Time synchronization safety monitoring method and system based on long short-term memory network
A technology of long and short-term memory and security monitoring, applied in the time-frequency field, can solve the problems of low accuracy and poor anti-interference, and achieve the effect of high accuracy, wide application range, and avoiding false identification of system security status.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0042] Embodiment 1 (deployment after laboratory environment training)
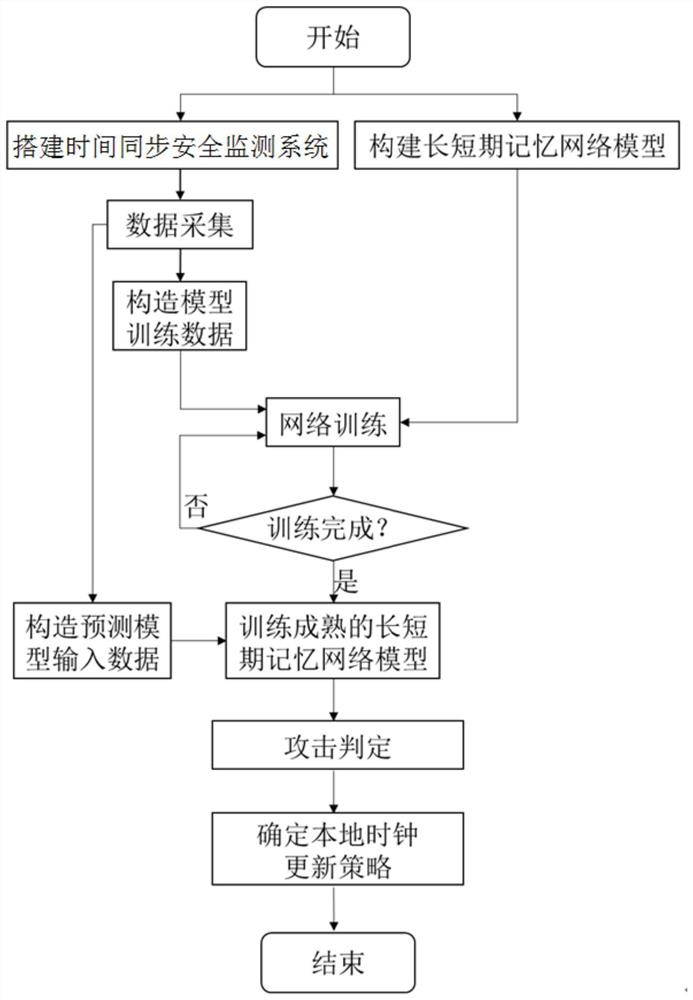
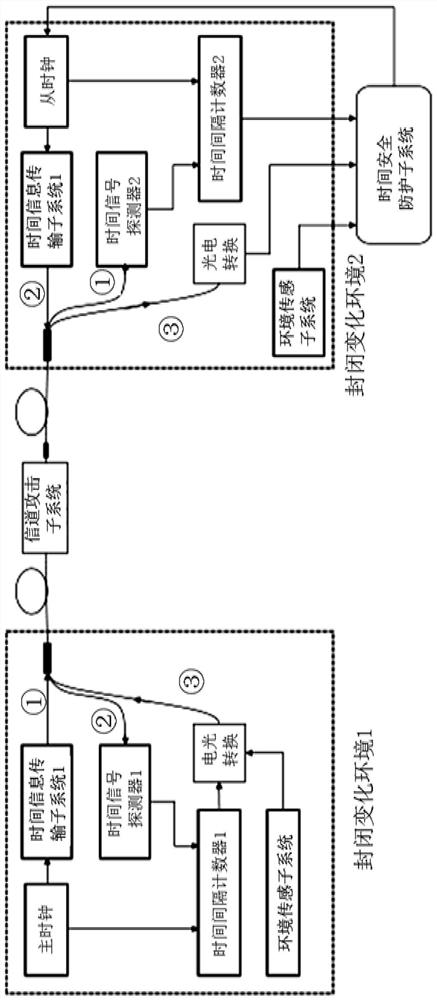
[0043] In order to illustrate the specific implementation manner of the present invention, the detailed description will be given below in conjunction with the accompanying drawings. Build a time synchronization security monitoring system in the experimental environment, such as figure 2 shown. In order to prevent changes in the key characteristics of the system relative to the laboratory environment caused by the deployment process, the accuracy of system attack recognition after the migration of the pre-deployment-trained long-short-term memory network to the post-deployment system is reduced. The system used for training in the laboratory environment is as consistent as possible with the actual deployed system for attack identification. The pre-deployment system is trained, and the trained and mature system is deployed on the spot. After the deployment is completed, the system directly judges the sy...
Embodiment 2
[0068] Embodiment 2 (Training under the real environment after deployment)
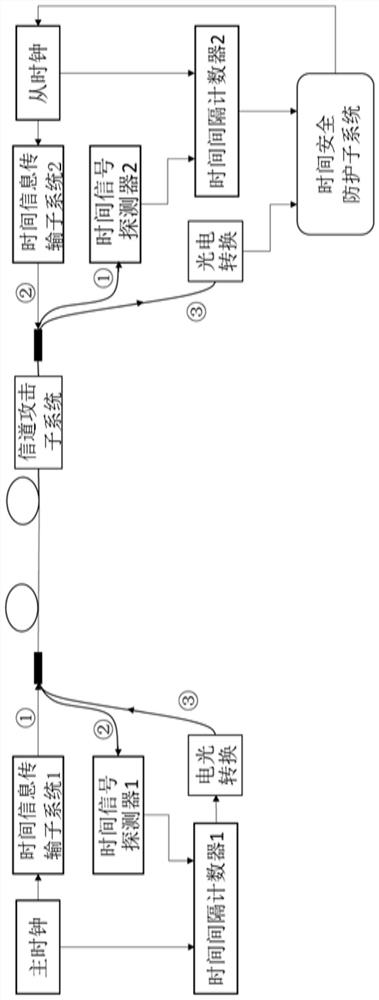
[0069] In order to illustrate the specific implementation manner of the present invention, the detailed description will be given below in conjunction with the accompanying drawings. Deploy a time synchronization security monitoring system for time synchronization attack identification training in the field, such as image 3 shown. After the deployment is completed, the long-short-term memory network is trained according to the data collected after field deployment. A mature system such as Figure 4 As shown, the system security status can be judged according to the data collected on site. System construction and processing methods such as figure 1 shown.
[0070] Step S1: Build a time-synchronized security monitoring system for training after deployment, such as image 3 shown. The time synchronization safety monitoring system includes a master clock, a slave clock, a time information transmis...
Embodiment 3
[0094] Embodiment 3 (environmental training during the experiment first, and then on-site intensive training after deployment)
[0095] In order to illustrate the specific implementation manner of the present invention, the detailed description will be given below in conjunction with the accompanying drawings. First, build a time-synchronized security monitoring system for long-short-term memory network training in a laboratory environment, such as figure 2 As shown, the long-short-term memory network is trained by obtaining data in the laboratory environment; after the training is mature, the time-synchronized security monitoring system is deployed in the field, such as image 3 As shown, according to the data collected in the field, the long-short-term memory network migrated from the laboratory is intensively trained until the network training is mature; after that, the mature time-synchronized security monitoring system is trained on-site, such as Figure 4 As shown, it ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com