Grid network security analysis method and system based on graph database
A network security analysis and network security technology, applied in the field of computer information processing, can solve problems such as being less than ideal in actively and effectively responding to various security incidents, and limiting the ability of network security administrators to make optimal response decisions. The effect of improving attack link traceability and high deployment flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
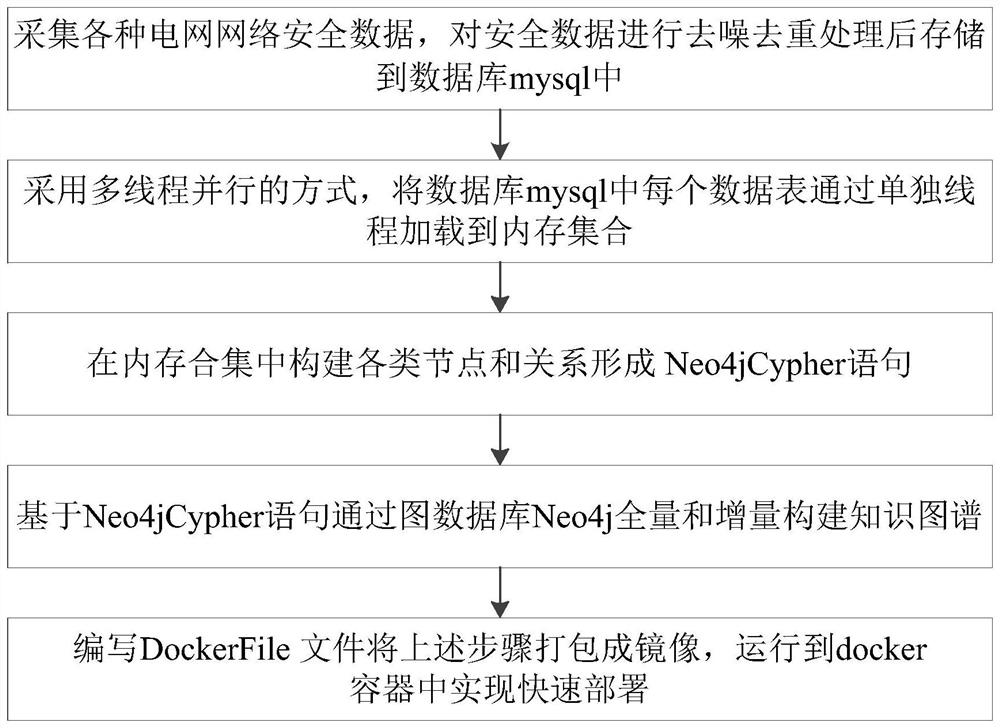
[0036] like Figure 1-2 As shown, the present invention provides a grid network security analysis method based on a graph database, comprising the following steps:
[0037] S1. Collect various power grid network security data, perform denoising and deduplication processing on the security data, and store them in the database mysql;
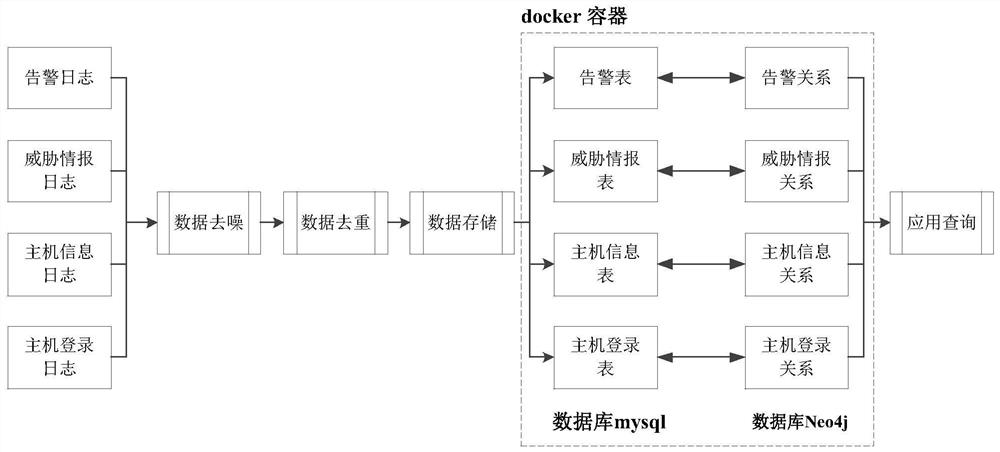
[0038] S101. Collecting various power grid network security data includes acquiring alarm logs, host login logs, host information logs, and threat intelligence logs through webservice and UDP.
[0039] The alarm log includes the attack source, the attacked target, the system it belongs to, the operation and maintenance unit, and geographic information; the threat intelligence log includes the threat intelligence data; the host information log includes the operating system and the mac address; the host login log includes the host login data.
[0040] S102, performing deduplication and denoising processing on the security data includes:
[0041] D...
Embodiment 2
[0155] The embodiment of the present invention provides a grid network security analysis system based on a graph database, the system includes:
[0156]The data preparation module is used to collect various power grid network security data, denoise and deduplicate the security data and store it in the database mysql;
[0157] The data loading module is used to load each data table in the database mysql into the memory collection through a separate thread in a multi-threaded parallel manner;
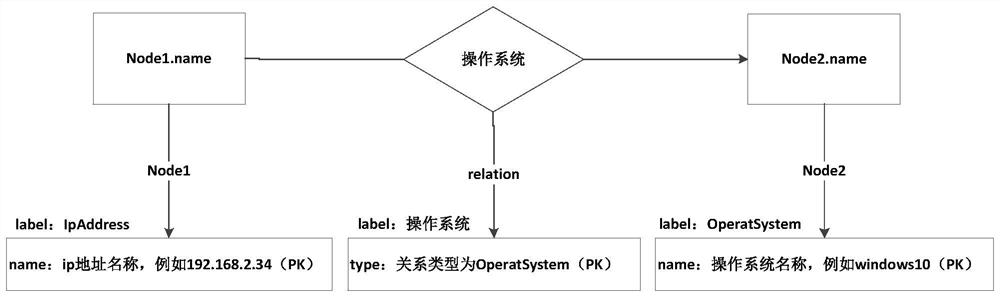
[0158] The relationship graph module is used to construct various nodes and relationships in the memory collection to form Neo4jCypher statements;
[0159] The knowledge graph module is used to build a knowledge graph in full and incrementally through the graph database based on Neo4jCypher statements;
[0160] The method deployment module is used to write a DockerFile file to package the above steps into an image, and run it into a docker container to achieve rapid deployment.
[0161]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com