User identification method and system based on data burying points
A technology of user identification and identification system, which is applied in the field of user identification method and system based on data embedding, can solve the problems of low quality of user portraits, partial and complete portraits, and difficult collection of behavior data, so as to achieve accurate and efficient user portraits high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
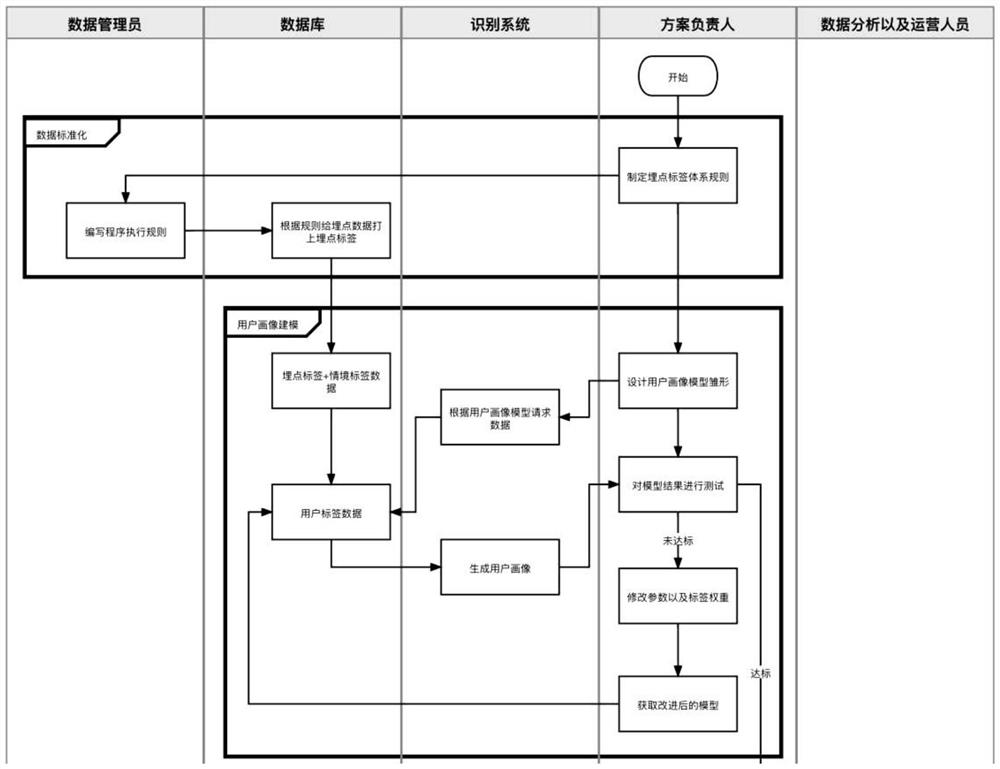
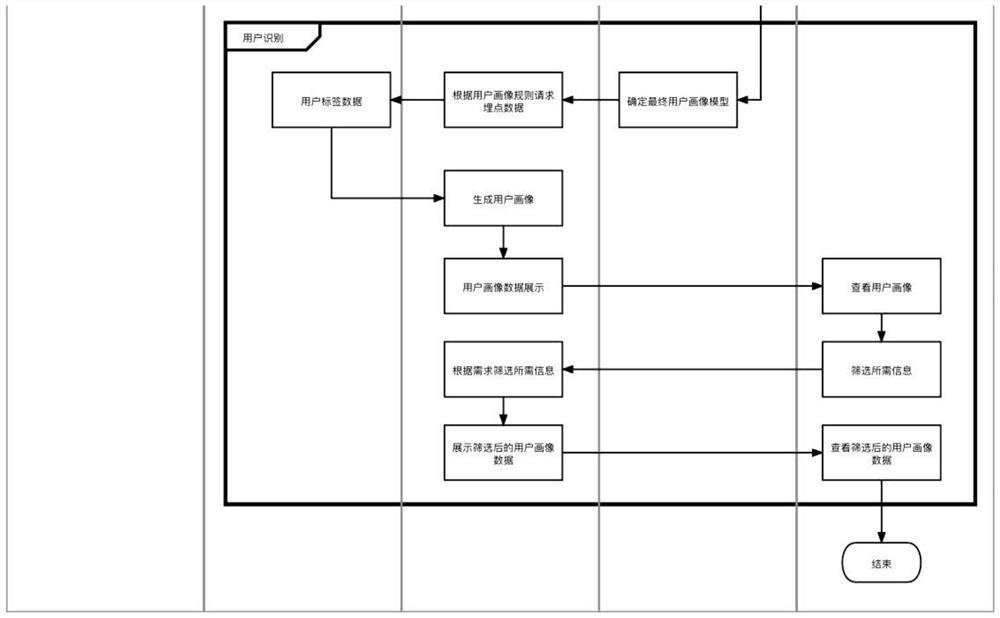
[0050] refer to figure 1 and 2 As shown, this embodiment provides a user identification method based on data buried points, including the following steps:
[0051] S1 initializes, standardizes the buried point data in the database, and stores the newly generated label data into the database;
[0052] S2 receives the rules of the user portrait model, and calculates the embedded point tag data in the database according to the rules, and obtains the user tag sample data;
[0053] S3 tests the user portrait model based on the sample data, and improves the model according to the inspection standard;
[0054] S4 builds a user identification system based on the model in S3, and displays various data of user portraits when user information needs to be obtained.
[0055] This embodiment further provides a data standardization process, standardizes the buried point data in the database according to the buried point label rules, and labels each buried point data of each user id with a c...
Embodiment 2
[0061] In terms of specific implementation, this embodiment provides a data standardization process on the basis of Embodiment 1, specifically as follows:
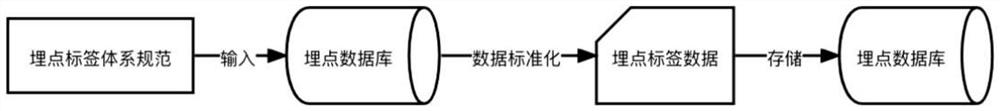
[0062] In this embodiment, the buried point database stores the buried point data entered according to the buried point design, and the buried point data field contains the unique identification field of each user—user id (ip address, micro signal, etc.), and the id is included in the program Information data such as all operation behaviors, operation objects, page addresses, operation creation time, equipment used, location, etc. Then create the buried point label rules through the data standardization process, the specific process is as follows image 3 shown.
[0063] In this embodiment, firstly, the professional person in charge formulates the buried point label specification including various detailed rules, and the specific content of each detailed rule. According to the actual situation, clearly stipulate the corr...
Embodiment 3
[0072] In terms of specific implementation, this embodiment provides a user portrait modeling process on the basis of Embodiment 1. The user portrait modeling process in this embodiment is the process of labeling users as users, and it is also the process of converting buried point labels into The process of user tagging. Can be divided into 4 categories:
[0073] Statistical labels in this embodiment: indicators obtained directly through statistical analysis of data. For example, according to the statistics of the number of "Avalokitesvara" tags, there are 3-5 tags that can be marked as "interested in Avalokitesvara", 6-10 tags that can be marked as "very interested in Avalokitesvara", and 10 or more of this tag can be marked as "very interested in Guanyin Bodhisattva".
[0074] In this embodiment, the rule-type tag: convert the buried point tag according to the business rule. If you have more than 20 history-related tags such as "Historical Articles", "Zhu Yuanzhang", and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com