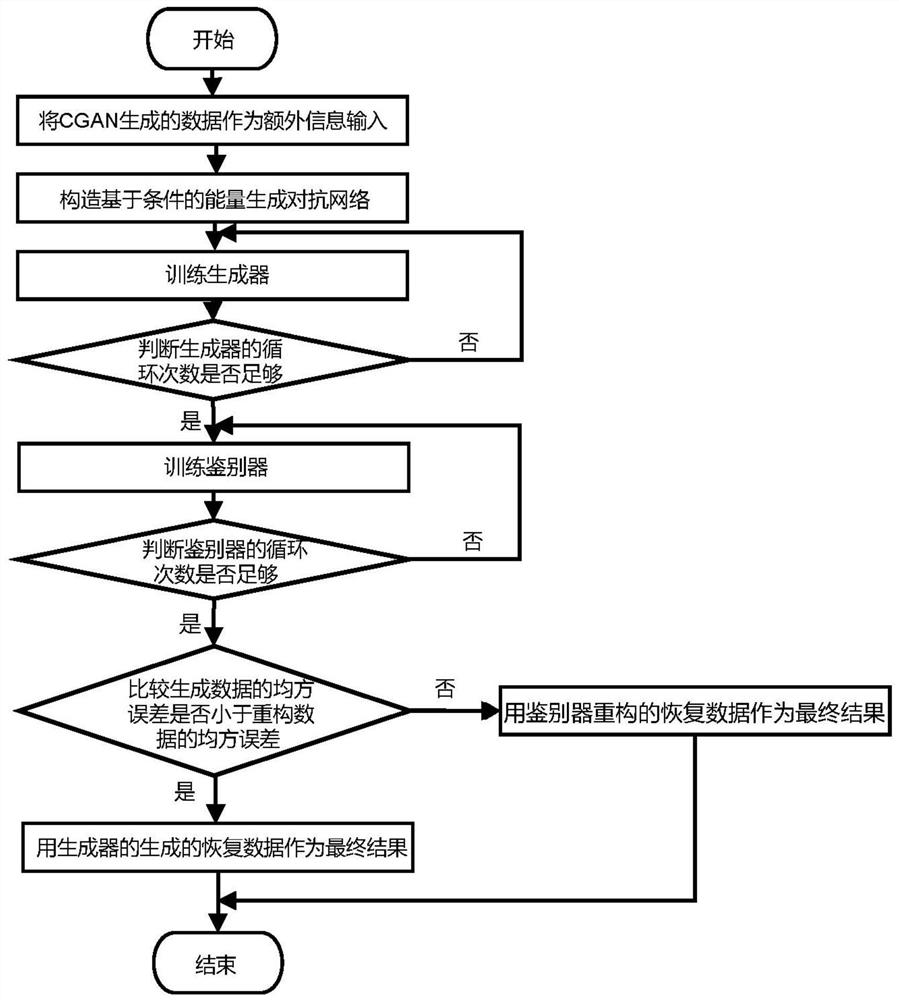
[0060] In step 2, the feature data generated by the condition-based gene...
Embodiment 2
[0093] The second embodiment is to use the recovery data obtained by the traditional generative confrontation network and the cascaded energy-based generative confrontation network with different numbers of training rounds as a reference, and then use the industrial control network traffic for experimental verification, and compare the results obtained by the method proposed in this paper. Recover the data, and compare the training time, storage space usage, and accuracy of the recovered data for different models.
[0094] Figure 5 and Figure 6 Five models are shown with the recovery accuracy over time for different register measurements. Analyzing the results in the table, it can be found that the model proposed in this paper is significantly better than the generative confrontation network and the cascaded energy-based generative confrontation network with different numbers of training rounds in terms of recovery accuracy and stability. The reason for this result is that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com