Architecture of an encryption circuit implementing various types of encryption algorithms simultaneously without a loss of performance
a technology of encryption circuit and architecture, applied in the field of encryption, can solve the problems of high development cost of a solution that remains, and the lack of architectures that are capable of executing a set of algorithms, and achieve the effect of fast execution of the principal encryption algorithms, without loss of performan
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] For simplicity's sake, the encryption / decryption module will hereinafter be called the “encryption module.”
[0020] The links between each module are all two-way links unless indicated.
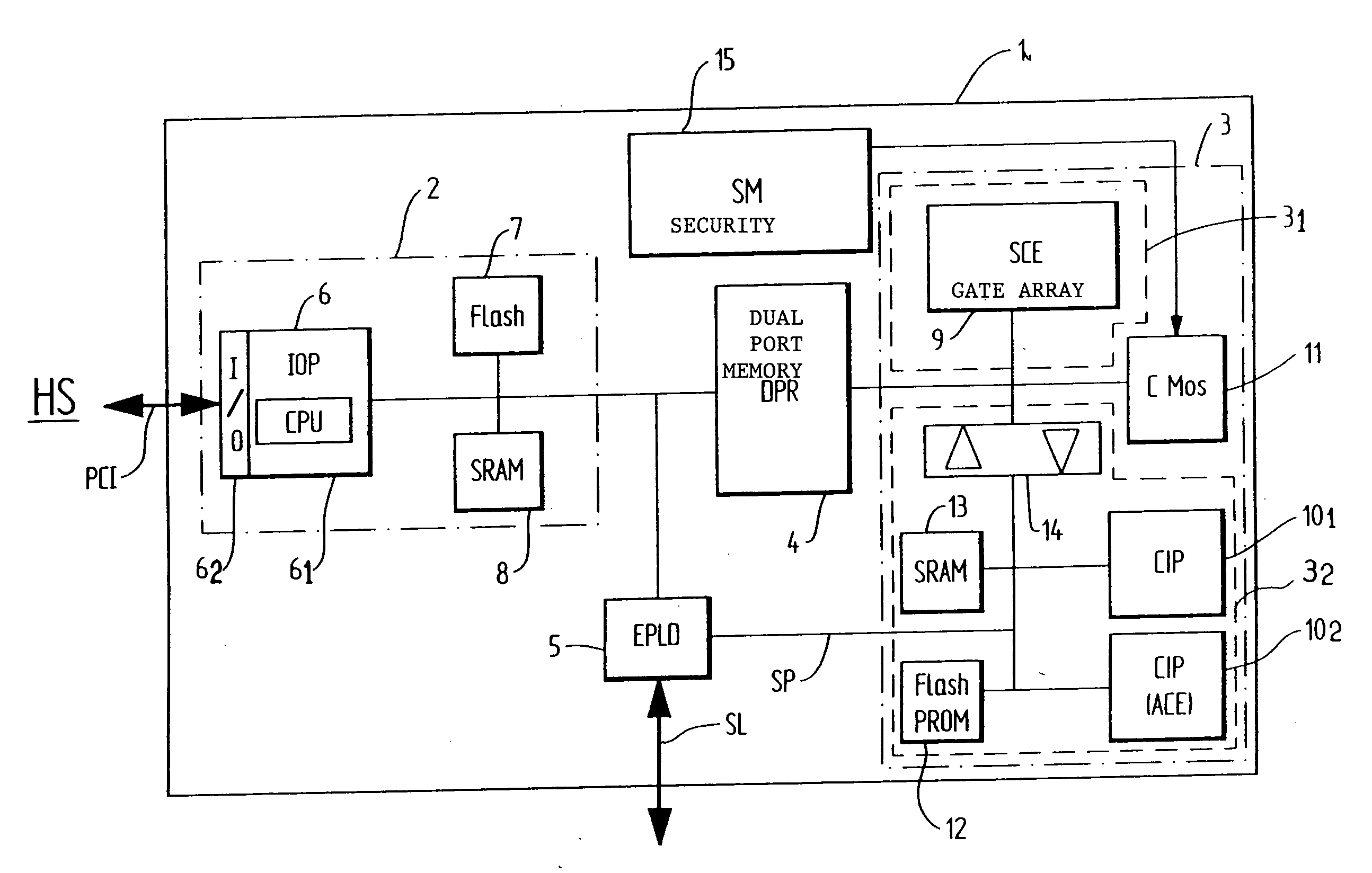
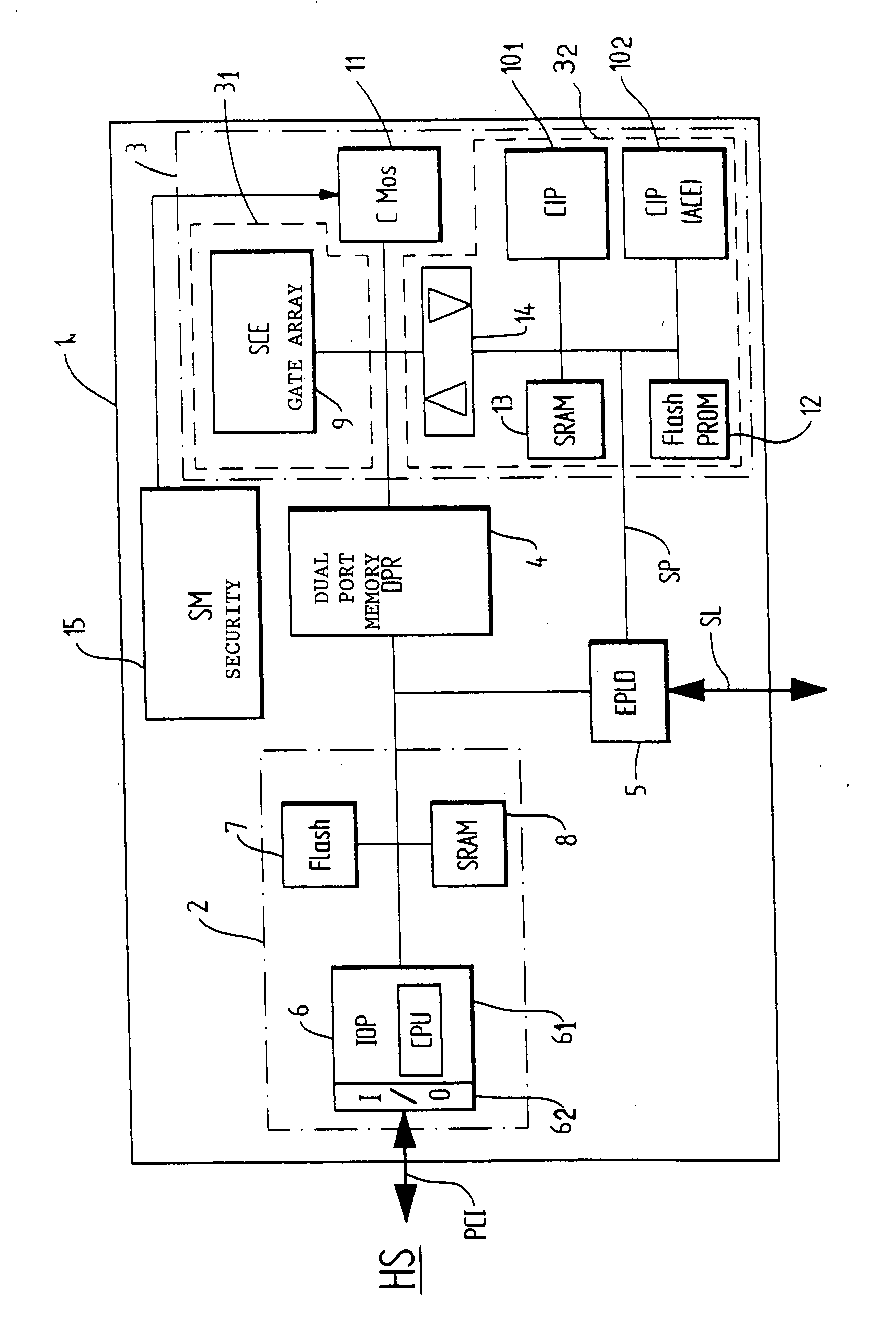
[0021] The encryption circuit 1 according to the invention hinges on two main modules: [0022] an input / output module 2 responsible for the data exchanges between the encryption resources and a host system HS via a PCI bus; and [0023] an encryption module 3 in charge of the encryption and decryption operations as well as the storage of the secrets.
[0024] These two modules 2 and 3, respectively delimited by an enclosing dot-and-dash line, dialogue via a dual-port memory DPR 4 that allows the exchange of data and commands / statuses between the two modules 2 and 3.
[0025] A serial link SL controlled by the encryption module 3 also makes it possible to input the basic keys through a secure path SP independent of the normal functional path (PCI bus), thus meeting the requirement imposed by the FIPS 14...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com