Distributed user authentication system and authentication method suitable for low earth orbit satellite network
A low-orbit satellite, user authentication technology, applied in the field of satellite communications, to reduce complexity, reduce communication delay, and improve the efficiency of inter-satellite communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0094] Example 1, user registration (non-mobile scenario):
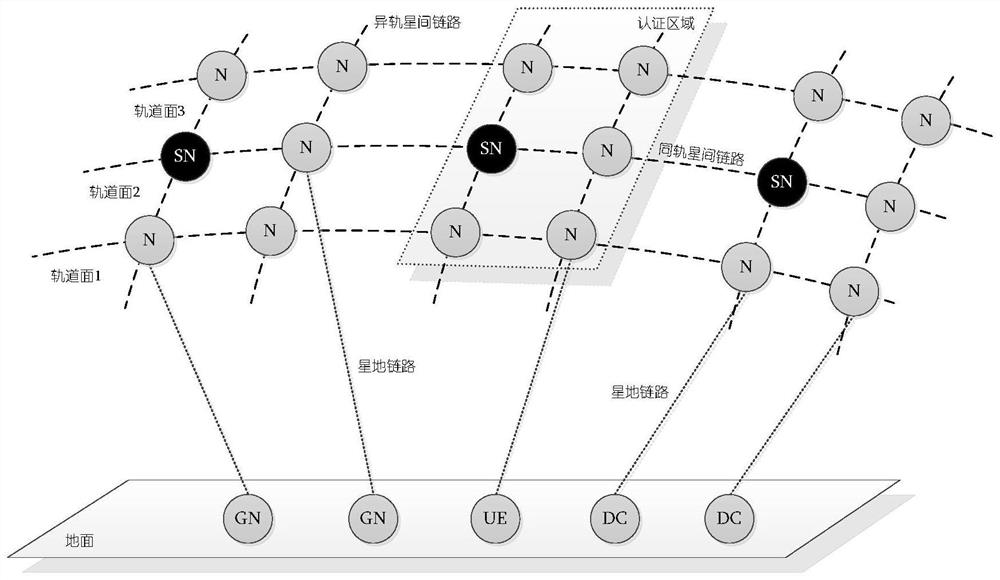
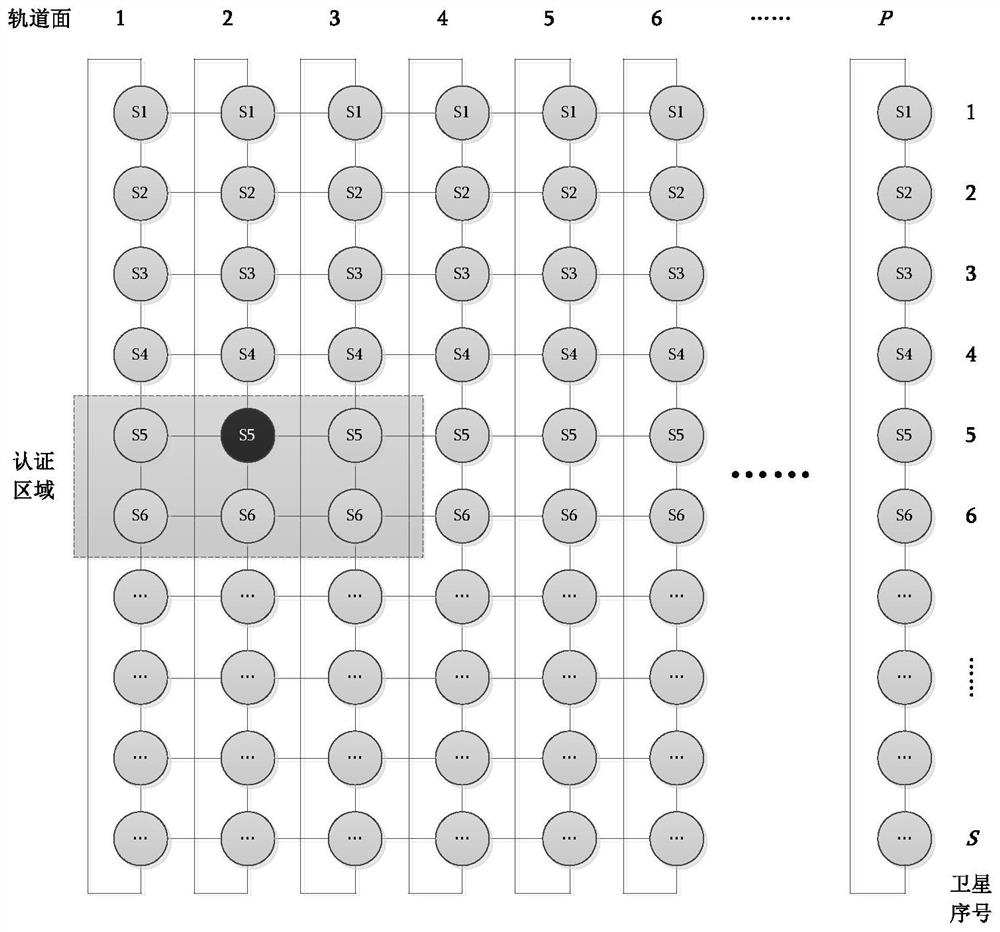
[0095] Design topology such as figure 1 , figure 2 As shown, and take 12 LEO orbital planes, each orbital plane 10 satellites deployment. An illegal user sends a message to a certain GN on the ground figure 2 The S6 satellite in the middle orbital plane 2 initiates a registration request, and the SN in the certification area to which the satellite belongs is the S5 satellite in the orbital plane 2. The user registration process is as follows:
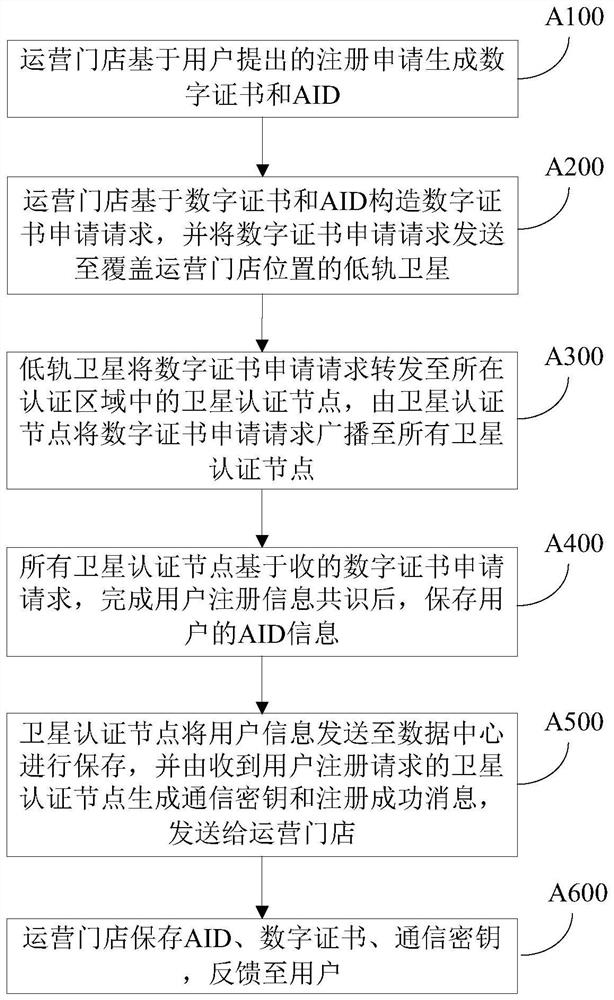
[0096] 1. The user brings his ID card and organization certificate to the GN on the ground to apply for registration, and the GN will manually verify the validity of his certificate (valid by default). Fill in the certificate information in the registration module of the GN registration machine. The built-in algorithm of the registration module automatically generates digital certificates and AIDs. The AID generated this time is shown in Table 1.
[0097] Table 1: AID...
example 2
[0113] Example 2, user registration (mobile scenario):
