Hardware module-based authentication in intra-vehicle networks
a hardware module and intra-vehicle network technology, applied in data switching networks, digital transmission, transportation and packaging, etc., can solve the problem of destroying malicious messages before they are fully received, reduce the overhead of key management, and improve the security of in-car network communications.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
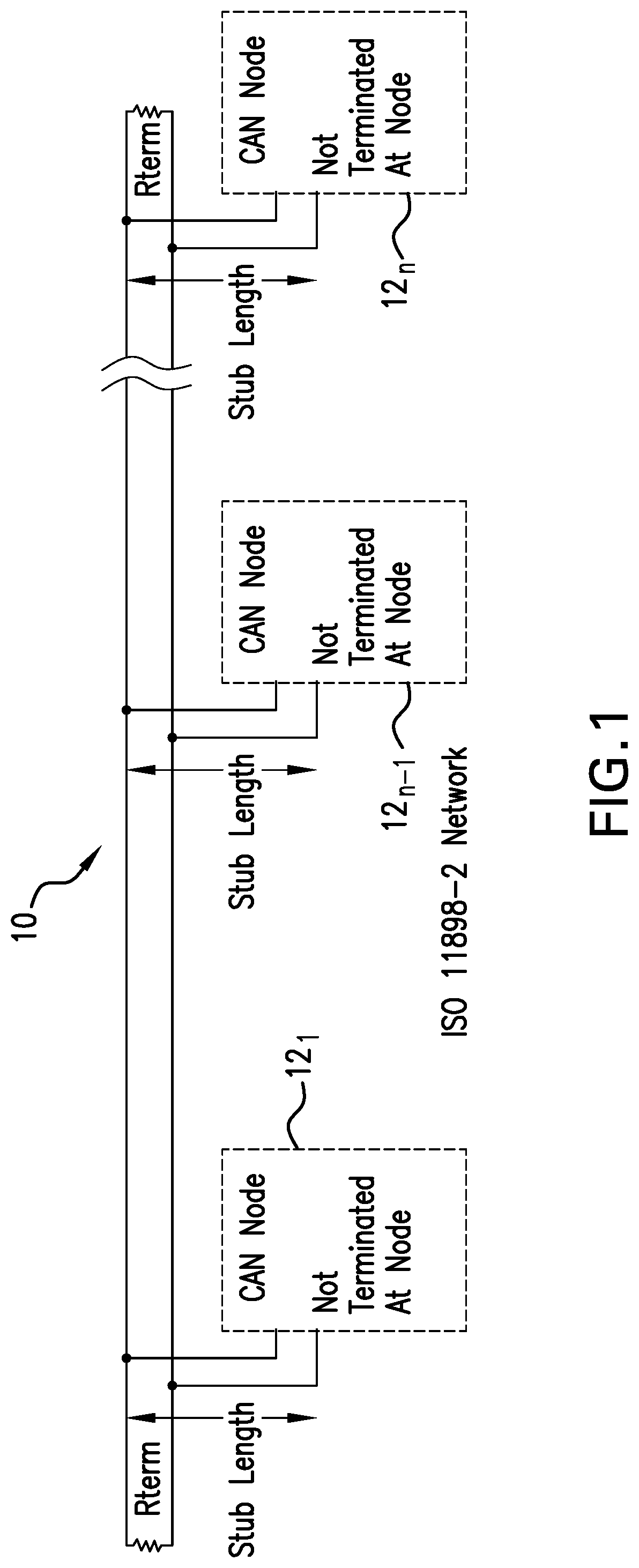
[0040]CAN is a multi-master serial bus standard for connecting ECUs, also known as nodes. All nodes are connected to each other through a two wire bus. ISO-11898-2, also called high speed CAN, is the standard implemented in modern automobiles. Modern automobiles may have as many as 70 ECUs for various subsystems, such as the engine control unit, transmission, airbags, antilock braking system (ABS), cruise control, power steering, audio systems, and so forth. FIG. 1 illustrates the architecture of the high speed CAN which comprises a two wire bus, or CAN bus, 10 terminated at each end by 120Ω resistors. A plurality of ECUs, or nodes, 121 to 12n are connected to the CAN bus 10. The bus standard allows the ECUS to communicate with each other without a host computer. The comminations are a message-based protocol rather than an address based protocol.
