Matching method and device based on tunnel message
A technology of tunnel message and matching method, which is applied in the field of tunnel message-based matching, can solve the problem of low matching analysis efficiency in the inner layer or outer layer of the tunnel, and achieve the effect of flexible detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
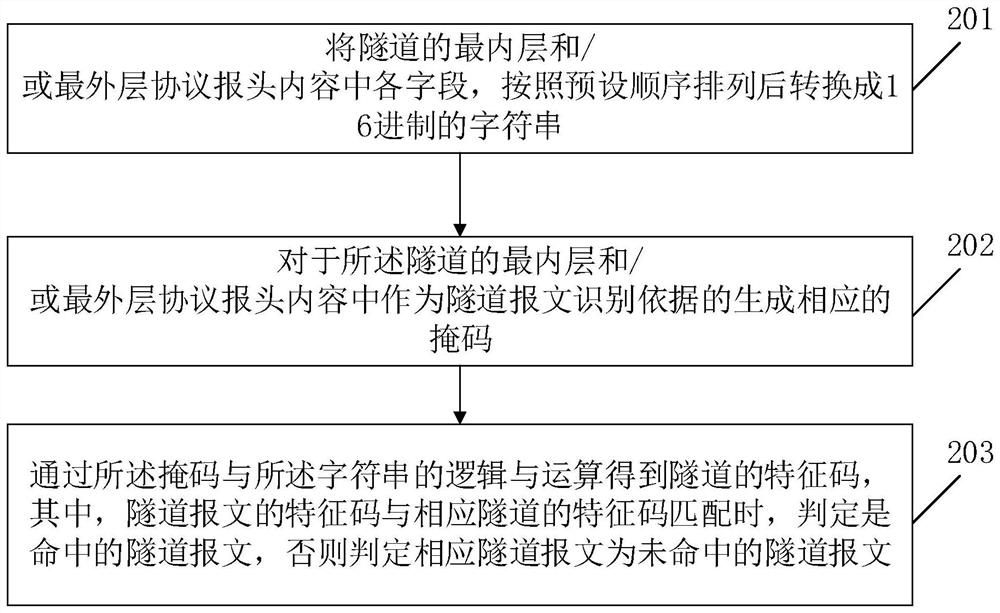
[0041] Embodiment 1 of the present invention provides a matching method based on tunnel packets, which is realized by converting into signature rules, such as figure 1 As shown, the methods include:
[0042] In step 201, the fields in the innermost layer and / or outermost layer protocol header content of the tunnel are arranged in a preset order and converted into a hexadecimal character string.
[0043] In step 202, a corresponding mask is generated for the content of the innermost layer and / or outermost layer protocol header of the tunnel as the basis for identifying the tunnel message.
[0044] In step 203, the characteristic code of the tunnel is obtained through the logical AND operation of the mask and the character string, wherein, when the characteristic code of the tunnel message matches the characteristic code of the corresponding tunnel, it is determined that the tunnel message is a hit, Otherwise, it is determined that the corresponding tunnel packet is a tunnel pa...
Embodiment 2
[0094] The embodiment of the present invention continues the method content of embodiment 1, and by combining Figure 5 The shown example tunnel message content illustrates the realization of the method content of the above steps 201-203.
[0095] Such as Figure 5 As shown, in the corresponding border of the outer layer SIP+DIP: SIP is 10.0.0.1 (converted to 0a 00 0001 in hexadecimal); In the frame is IP protocol 4 (corresponding to 04 in hexadecimal, which is shown as Internet Protocol Version 4 in the figure).
[0096] The content of the border corresponding to the inner SIP+DIP is: SIP is 11.12.13.1 (converted to hexadecimal to 0b 0c 0d01); DIP is 11.12.13.254 (converted to hexadecimal to 0b 0c 0d fe), and the border corresponds to the port number Sport 1024 (convert to 0400 in hexadecimal), Dport 1024 (convert to 0400 in hexadecimal), and the protocol number corresponding to the border is udp 17 (convert to 11 in hexadecimal).