[0114] Design topology such as figure 1 , figure 2 As shown, the deployment method adopted is the same as that of Example 1. An illegal user sends a message to a certain GN on the ground figure 2 The S6 satellite in the middle orbital plane 2 initiates a registration request, and the SN in the certification area to which the satellite belongs is the S5 satellite in the orbital plane 2. The user registration process is as follows:
[0115] 1. The user brings his ID card and organization certificate to the GN on the ground to apply for registration, and the GN will manually verify the validity of his certificate (valid here by default). Fill in the certificate information in the registration module of the GN registration machine. The built-in algorithm of the registration module automatically generates digital certificates and AIDs. The AID generated this time is shown in Table 6.
[0116] Table 6: AID example
...
example 3
[0136] Example 3, user login:
[0137] The network topology design is the same as that of Example 1. Take the legal user UE (AID=0000:0000:0000:0000:0000:0000:0000:0081) to initiate a login request to the S6 satellite on orbital plane 2 on any user computer with an authentication client installed:
[0138] 1. The user inserts the Ukey into the computer and opens the authentication client program. The program automatically recognizes the Ukey and reads the AID information in it.
[0139] 2. The authentication client program sends a login request to the S6 satellite on orbital plane 2, and the request includes the user's AID information, as shown in Table 12.
[0140] Table 12: Sample Login Request Message
[0141] type 3 (3 means login request message) AID 0000:0000:0000:0000:0000:0000:0000:0081 Timestamp T2
[0142] 3. The S6 satellite on the orbital plane 2 forwards the login request message to the S5 satellite on the orbital plane 2 (the SN of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com