Container security isolation reinforcement method and device, electronic equipment and storage medium
A technology for security isolation and hardening devices, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as incomplete container isolation, and achieve the effect of avoiding malicious access and realizing network isolation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
[0050] Platform: Substation Monitoring System Basic Platform, cover server hardware, operating system, public service components, real-time database, historical database, message bus, process management, permission management, etc.
[0051] App: Substation specific business function modules, such as grid real-time data drive, network security monitoring, data services, model services, graphics services, alarm services, etc.
[0052] Data Communication Gateway: Communication, security, measurement, auxiliary control, fire protection and first, secondary equipment online monitoring, etc. The remote service and other functions provide smart communication devices for transport services for data, models, and graphics.
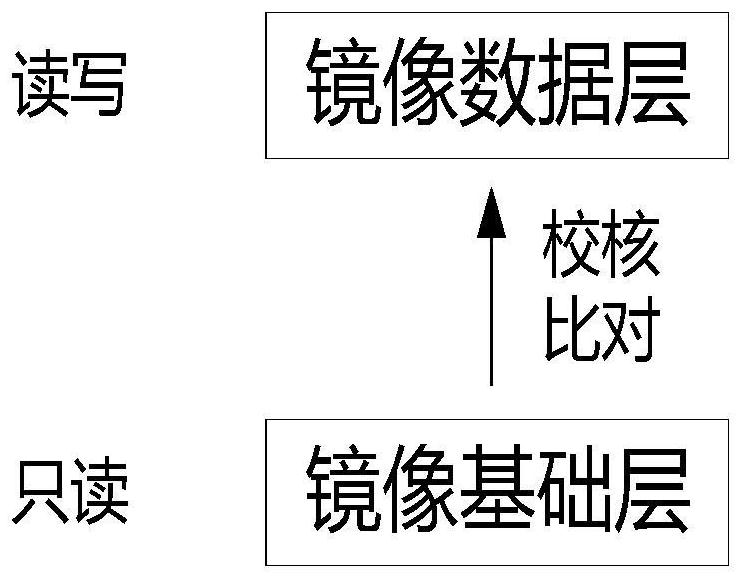
[0053] Container: The container is a series of processes separated from other parts of the system. All files required to run these processes are provided by another image, and the container has portability and consistency. The container can share the same operating syst...
Embodiment 1
[0055] The present invention is based on the container technology, and the isolation environment and the APP are safely reinforced, and customizable containers that meet all APP deployment security requirements are implemented.
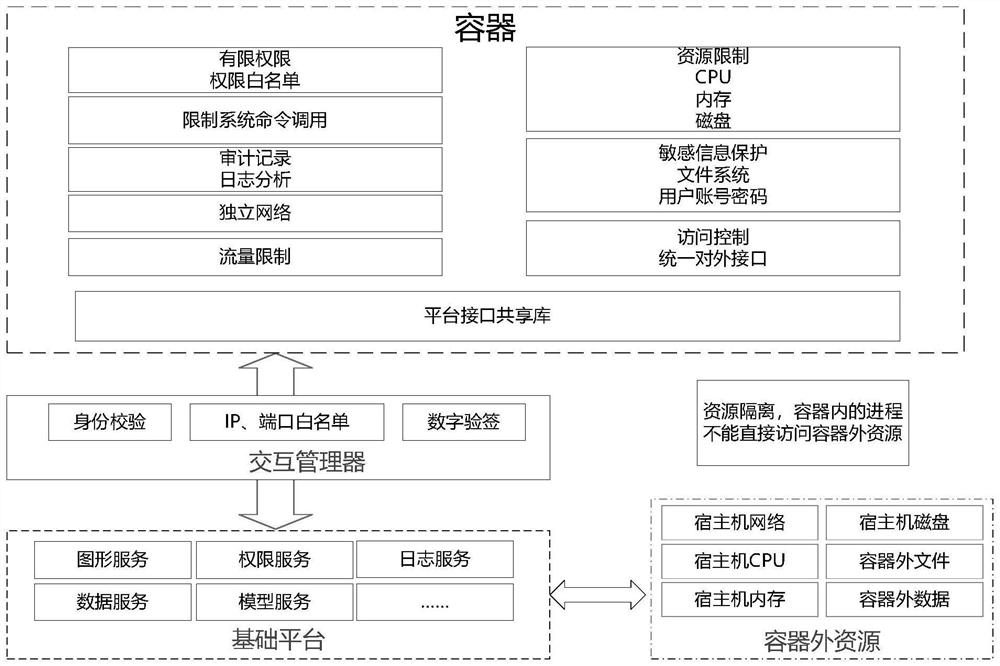
[0056] See figure 1 As shown, in the container safety isolation reinforcement device, the software system on the data communication gateway (the host) is divided into the application layer and the base platform layer in accordance with the service, and the basic platform is deployed on the operating system. Application layer APP is deployed in the container During the container and the foundation platform, communication is connected by interactive manager. Through the container to satisfy the minimum resource from the APP run to an independent environment, the container is unified, and the interaction of the APP and the foundation platform is interactive through the interactive manager. Application layer App will only access resources in the container, an...
