Industrial host terminal security protection system
A terminal security and protection system technology, applied in the field of network security, can solve the problems that terminal security cannot be guaranteed, anti-virus software cannot detect and defend against APT, etc., and achieve the effect of improving terminal security management capabilities and resource overhead protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
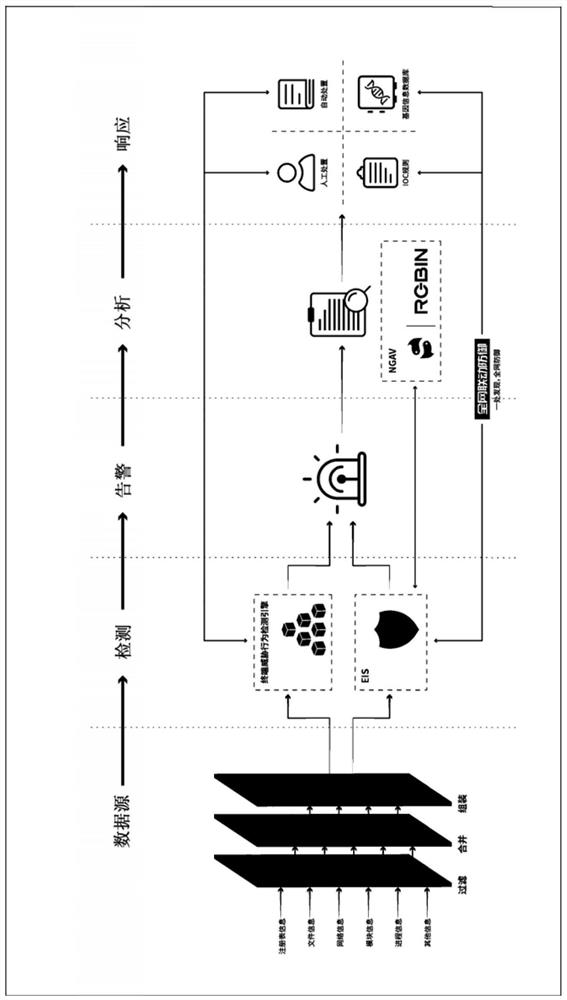
[0027] Such as figure 1 As shown, this embodiment proposes an industrial host terminal security protection system, which is a set of three-dimensional terminal security protection solutions, suitable for terminal systems such as servers, terminal PCs, and virtualization hosts. The system uses C / S and The B / S combination mode provides customers with terminal threat detection, response, traceability and other services.
[0028] The system includes a client and a server. The client and the server adopt a C / S architecture. By installing a lightweight Agent program in the terminal operating system, the full amount of kernel-level fine-grained behavior data is obtained in real time and reported. The above server management adopts B / S architecture to realize threat analysis and system management, adopts distributed deployment mode and big data storage to meet high expansion, high availability and high concurrency, and provides data sources for threat analysis and traceability.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com