SDC vulnerability prediction method based on instruction feature importance
A technology of command features and prediction methods, which is applied in the direction of instruments, calculations, character and pattern recognition, etc., can solve the problems of large time cost, reduce memory consumption, and improve prediction accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] In order to make the purpose, technical solution and advantages of the present application clearer, the present application will be further described in detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the specific embodiments described here are only used to explain the present application, and are not intended to limit the present application.
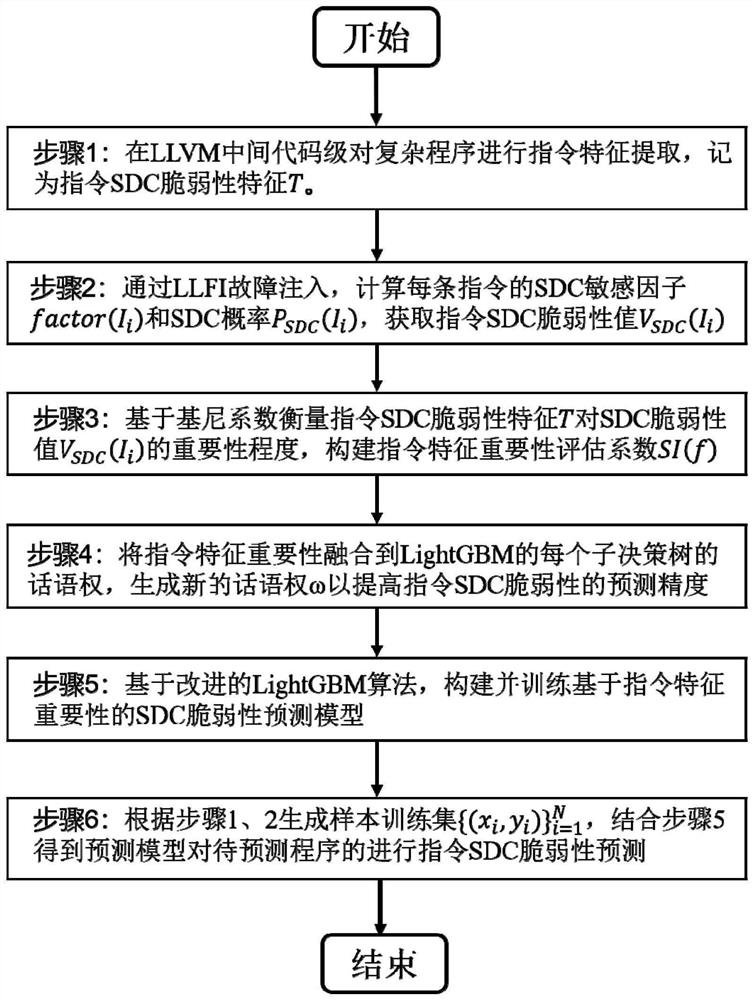
[0043] In one embodiment, combined with figure 1 , providing a method for predicting SDC vulnerability based on the importance of instruction features, the method comprising the following steps:
[0044] Step 1, perform instruction feature extraction on the complex program at the LLVM intermediate code level, and generate the instruction SDC vulnerability feature T;
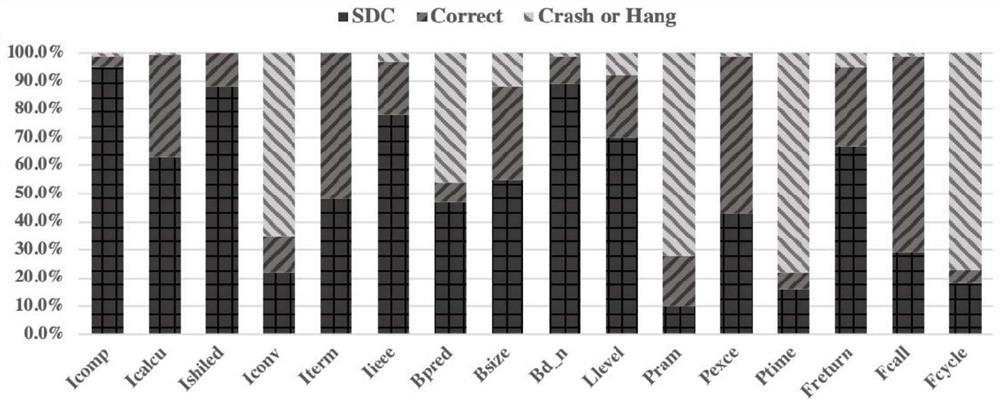
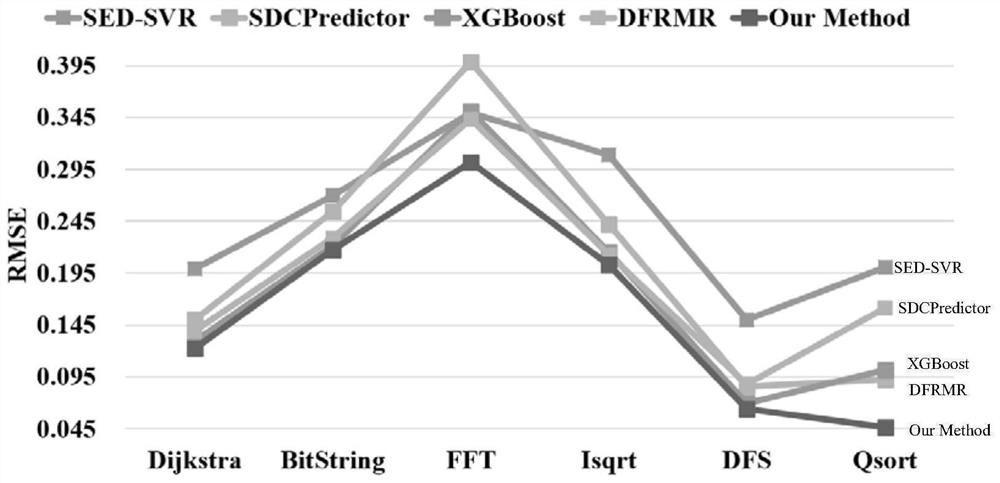
[0045] Step 2, use the LLFI fault injection tool to simulate unit flipping to randomly inject faults into complex programs, and calculate the SDC sensitivity factor factor(I i ) and SDC probability P SDC (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com