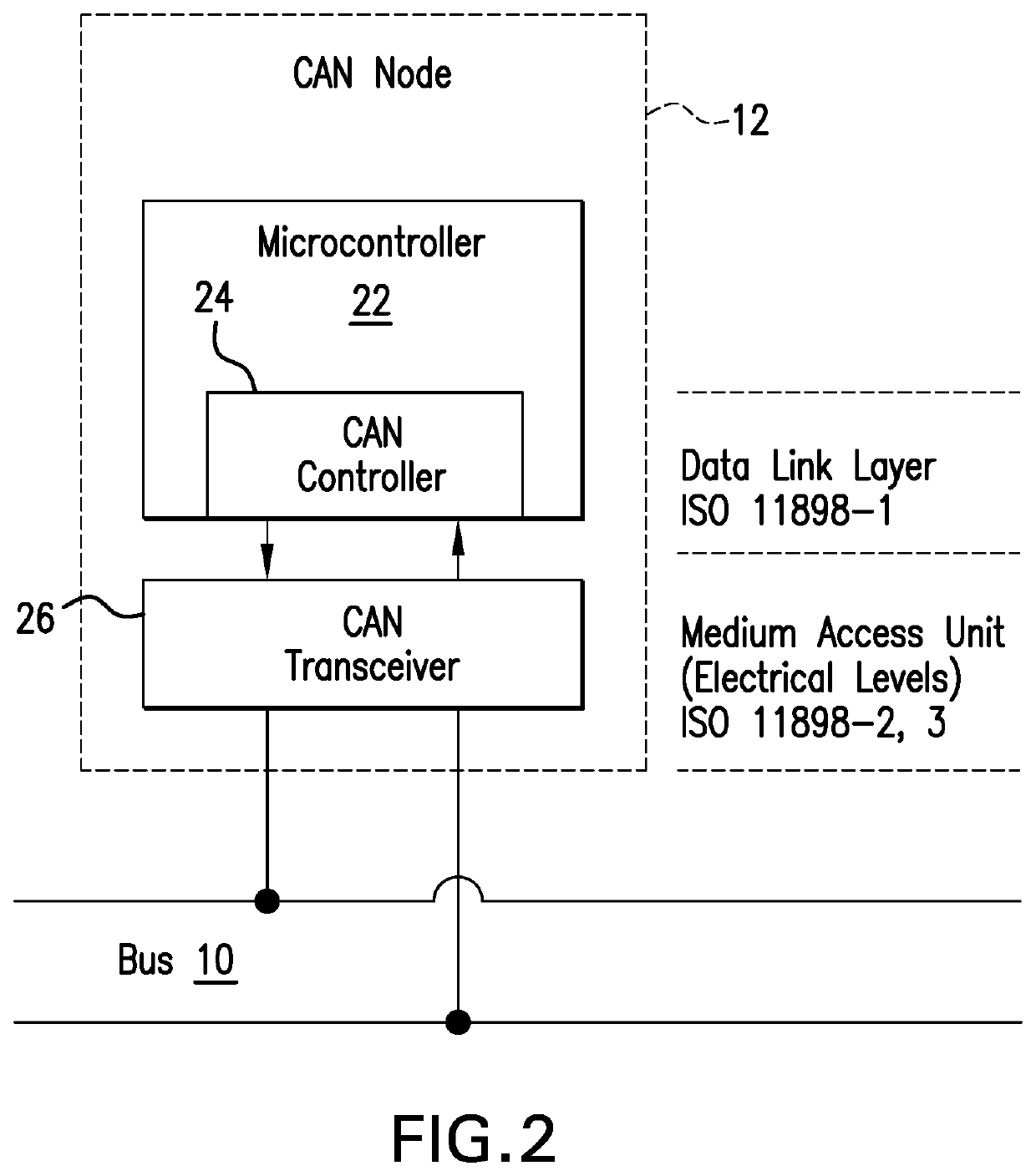
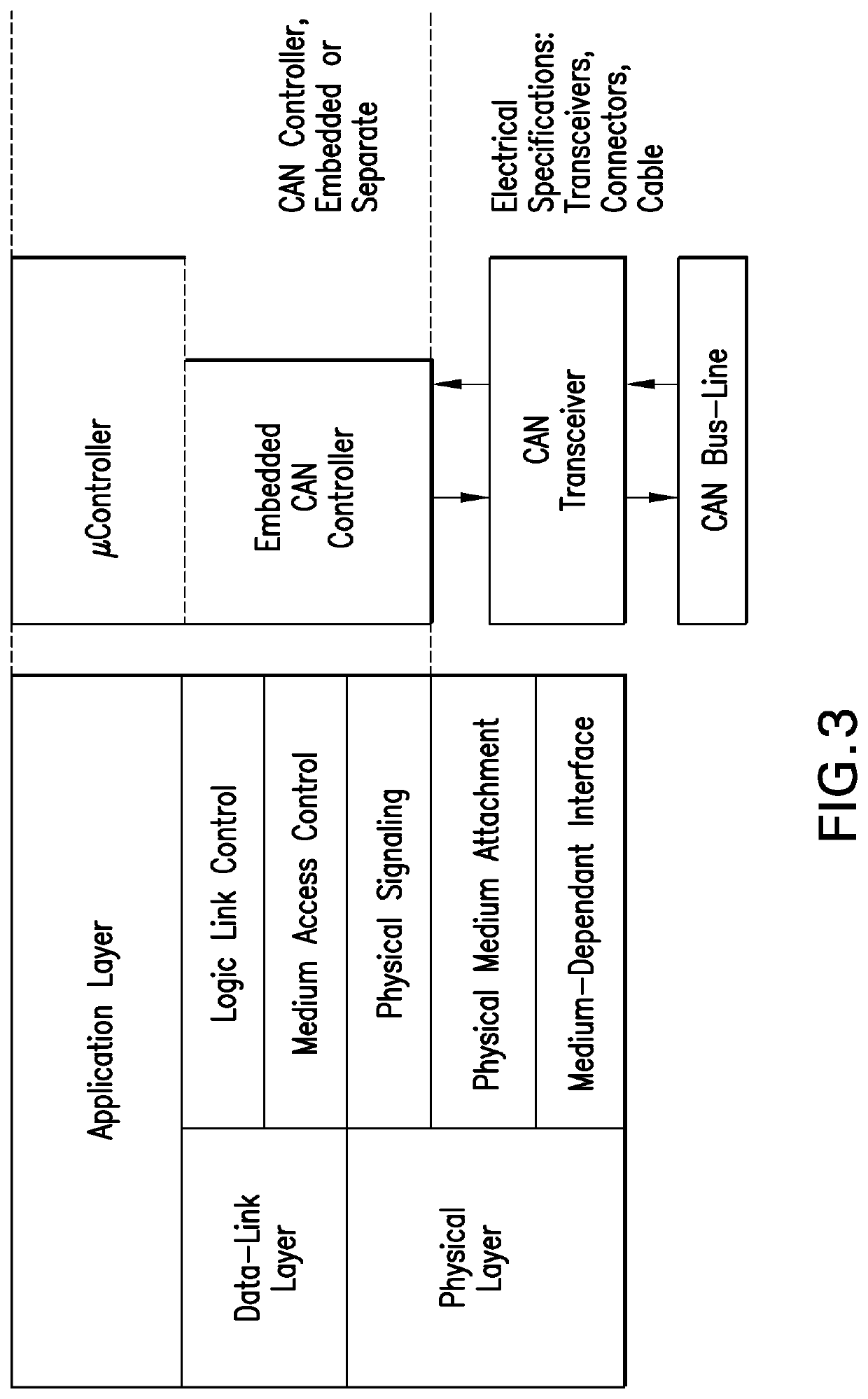
[0041]FIG. 2 illustrates a CAN node or ECU. Generally, each ECU 20 comprises a central processor 22, typically a microcontroller, a CAN con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com