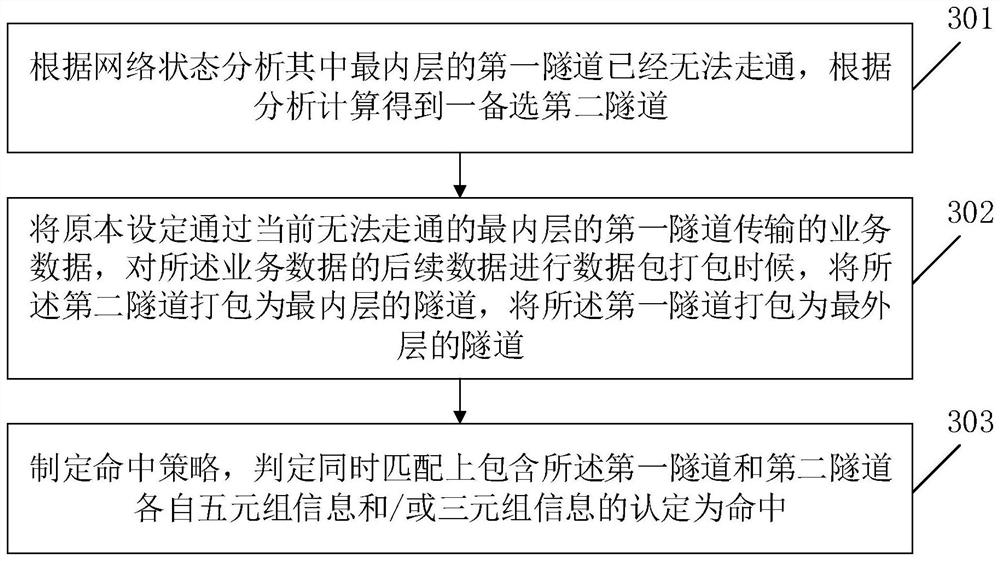
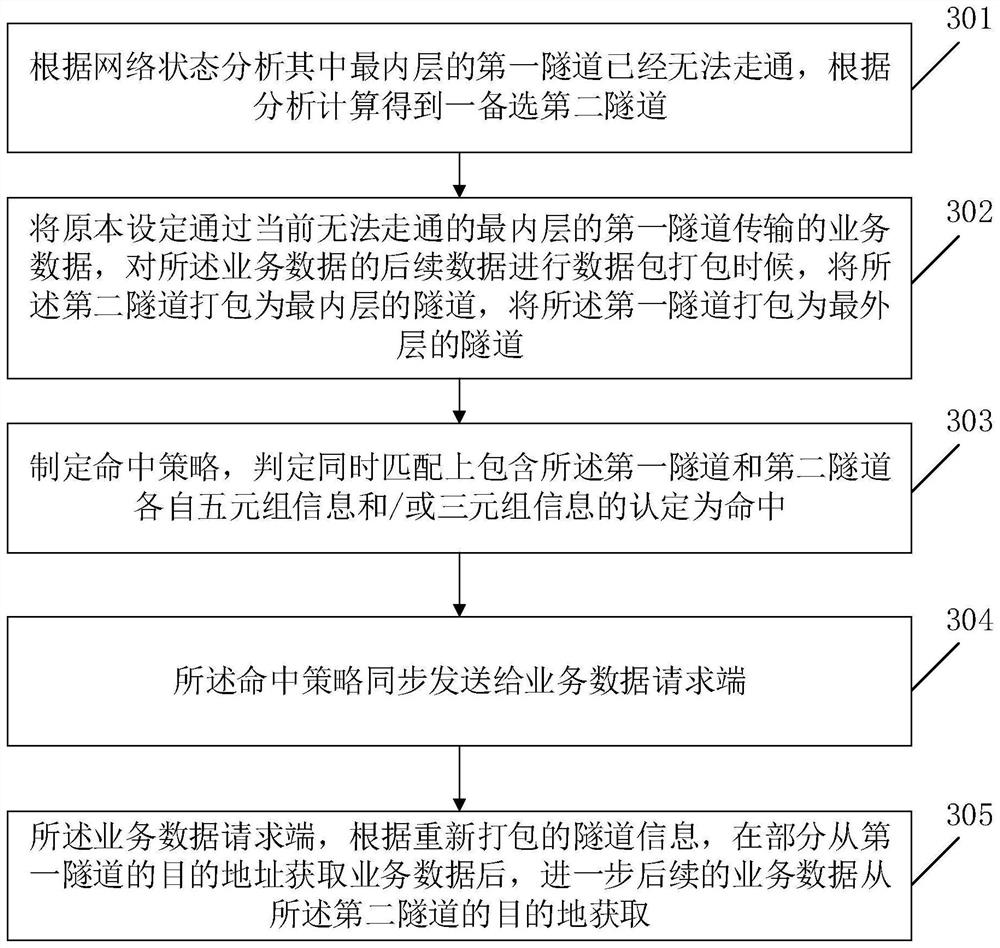
[0097] Internal and external solution 1:...
Embodiment 3
[0122] Such as Figure 6 As shown in FIG. 2 , it is a schematic diagram of the structure of the matching device based on the tunnel message according to the embodiment of the present invention. The apparatus for matching based on tunnel packets in this embodiment includes one or more processors 21 and memory 22 . in, Figure 6 A processor 21 is taken as an example.
[0123] Processor 21 and memory 22 can be connected by bus or other means, Figure 6 Take connection via bus as an example.
[0124] The memory 22, as a non-volatile computer-readable storage medium, can be used to store non-volatile software programs and non-volatile computer-executable programs, such as the matching method based on tunnel packets in Embodiment 1. The processor 21 executes the matching method based on the tunnel message by running the non-volatile software programs and instructions stored in the memory 22 .
[0125] The memory 22 may include a high-speed random access memory, and may also inc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com