Embodiment 2
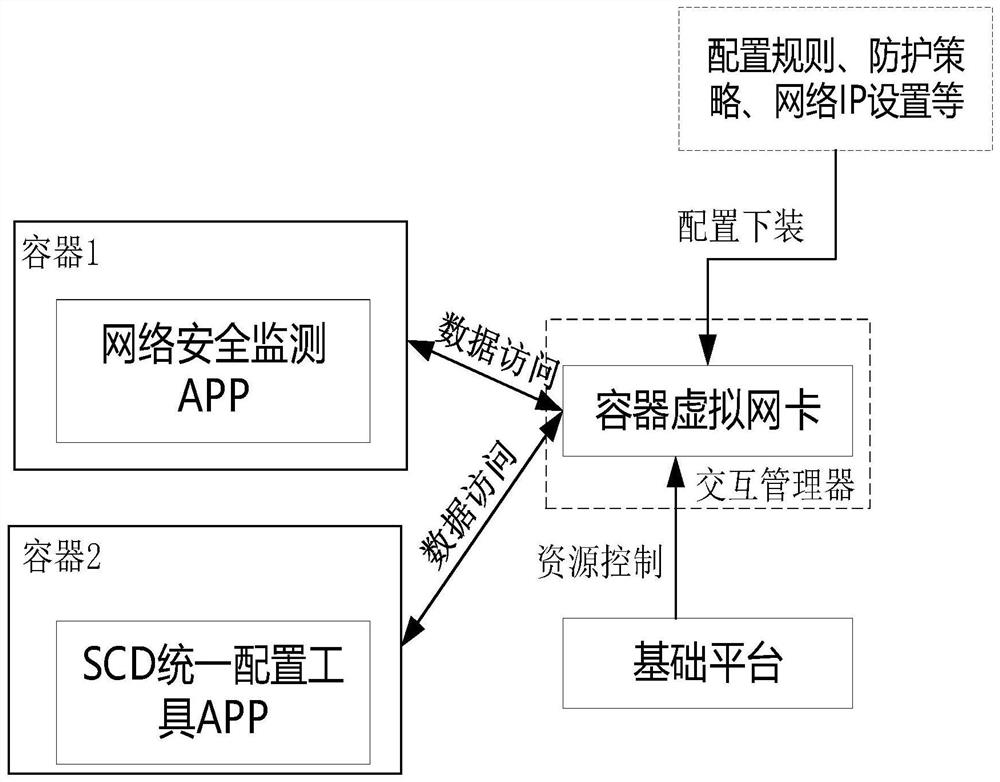
[0069] The present invention provides a container safety isolation reinforcement method, including: Interactive Manager Monitoring the container installed with APP through the interactive manager's resource usage, the resource uses more than the preset alarm threshold. Alarm.
[0070] In the present invention, the resources include: CPU usage, CPU occupancy weight, maximum memory, recommended memory, disk device write bandwidth, disk device read bandwidth, disk device write IO rate, disk device read IO rate , Disk / device read and write weight, network bandwidth, one or more of disk limit.
[0071] In the present invention, the interactive manager filters the commands emitted by the container in accordance with the preset high-risk command list; the high-risk command includes one or more of the IP addresses.
[0072] In the present invention, the interactive manager sets the container virtual network card, and configures the container virtual network card; limit the network to wh...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap