Two-stage DDoS attack detection and defense method in software defined network
A software-defined network and attack detection technology, applied in the field of network security, can solve the problems of switches discarding normal data packets, less overhead, exhaustion of controller resources, etc., and achieve good classification effects, load reduction, and high real-time effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
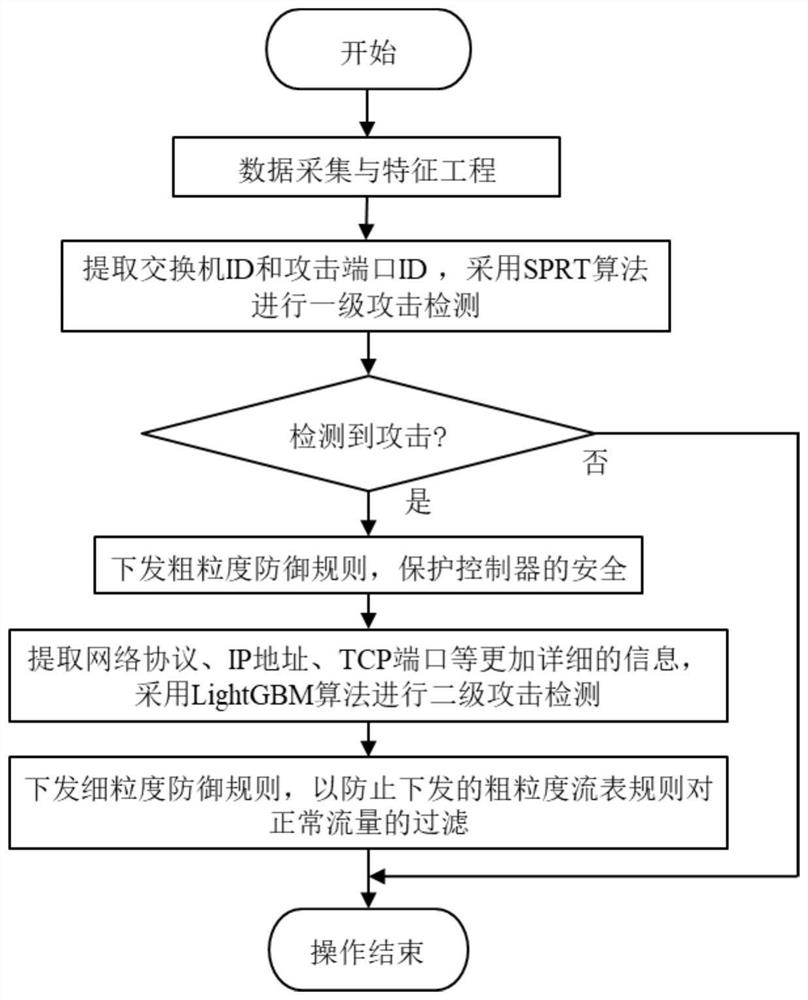
[0054] A two-level DDoS attack detection and defense method in a software-defined network, such as figure 1 shown, including the following steps:
[0055] S1. Collect switch flow table data, and extract direct features and derived features;
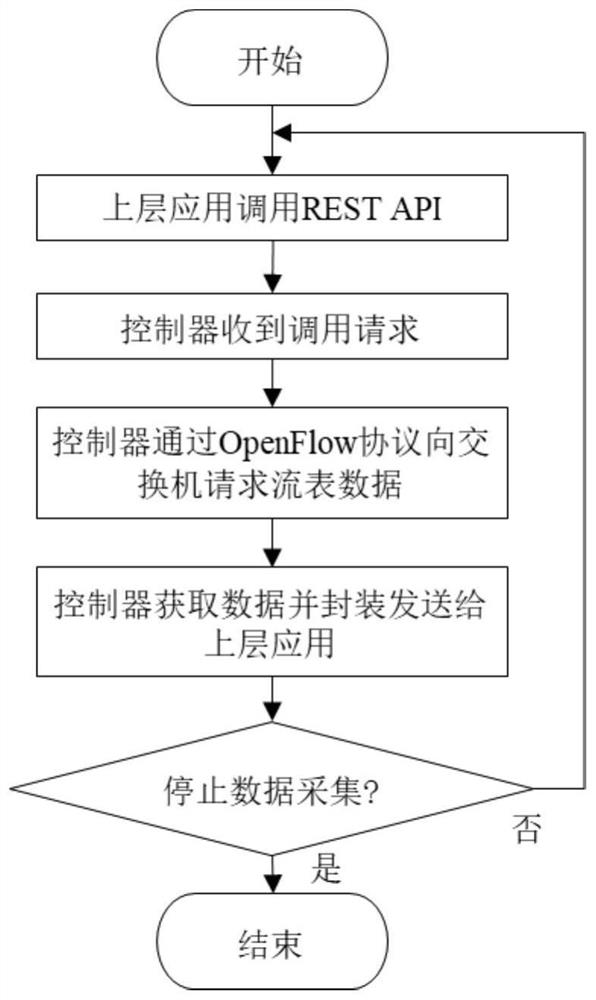
[0056] Specifically, every preset period (in this embodiment, the preset period is 5 seconds), the flow table information of the switch is collected through the northbound interface of the controller, and the flow table data collection flow chart based on the northbound interface is as follows figure 2 As shown, and extract the direct features of the flow table and the derived features of the flow table, and then perform missing value processing, One-Hot encoding, and data standardization preprocessing operations on the extracted features, specifically:
[0057] The collected flow table data types include normal traffic types and three types of attack traffic types: DDoS attack type, Probe attack type, and R2L attack type;
[0058] The...
Embodiment 2
[0084] The present invention provides a two-level DDoS attack detection and defense system in a software-defined network, including:
[0085] The collection and extraction module is used to collect switch flow table data, and extract direct features and derived features;
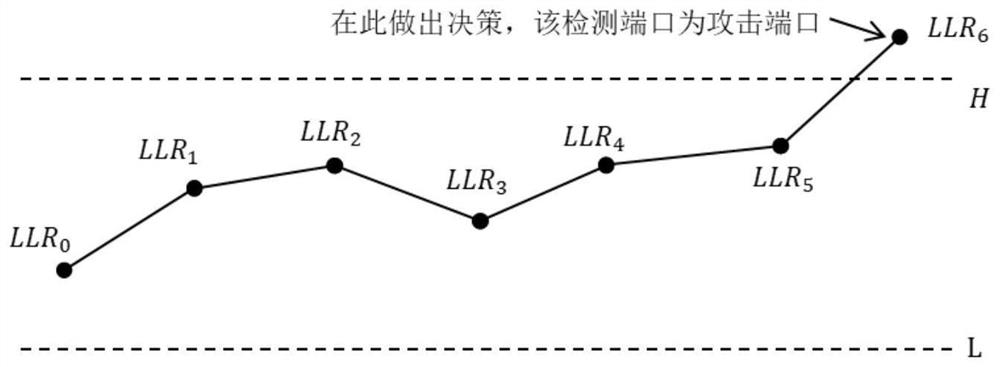
[0086] The first-level detection module is used to calculate the direct feature and the derived feature by using a statistical algorithm. If an attack is detected, perform the operation of the first-level defense module; otherwise, end the operation;
[0087] The first-level defense module is used to encapsulate the detected attack port to generate a coarse-grained flow table defense rule, and discard the data packet on the attack port to protect the security of the controller;
[0088] The secondary detection module is used to calculate the direct feature and the derived feature by using a classification algorithm to determine the type of attack;
[0089] The secondary defense module is configured to gener...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com