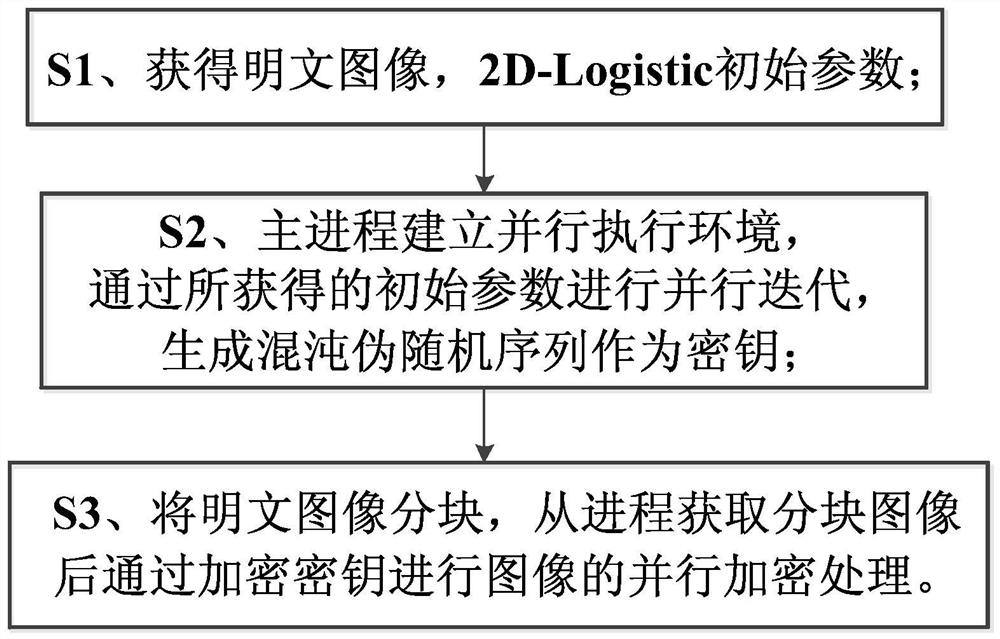
Hyperchaos-based parallel encryption method for images in network office official document
An encryption method and ultra-chaotic technology, applied in the field of new parallel digital image encryption, can solve problems such as hidden dangers of multimedia data security, and achieve the effects of improving plaintext sensitivity, enhancing sensitivity, and increasing computing speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
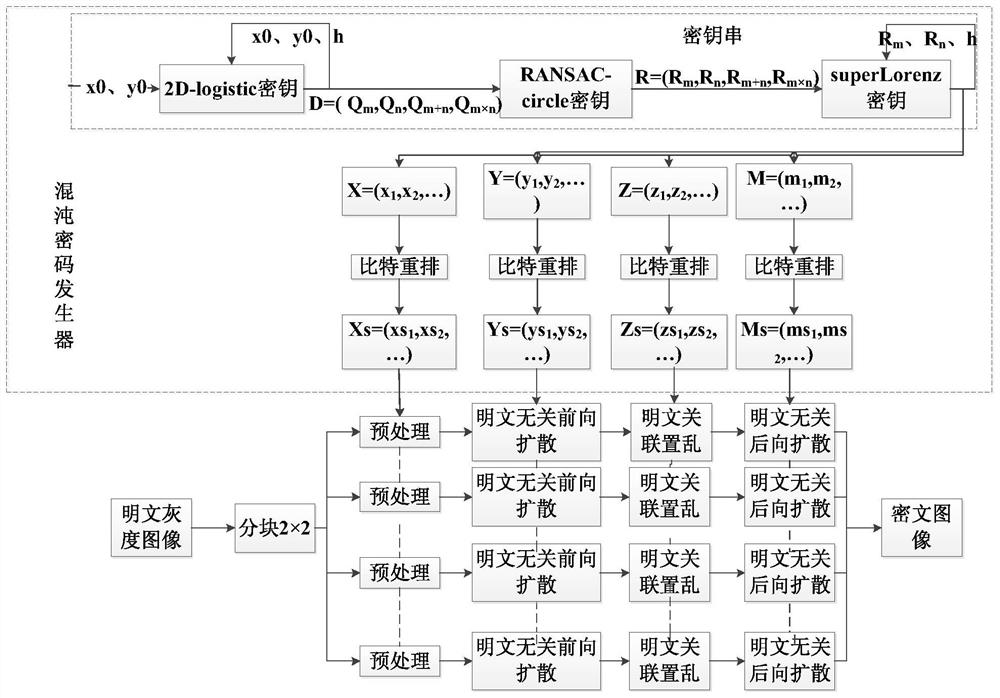
[0137] Example 1, constructing a chaotic password generator
[0138] The overall encryption process requires a pseudo-random chaotic sequence generated by a chaotic cipher generator for scrambling and diffusion operations in the encryption process. The chaotic cipher generator is constructed from a "key string", and the "key string" is composed of three groups of mutually iterative "keys": 2D-Logistic key, RANSAC-circle key, superLorenz key. The four sequences generated by the chaotic cipher generator are used for preprocessing, scrambling, diffusion and other operations in the encryption process;
[0139] Use P to represent the sample electronic document image. If the length and width are not divisible, it will be corrected with a pixel value of 0. The corrected image size is 800×800. The key generation steps are as follows:
[0140] Func1.1, 2D-Logistic key
[0141] The key is based on a two-dimensional Logistic (ie, 2D-Logistic) map and serves as the initial iteration key...
example 2
[0177] Example 2. Digital image encryption
[0178] First, the network electronic document image P is divided into block images in units of 2×2, and put into a parallel pool for parallel encryption operations. If the length and width are not divisible by an integer, it will be corrected with a pixel value of 0, and the corrected size will be 640,000. Taking the first image P1 as an example, preprocess P1 to obtain a preprocessed image P', and then perform plaintext-independent forward diffusion, plaintext correlation scrambling, and plaintext-independent backward diffusion on each image in parallel, and finally obtain electronic Official document ciphertext image C.
[0179] Its specific steps are described as:
[0180] Func2.1, digital image preprocessing
[0181] The specific steps are described as:
[0182] The plaintext block image P1 and the random matrix X(400,400) are subjected to bit-level bit XOR processing to obtain the preprocessed image P';
[0183] Func2.2, pl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com