Online and offline signcryption method from CLC environment to PKI environment
An environmental and offline technology, applied in the field of secure communication, can solve problems such as the lack of anonymity in the solution, the lack of discussion on the sender's non-certificate environment, the receiver's environment, and the reduction of program efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described in detail below with reference to the accompanying drawings.
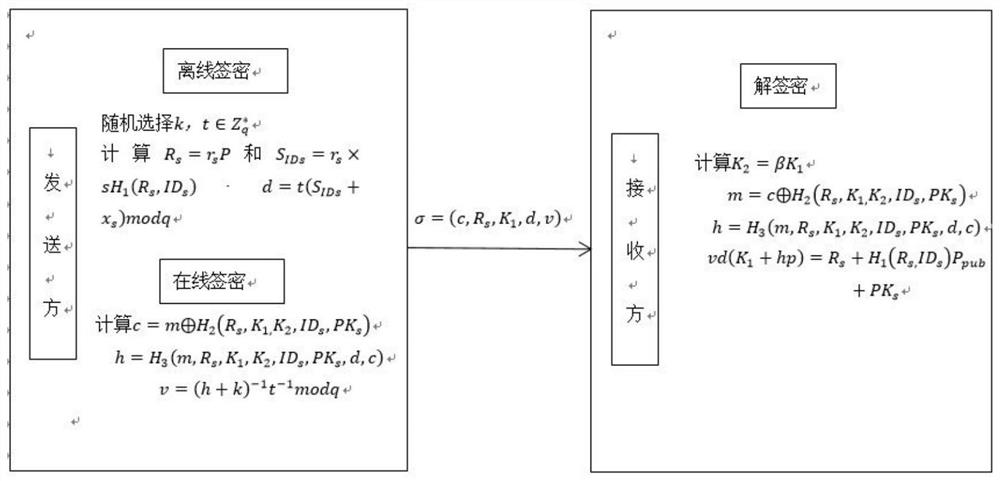
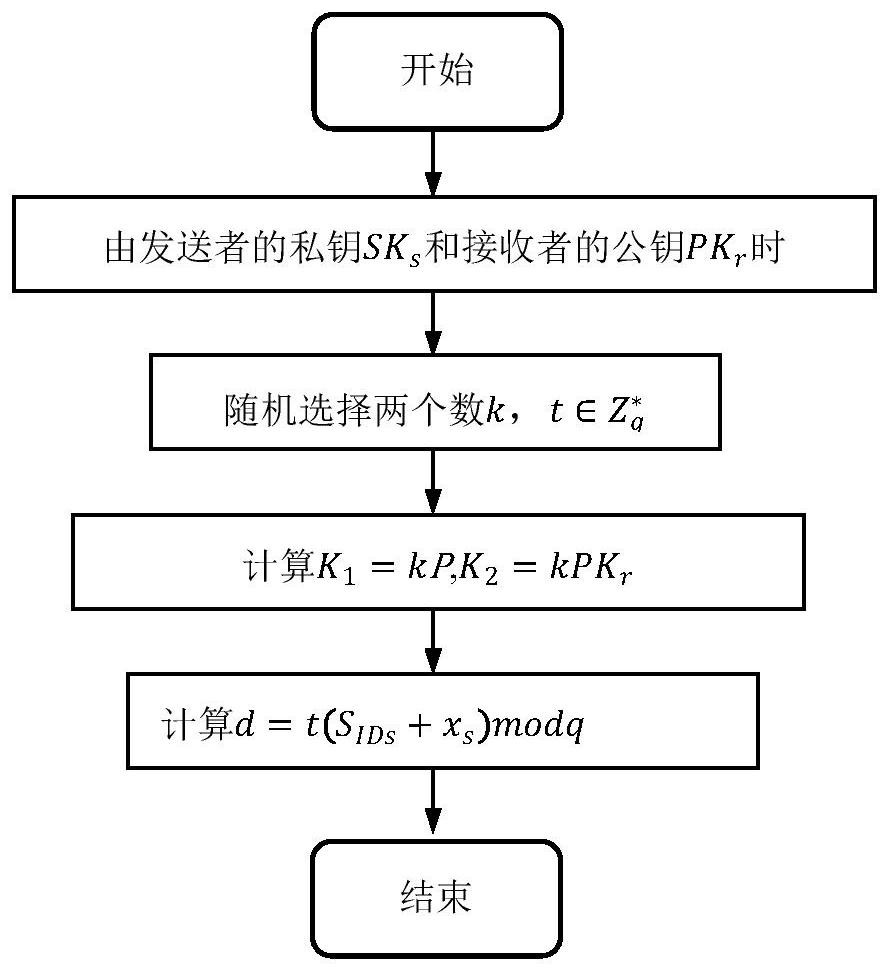
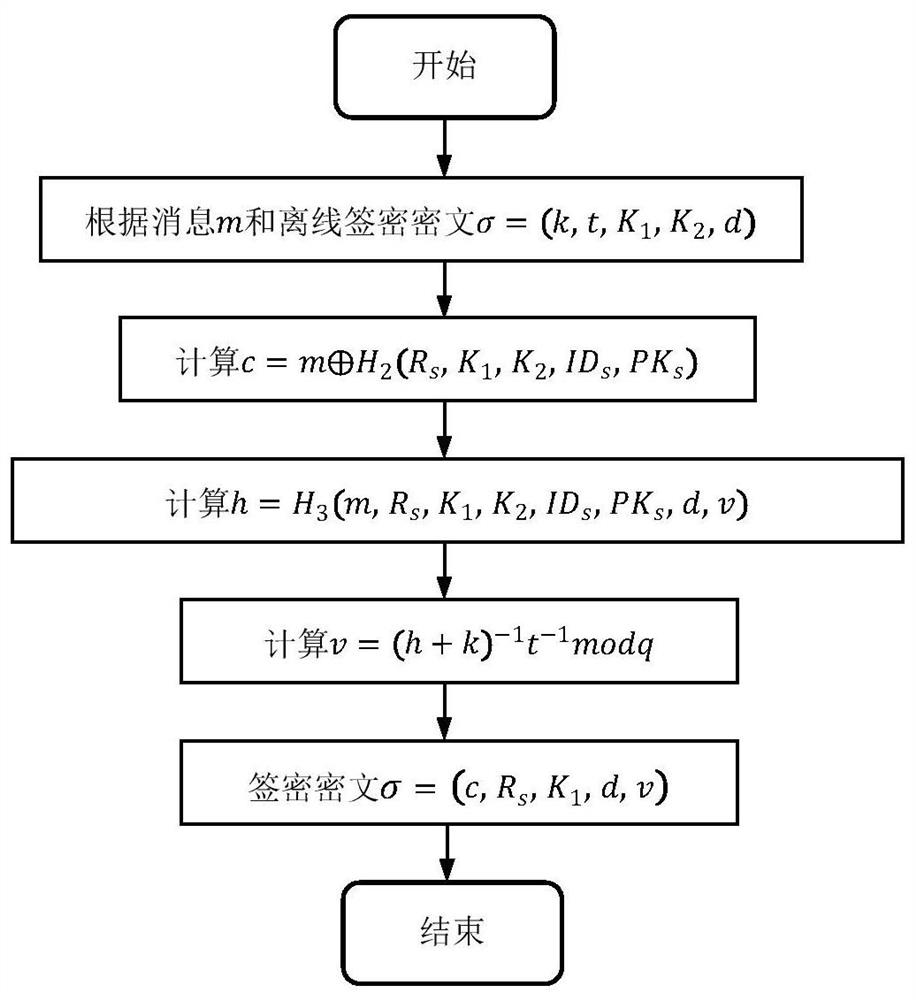
[0030] The present invention proposes an online offline signatory method from a CLC environment to a PKI environment, such as figure 1 As shown, specifically includes the following steps:
[0031] Step 1: System parameters initialize.
[0032] The system parameters comprise a CLC environment-based online offline sign secret module, a system parameters required to be set based on the pyi environment, and the system parameters required for a trusted third party module; specifically: given a security parameter K, set G 1 The cyclic addition group generated by the P, the order Q is the number of ps, and P is G. 1 Generator element. Define three secure hash functions Key Generation Center KGC randomly selects a master key Calculate P pub = SP. KGC public system parameter params = {g 1 , K, P, P pub , Q, H 1 H 2 H 3 }
[0033] And confidential private key s. The para...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com